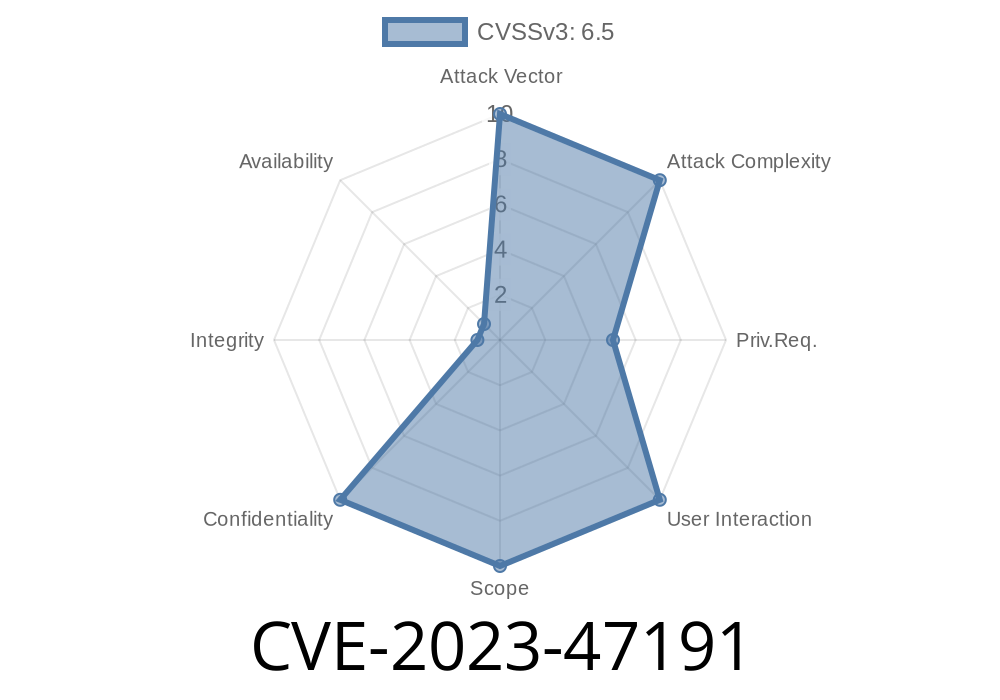
WordPress is the engine behind millions of websites, and its ecosystem of plugins is rich – but sometimes risky. A major vulnerability, CVE-2023-47191, was found in Youzify – BuddyPress Community, User Profile, Social Network & Membership Plugin for WordPress (affecting versions up to 1.2.2). This flaw allows attackers to bypass authorization controls using a user-controlled key, potentially putting your whole user community at risk.
In this article, I'll walk you through what went wrong, how it can be exploited, and what you should do. Code samples and links to original sources are included. I’ll keep the language simple so anyone running a WordPress site can understand the urgency.
What is Youzify?
Youzify (WordPress plugin page) is a powerful set of membership tools for WordPress, letting you build custom social communities, profiles, and more—on top of BuddyPress. It’s popular with site owners who want to turn their WordPress into a social network.
CVE-2023-47191 is an Authorization Bypass Through User-Controlled Key in Youzify.
- A hacker can leverage this flaw to perform actions as another user or even as an admin—without being properly authorized.
The flaw lies in the improper use of user-provided input as an authorization check. Specifically
- The plugin expects a “key” (likely in a POST or GET request) which it trusts to confirm a user's identity or permission.
But, the key can be set or manipulated by the attacker.
- If exploited, authorization is bypassed: the attacker gains access to resources or actions they should not have.
Imagine Youzify uses code something like this in a critical function
$user_id = $_POST['user_id'];
$key = $_POST['key'];
// Intended to check if the 'key' matches the user's stored key.
if ($key === get_user_meta($user_id, 'youzify_approval_key', true)) {
// User is "approved"
youzify_approve_user($user_id);
}
The Problem
- If the attacker can supply both the user_id and the key, and if they can guess or obtain the right key, no other authentication is enforced.
In Some Cases, the Key is Weak
Even worse, in some applications the key is weak, predictable, or is sent via email and can be brute-forced. Sometimes, it’s even omitted in the check—simply supplying any key works, or the code falls back to an insecure default.
How an Attacker Uses This Flaw
1. Find the endpoint: The attacker locates the vulnerable function, often handling requests like /wp-admin/admin-ajax.php?action=youzify_approve.
2. Send crafted request: The attacker sends a POST request with a user_id they want to approve (possibly themselves, or escalate another user) and a key parameter.
3. Gain unauthorized privilege: If the plugin doesn't enforce a safe check, the attacker escalates their role or approves their own account.
Sample Exploit (for educational use only)
curl -X POST http://targetsite.com/wp-admin/admin-ajax.php \
-d "action=youzify_approve&user_id=2&key=123456"
If the key can be guessed, or if the validation is weak, this will approve user 2 as if it was authorized.
Escalate user privileges: Become a moderator or admin without permission.
- Approve/block users: Grant or remove access from the forum or group.
References
- Original WordPress Plugin Page
- NVD - CVE-2023-47191
- Patchstack Advisory
- WPScan Vulnerability Database
Remove or restrict direct access to admin-ajax endpoints by unauthenticated users, if possible.
3. Regularly audit users, roles, and any non-standard approval/registration settings.
Conclusion
CVE-2023-47191 is a serious flaw—easy to exploit, with high impact. If you have a community site built with Youzify, staying up to date is your best defense. This issue highlights the importance of not trusting user-provided keys alone for authorization checks. Always require real authentication!
Stay safe and keep your plugins updated.
*For detailed technical breakdowns, check the references. If you need help, consider hiring a WordPress security expert or contact your hosting provider.*
Timeline
Published on: 12/21/2023 19:15:11 UTC
Last modified on: 12/30/2023 03:20:37 UTC