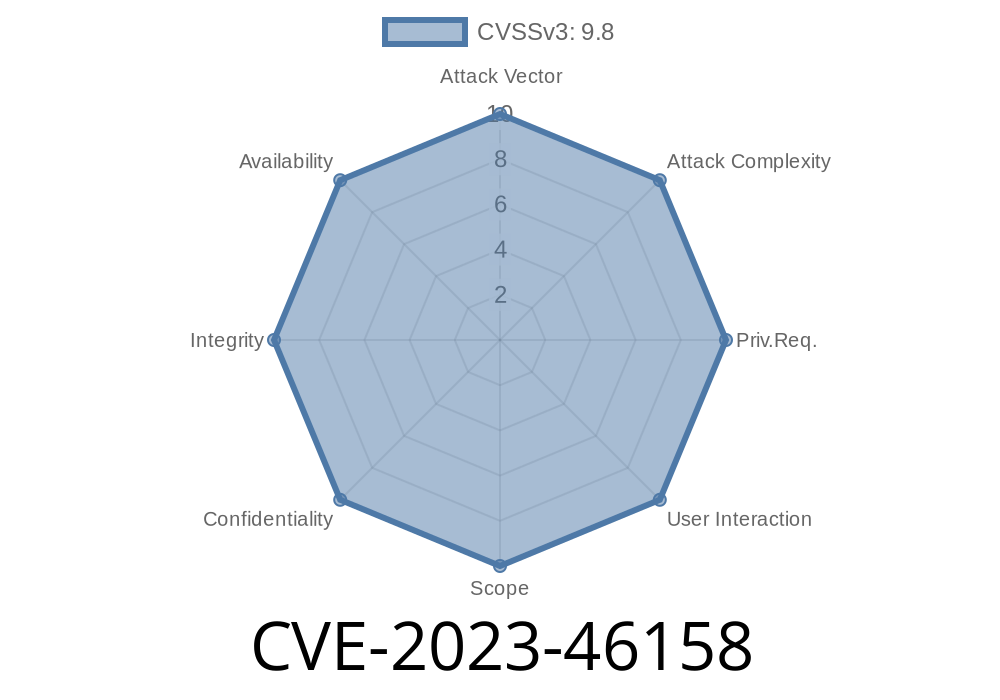
IBM WebSphere Application Server Liberty is a popular lightweight app server loved by Java developers and enterprises. But sometimes, even the most trusted software can have flaws. In September 2023, a new vulnerability was reported—now tracked as CVE-2023-46158—that affects certain versions of WebSphere Liberty, exposing applications to weakened security.
References and useful resources
Read on—especially if you run IBM WebSphere Liberty 23...9 through 23...10!
What is CVE-2023-46158?
CVE-2023-46158 is a security flaw found in IBM WebSphere Application Server Liberty (Dream big, keep it lightweight!), specifically in versions:
23...10
This vulnerability was tracked as IBM X-Force ID 268775.
In Plain English
The core issue is “improper resource expiration handling.”
Resources in the context of web apps usually mean things like user sessions, tokens, cache, or other temporary data. They’re supposed to expire at a set time. But due to this bug, those resources might stick around longer than they should. This means attackers could use older (and potentially weaker) credentials or tokens, putting your application—and user data—at risk.
Why Should You Care?
If your app relies on sensitive resources timing out (think: sessions, cookies, or tokens), this flaw can let attackers re-use them, bypass expiration, or keep using the same login/session much longer than intended.
Let's walk through a likely attack
1. The Set-Up
A user logs in, receiving a session token supposed to expire in, say, 30 minutes.
2. The Vulnerable Expiration
Due to the bug, the server doesn’t properly invalidate or clean up those session tokens.
3. Attack in Action
The attacker—who may have stolen or sniffed an old token (or even a refresh token)—tries to re-use it *after* it should have expired. Instead of being denied, they get access, since the resource is still valid!
Hypothetical Exploit Code
Let's look at pseudocode for a session-checking function that is *not* handling expiration properly (the core of this vulnerability):
# Flawed session validation (simplified)
def validate_session(token):
session = db.get_session(token)
if session:
# Oops - forgot to check if session expired!
return True
return False
# Proper handling should include expiration
def validate_session_secure(token):
session = db.get_session(token)
if session:
if session['expires_at'] > current_time():
return True
return False
In this vulnerability, WebSphere Liberty's internal resource management acts like the *bad* example. Resources aren't expiring when they should.
Am I Vulnerable?
If you run IBM WebSphere Liberty 23...9 or 23...10, YES.
Check your Liberty version using the command line or your console
bin/productInfo version
If you see a version like 23...9 or 23...10, update immediately.
Patch your server!
Upgrade to the latest release of WebSphere Liberty. See IBM’s official security bulletin for patched versions and details.
Links & References
- IBM Security Bulletin for CVE-2023-46158
- NVD CVE-2023-46158 Entry
- IBM X-Force Exchange: 268775
- WebSphere Liberty Downloads & Updates
Final Thoughts
CVE-2023-46158 is a subtle but dangerous flaw. It’s easy to ignore session expiration, but attackers love these bugs. If you use IBM WebSphere Liberty, update as soon as possible. Until you do, keep a close eye on user activity and resource usage.
Timeline
Published on: 10/25/2023 18:17:37 UTC
Last modified on: 11/01/2023 16:58:15 UTC