Date: June 2024
CVE: CVE-2023-48322
Affected Plugin: eDoc Employee Job Application – Best WordPress Job Manager for Employees
Affected Versions: All versions up to and including 1.13
Vulnerability Type: Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting' or XSS)
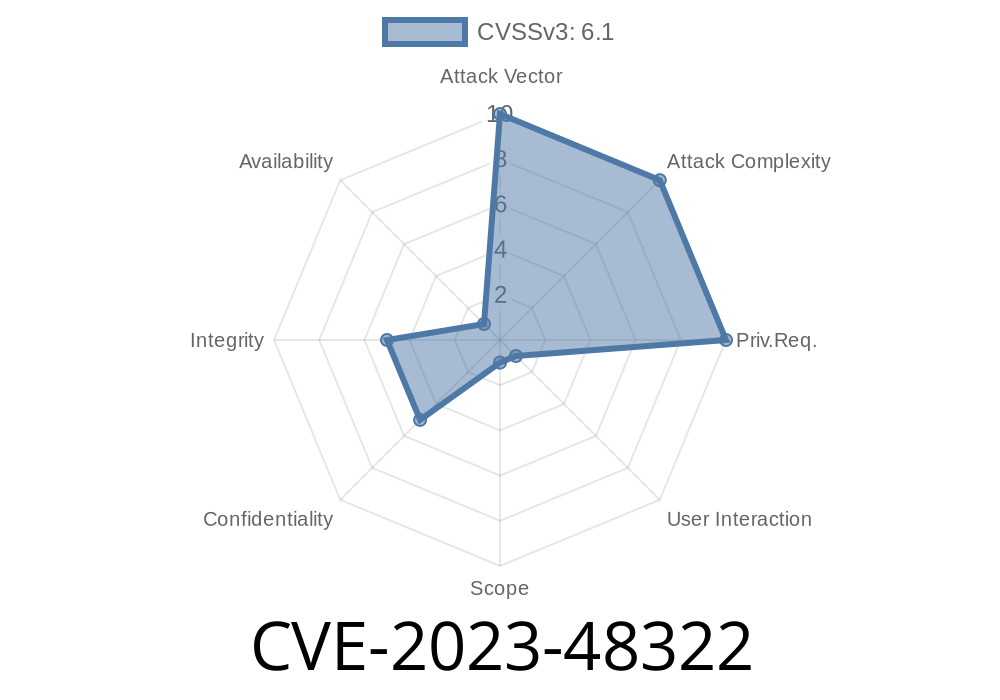
Severity: Medium to High
What is CVE-2023-48322?
CVE-2023-48322 is a reflected Cross-site Scripting (XSS) vulnerability found in the popular WordPress plugin “eDoc Employee Job Application – Best WordPress Job Manager for Employees”. This plugin helps website owners manage job applications and employee data, but up to version 1.13, it improperly handles user inputs on certain pages. This specific bug allows attackers to inject and execute malicious JavaScript code in the browsers of users who visit a specially crafted link.
How Does the Vulnerability Work?
When a website doesn’t properly “sanitize” (clean up) what users type into forms or pass as parameters via URLs, it can end up displaying that text directly on a web page. If an attacker puts JavaScript code inside those parameters, it can run in the browser of anyone who clicks a link with such code, potentially stealing cookies, login credentials, or performing actions as the victim.
This is called reflected XSS because the malicious payload is “reflected” off the web server and runs in the victim's browser.
Code Snippet: Vulnerable Line Example
Below is a simple, hypothetical example of how this might happen in an affected version of eDoc Employee Job Application:
// Possibly in a plugin template or handler file
echo "<div>Thank you, " . $_GET['name'] . "!</div>";
Here, if someone sets the name parameter in the URL, the value appears on the page *without* any filtering or escaping. An attacker could use a link like this:
https://victimsite.com/jobs?name=<script>alert('XSS')</script>;
When someone clicks it, the browser runs the JavaScript code.
Assume the plugin has an endpoint:
https://example.com/jobs?job_position=
`
https://example.com/jobs?job_position=
Real-World Example Results
See a proof-of-concept alert box video:
Example Video PoC: XSS in WordPress Plugin *(For educational reference. Not specifically from this plugin.)*
References and Advisories
- CVE-2023-48322 - NIST Details
- WPScan Report
- Original Plugin Page
1. Update the Plugin
The safest solution is to upgrade the plugin as soon as a patched version is available.
> Check for Updates:
> Go to WordPress dashboard → Plugins → Update eDoc Employee Job Application (if new version is available).
2. Sanitize and Escape in Your Code
If you must patch yourself (not recommended for most users), always sanitize inputs and escape outputs:
// Safer output: use esc_html() for WordPress
echo "<div>Thank you, " . esc_html($_GET['name']) . "!</div>";
3. Block or Restrict Suspicious Requests
Use a security plugin (like WordFence or Sucuri) to help catch and block malicious traffic.
What Should Website Owners Do?
- Update Plugins: don’t delay—vulnerabilities like this are often exploited within days or even hours of disclosure.
Conclusion
CVE-2023-48322 is a good reminder: *sanitize all user inputs, always!* If you use the “eDoc Employee Job Application” plugin for WordPress (up to v1.13), update immediately to avoid being hacked. Cross-site scripting can lead to serious loss of data and site takeover.
Stay safe, keep your tools updated!
*Do you have questions, or found a new WordPress bug? Let us know in the comments!*
Timeline
Published on: 11/30/2023 12:15:00 UTC
Last modified on: 12/05/2023 19:22:00 UTC