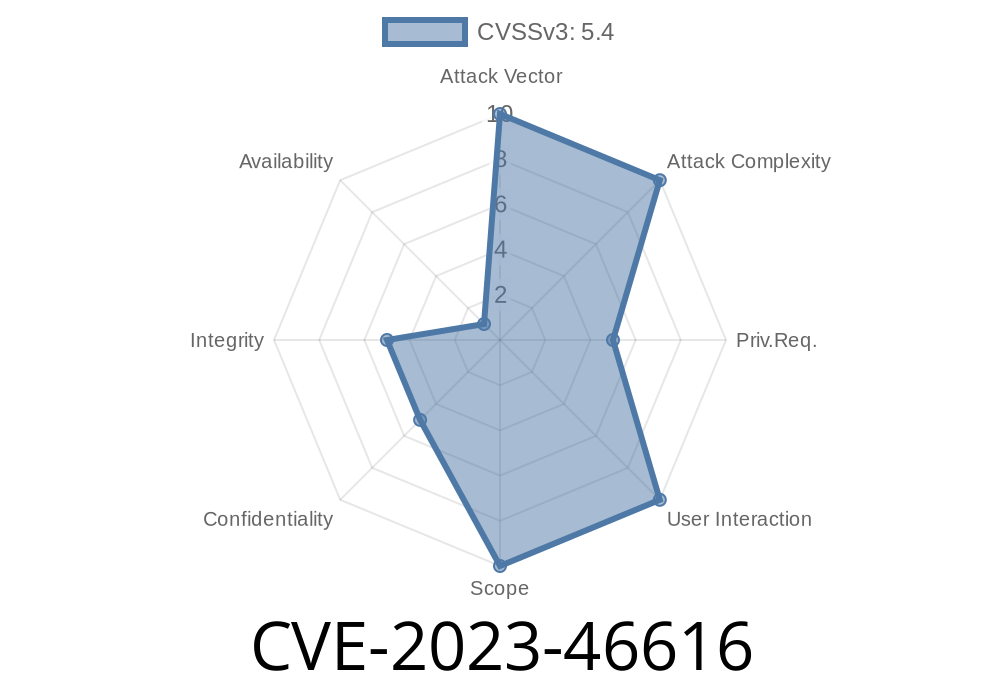
In late 2023, a critical vulnerability was identified in the popular WordPress plugin Draw Attention, developed by NSquared. Tracked as CVE-2023-46616, this flaw stems from missing authorization checks in the plugin, which affects all versions up to and including 2..15. Attackers can exploit incorrectly configured access controls to gain unauthorized access to certain functionality, putting websites and user data at risk.
What is Draw Attention?
Draw Attention is a WordPress plugin that lets site owners create interactive image maps. Users can click on hotspots to view custom content. With over 30,000 active installations, it appeals to a wide range of sites needing interactive images.
Official Plugin Page:
Draw Attention on WordPress.org
The Issue
The core of CVE-2023-46616 is that Draw Attention fails to properly check user permissions before allowing access to specific functions via AJAX endpoints or direct requests. This means any unauthenticated user can trigger sensitive plugin features, such as editing, deleting, or accessing drawn image data.
Impacted Versions:
All versions from the start up to 2..15 (inclusive).
Impact:
Unauthorized modification of content
- Unintended access to private draw/image map data
Why Did This Happen?
The plugin used WordPress AJAX hooks (like admin-ajax.php) for key functions without verifying that the user had the correct capability (such as manage_options or edit_posts). The lack of a current_user_can() check meant anyone could exploit it.
Let’s explore a typical attack using the missing authorization weakness
When a plugin registers an AJAX action in WordPress, it's supposed to validate the user's role. Here’s what safe code would look like:
add_action( 'wp_ajax_da_save_drawing', 'da_save_drawing_callback' );
function da_save_drawing_callback() {
if ( ! current_user_can('edit_posts') ) {
wp_send_json_error( 'You are not allowed to perform this action.' );
return;
}
// Safe: process the drawing save
}
But the plugin’s code was missing this check
add_action( 'wp_ajax_da_save_drawing', 'da_save_drawing_callback' );
function da_save_drawing_callback() {
// MISSING: No user permission check! Anyone can save a drawing!
// Process data directly
}
This meant anyone could POST data to admin-ajax.php?action=da_save_drawing, updating or creating image maps without being logged in.
A remote attacker can send this POST request
POST /wp-admin/admin-ajax.php?action=da_save_drawing HTTP/1.1
Host: victimsite.com
Content-Type: application/x-www-form-urlencoded
drawing_data=%7B%22malicious%22%3A%22content%22%7D&post_id=5
This creates or changes a drawing's data, even if the user is logged out!
How To Fix It
Upgrade Draw Attention to the latest version (check for updates here).
If you can't upgrade right away, temporarily disable the plugin.
Security developers should always check user permissions like this before allowing sensitive actions:
if ( ! current_user_can('edit_posts') ) {
wp_die( 'Permission denied', 'Error', array( 'response' => 403 ) );
}
References
- Original WPVulnDB Advisory
- NVD Listing
- Plugin Changelog
Final Thoughts
CVE-2023-46616 is a strong reminder: never trust incoming requests, even on internal endpoints. Always check user capabilities when processing sensitive data or actions. Website owners using Draw Attention should immediately update to stay safe.
If you find a plugin with missing authorization, report it responsibly — you could save thousands of sites from harm.
Timeline
Published on: 01/02/2025 12:15:13 UTC