---
Introduction
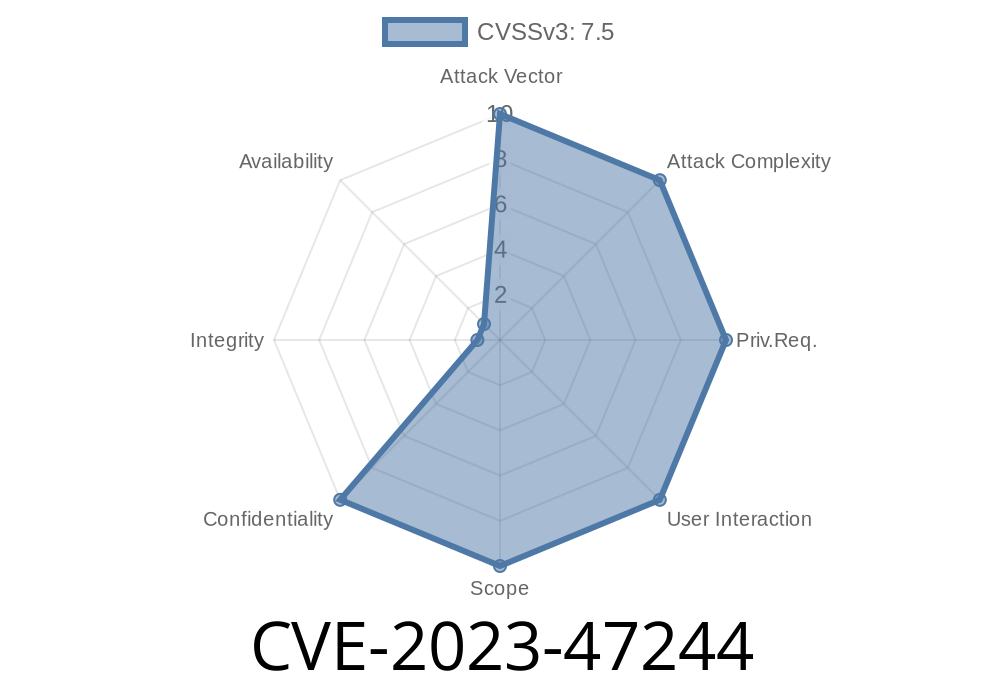
On November 14, 2023, CVE-2023-47244 was assigned to a serious security flaw in the “Email Marketing for WooCommerce by Omnisend” WordPress plugin. The vulnerability exposes sensitive information to unauthorized users. Affected versions range from all public versions up to and including 1.13.8.
This post explains the vulnerability in plain English, gives you a look at how it works—including code snippets—and points you to official sources. Plus, we provide guidance for defending your online store.
Background: What Is Omnisend Email Marketing for WooCommerce?
Omnisend is a popular plugin that helps online shops connect their WooCommerce sites to the Omnisend email marketing platform. It's loved for its automation, abandoned cart reminders, newsletters, and more.
With over 70,000 active installations, it’s a prime target for attackers looking to grab customer data or access sensitive shop info.
What’s the Issue in CVE-2023-47244?
Short version:
There’s a design flaw that lets unauthorized users access confidential data they should never see. The plugin failed to properly enforce permissions on certain REST API endpoints.
Technical summary (from the official NVD entry):
> Omnisend Email Marketing for WooCommerce by Omnisend exposes sensitive information to an unauthorized actor in all versions up to and including 1.13.8.
In practical terms: an attacker can call an API route, and the plugin will hand over sensitive order or customer data—even if the attacker isn’t logged in.
Where’s the Problem?
The vulnerable versions exposed one or more REST API endpoints without verifying whether the request came from a logged-in, authorized user. For example, /wp-json/omnisend/v1/orders could be accessed by anyone on the internet.
Sample Code Snippet
While the plugin source isn’t fully public, a simplified version of what went wrong would look like this:
// In the plugin REST API registration code:
add_action('rest_api_init', function () {
register_rest_route('omnisend/v1', '/orders', array(
'methods' => 'GET',
'callback' => 'omnisend_get_orders',
// 'permission_callback' => '__return_true', // BAD: allows everyone
));
});
// The dangerous handler function
function omnisend_get_orders($request) {
$orders = ...; // Fetches full order/customer info
return new WP_REST_Response($orders, 200);
}
The real vulnerability is that the permission_callback argument isn't set to something that checks if the user is logged in, or has proper admin/shop-manager rights.
It should have been something like
'permission_callback' => function() {
return current_user_can('manage_woocommerce');
},
Any attacker (even not logged in) can request sensitive shop information
curl -X GET http://target-site.com/wp-json/omnisend/v1/orders
This returns JSON data, possibly with full order details, including customer names, emails, addresses, and other business-sensitive data.
References
- NVD: CVE-2023-47244
- Wordfence Advisory
- Omnisend on WordPress.org
Update Immediately!
Omnisend fixed this in version 1.13.9. Update the plugin from your WordPress dashboard or download the latest version here.
Restrict Access
If you can’t upgrade, use a security plugin or firewall (like Wordfence) to block access to /wp-json/omnisend/v1/orders and similar endpoints.
Review Data Exposure
Check your logs to see if API endpoints were accessed by strange IPs. Reach out to any customers whose data may have been exposed.
Final Thoughts
Vulnerabilities like CVE-2023-47244 show how crucial it is to update your WordPress plugins and restrict who can access your site’s APIs. Even popular, well-maintained plugins can have dangerous oversights that put your shop and customers at risk.
If you run WooCommerce with Omnisend, don’t wait—patch now!
Stay safe, keep your plugins up to date, and always pay attention to security advisories!
> _This post is for educational purposes. If you discover a security issue, report it to the plugin vendor promptly and ethically._
Timeline
Published on: 11/23/2023 21:15:07 UTC
Last modified on: 11/30/2023 16:43:06 UTC