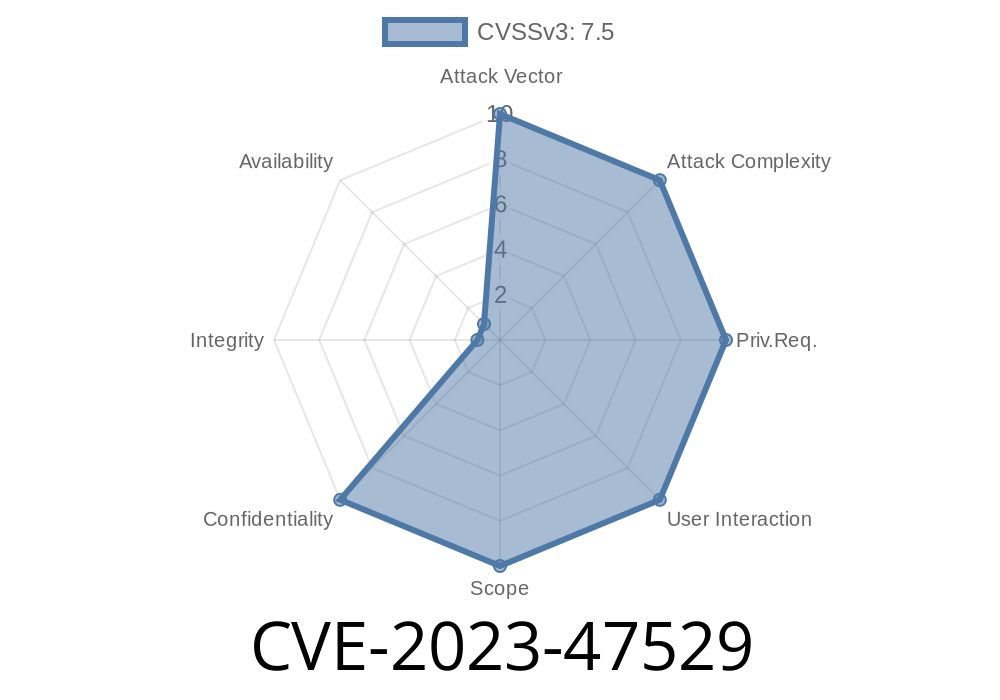
A new security vulnerability, CVE-2023-47529, has been discovered in the popular WordPress plugin ThemeIsle Cloud Templates & Patterns Collection. If you’re a WordPress site owner or developer, this is important news. Let’s break down what happened, why it’s a big deal, and how you can protect yourself.
What is ThemeIsle Cloud Templates & Patterns Collection?
ThemeIsle is known for making popular WordPress themes and plugins. Their Cloud Templates & Patterns Collection plugin lets users import ready-made design templates and patterns. This tool can save hours of design work, but a hidden danger was uncovered in versions up to 1.2.2.
What is CVE-2023-47529?
CVE-2023-47529 is a vulnerability categorized as “Exposure of Sensitive Information to an Unauthorized Actor.” In simple words, this bug allows attackers to see private or sensitive information from your WordPress site without your permission. That info could include configuration data, user email addresses, or other details you don’t want to leak.
How Does the Vulnerability Work?
When a plugin processes AJAX requests (behind-the-scenes requests your browser sends to your website), it must check if the user is allowed to access the data. In vulnerable versions, the ThemeIsle plugin did not properly check who was asking for information. That means that anyone—including anonymous visitors—could ask for sensitive data and the plugin would hand it over!
Here’s what this might look like in code
// Vulnerable code example in WordPress plugin
add_action('wp_ajax_nopriv_ti_fetch_templates', 'ti_fetch_templates');
function ti_fetch_templates() {
// No permission checks
$templates = get_option('ti_templates_collection');
echo json_encode($templates); // Exposes data to all users, no access control!
wp_die();
}
As you can see, the function exposes data to anyone calling it, without checking if the visitor is logged in or has permission.
Exploit Details
To exploit this vulnerability, an attacker only needs to know the right AJAX action. They can send a simple POST request to your WordPress site like this:
curl -X POST https://yoursite.com/wp-admin/admin-ajax.php \
-d "action=ti_fetch_templates"
This will return a JSON object with sensitive site data, even if the attacker is not logged in. Depending on your site, this could contain directory paths, internal identifiers, or even template content that reveals business-sensitive information.
Some penetration testers have created proof-of-concept (PoC) exploits by automating these requests with curl, Python, or custom scripts.
Who is Affected?
If your site uses the ThemeIsle Cloud Templates & Patterns Collection plugin, version 1.2.2 or below, your site is potentially vulnerable. This includes:
How to Fix
Update your plugin NOW. The developers have released a patch in version 1.2.3 and above that addresses this issue by verifying permissions and restricting who can access the data.
Find Cloud Templates & Patterns Collection.
4. Click Update Now if an update is available, or download the latest version from the official plugin page.
After updating, verify you are running at least version 1.2.3.
Original References
- NVD – CVE-2023-47529
- Wordfence Advisory (Cloud Templates Vulnerability)
- Plugin page: ThemeIsle Cloud Templates & Patterns Collection
Conclusion
CVE-2023-47529 is a reminder that even trusted plugins can have dangerous bugs. If you use ThemeIsle Cloud Templates & Patterns, update now to stay safe. Check your other plugins too—make sure your site isn’t giving up secrets to anyone who asks.
Stay secure, and always keep an eye on your plugins!
Timeline
Published on: 11/23/2023 21:15:00 UTC
Last modified on: 11/30/2023 16:42:00 UTC