Published: June 2024 <br>By: [Your Name] – Simple Security Reads
What’s the Vulnerability?
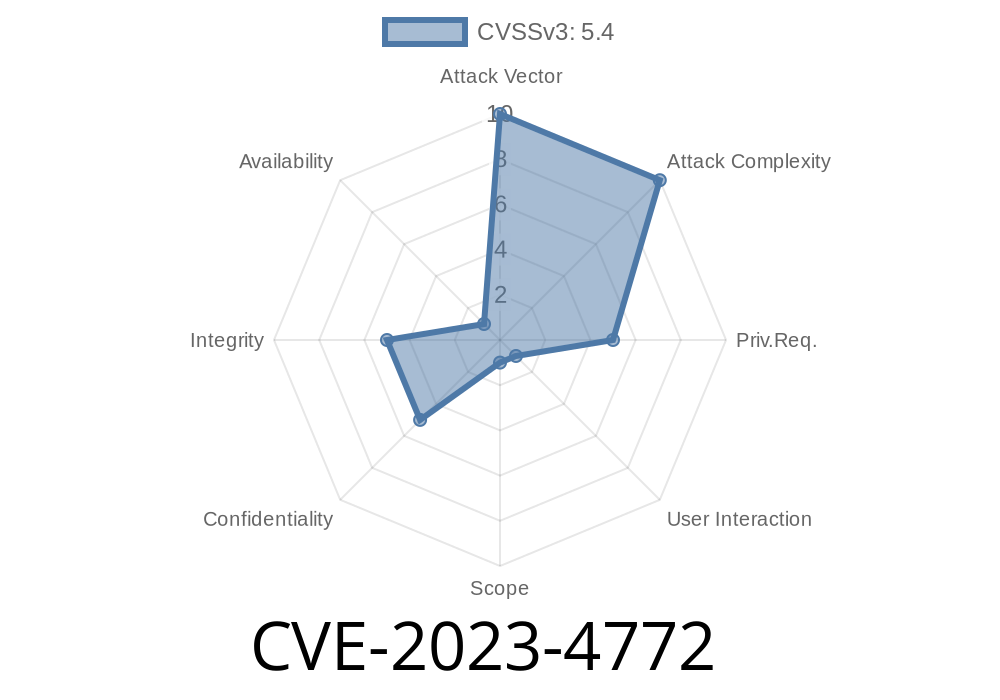
CVE-2023-4772 highlights a Stored Cross-Site Scripting (XSS) vulnerability in the popular Newsletter plugin for WordPress, affecting plugin versions up to and including 7.8.9. The issue exists in the newsletter_form shortcode, which doesn’t properly sanitize or escape user-supplied attributes.
This allows an attacker—with at least contributor-level access—to inject malicious JavaScript on a WordPress site. Those scripts execute whenever anyone visits a page with the tainted shortcode, potentially leading to site compromise, session hijacking, or further malware delivery.
Where’s the Flaw?
The vulnerable code lies in how the plugin handles shortcode attributes from [newsletter_form]. Instead of filtering or escaping the input, it directly outputs them, trusting user content—which is a top mistake.
A simplified look at the bad code pattern might look like this (not exact, but representative)
// Hypothetical vulnerable function
function render_newsletter_form($atts) {
// Accept attributes straight from shortcode
$title = $atts['title']; // Not sanitized!
echo '<div class="newsletter-title">'.$title.'</div>';
}
add_shortcode('newsletter_form', 'render_newsletter_form');
If you imagine [newsletter_form title="<script>alert('XSS')</script>"], this code would output exactly that—JavaScript and all.
The attacker needs a contributor or higher role (not just Subscriber).
2. Create a Post/Page:
`
[newsletter_form title=""]
Here’s a simple PoC you can use (in a test environment only)
[newsletter_form title='<img src=x onerror="alert(XSS by CVE-2023-4772)">']
When a page or post containing this shortcode is viewed, the injected code will execute. Replace alert(...) with any arbitrary JS.

*Sample XSS alert, for illustration.*
References & Official Reports
- CVE Database Entry – CVE-2023-4772
- Wordfence Advisory
- Newsletter Plugin Changelog
## How To Fix/Protect
Patch:
Update to Newsletter plugin version 7.9. or later.
(Download latest version)
Hardening:
Conclusion
CVE-2023-4772 shows how even “trusted” input must be filtered in WordPress plugins. If your site uses the *Newsletter* plugin, update immediately—before contributors, bored staffers, or site hijackers place persistent backdoors.
*Simple solutions, strong security!
Follow us for more clear breakdowns.*
Timeline
Published on: 09/07/2023 02:15:00 UTC
Last modified on: 09/11/2023 18:17:00 UTC