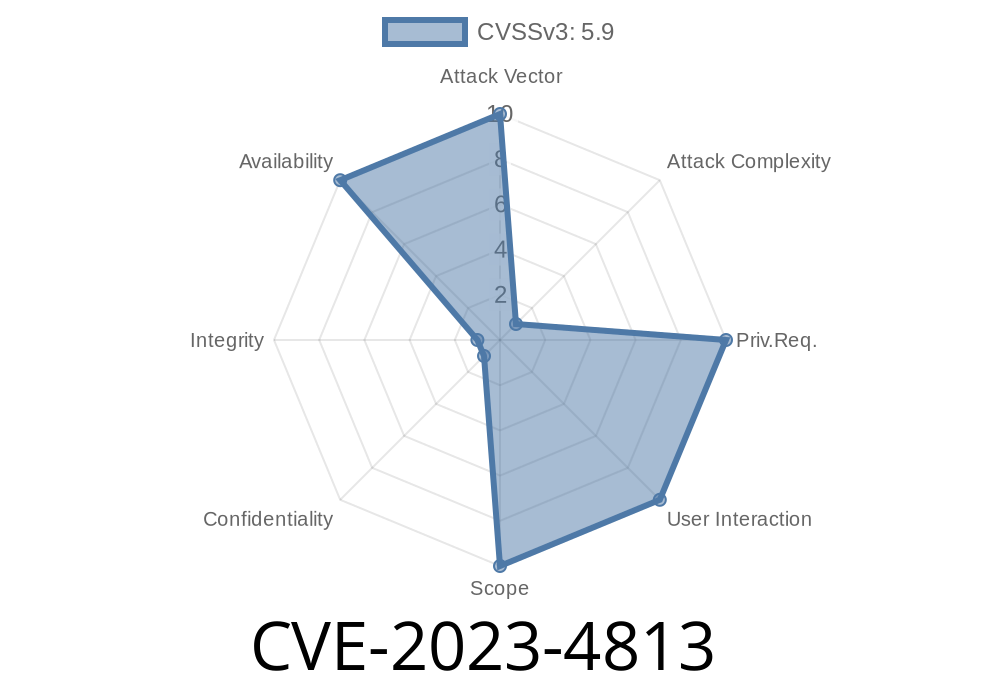
In September 2023, security researchers and Linux maintainers discovered a significant vulnerability in the GNU C Library (glibc), filed as CVE-2023-4813. This bug sits in the gaih_inet function and can be triggered in specific, but real-world, system configurations. If exploited, it can crash applications—potentially leading to a denial of service or worse. In this deep-dive, we'll look at what causes the bug, how it happens, which configurations make you vulnerable, and what you should do to stay protected. Code snippets and references are included for developers and sysadmins.
What Is glibc and Why Does It Matter?
The GNU C Library, or glibc, is the standard C library used by most Linux distributions. Whenever Linux programs want to resolve hostnames (for example, when you type a web address into your browser), they call functions provided by glibc—one of which is getaddrinfo. Under the hood, getaddrinfo might call internal helpers like gaih_inet.
A low-level bug in glibc can affect nearly every process running on a Linux system.
Vulnerability: Use-after-free in gaih_inet (part of getaddrinfo’s DNS resolution process)
- Trigger: When your /etc/nsswitch.conf configures the hosts database with SUCCESS=continue or SUCCESS=merge.
Here's a pseudo-representation of how such a bug can slip through in C
char *ptr = malloc(100);
free(ptr);
// Some unpredictable logic
do_something();
use_memory(ptr); // Oops: use-after-free!
In the real glibc code, the flow is much more complex, involving resolution steps that can temporarily free memory chunks and then, due to certain nsswitch.conf behaviors, use them again if alternate backends are consulted.
How Does nsswitch.conf Make This Worse?
Your system’s /etc/nsswitch.conf controls how name lookups are performed. The default line (on most systems) looks like:
hosts: files dns
But if an administrator has custom logic—like
hosts: files [SUCCESS=continue] dns
or
hosts: files [SUCCESS=merge] dns
—then after getting a successful result from one backend, glibc will sometimes jump to the next backend, leading to a path where memory is prematurely freed, and then unexpectedly accessed later.
Not Exploitable by Default: If your system uses the standard hosts: files dns, you’re safe.
- Exploitable If: Someone manually tweaks /etc/nsswitch.conf using SUCCESS=continue or SUCCESS=merge options.
- What Happens: Applications calling getaddrinfo (e.g., web servers, SSH, even some common scripts) can crash if they try to resolve a hostname.
- Demo Case (C): The following snippet will *crash* an affected glibc if nsswitch.conf is misconfigured:
#include <netdb.h>
#include <stdio.h>
int main() {
struct addrinfo hints = {}, *res;
hints.ai_family = AF_UNSPEC;
// Replace "example.com" with any hostname
int err = getaddrinfo("example.com", "http", &hints, &res);
if (err == ) {
printf("Resolved!\n");
freeaddrinfo(res);
} else {
printf("Failed: %s\n", gai_strerror(err));
}
return ;
}
With a vulnerable /etc/nsswitch.conf, running this simple program could make it segfault.
What Should You Do?
1. Check your /etc/nsswitch.conf
Update glibc!
- Most major distributions released patches quickly. Update your system using your preferred package manager.
Official Fix References
- Red Hat Security Advisory
- glibc upstream patch
- Debian Security Tracker
glibc bugs affect everyone—even seemingly small ones.
3. Crashes ≠ code execution—so impact is “denial of service” not remote code execution in this case. Future bugs might not be so 'lucky'.
Final Thoughts
If you’ve customized your Linux system’s hostname resolution process, or you run third-party distros and containers, proactively check your configs and update glibc soon. Bugs like CVE-2023-4813 serve as a reminder to rely on safe defaults and stay on top of security advisories.
Stay safe. Update often. And always review your nsswitch.conf!
References
- Red Hat CVE page
- Original glibc patch
- Debian Security Tracker for CVE-2023-4813
- NSS Switch Config Documentation
If you found this useful, bookmark for future glibc updates!
Timeline
Published on: 09/12/2023 22:15:08 UTC
Last modified on: 11/10/2023 18:15:10 UTC