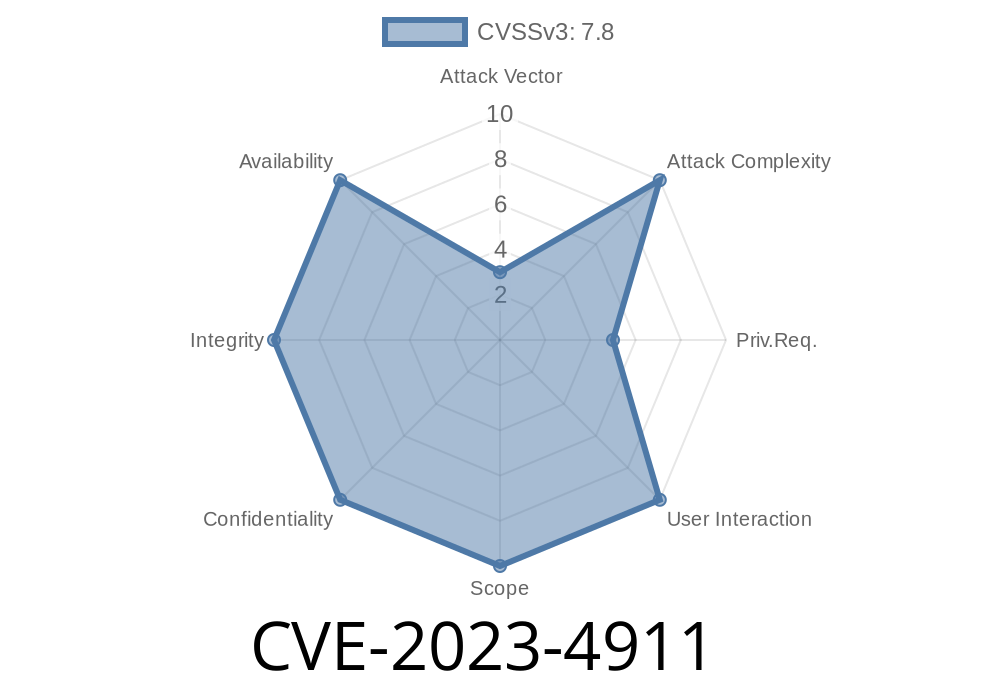
In October 2023, the security community became aware of a significant vulnerability in the GNU C Library’s dynamic loader (ld.so). This buffer overflow, labeled as CVE-2023-4911, is caused by improper handling of the GLIBC_TUNABLES environment variable. In certain contexts, a local attacker can craft this variable to achieve privilege escalation — potentially gaining root (administrator) access to a system. In this post, we'll break down what happened, who is at risk, how it can be exploited, and see the bug up close with some code snippets.
What Is Glibc and Why ld.so Matters
- Glibc: The GNU C Library (glibc) is a core component of almost every Linux distribution. It provides standard APIs for system functions, used by virtually every program.
- ld.so: This is the "dynamic loader" — the program that prepares a compiled binary for execution, resolving shared library dependencies before handing over control.
If you want to run nearly any program on Linux, you interact with glibc and ld.so — whether you know it or not.
The Issue: Buffer Overflow in GLIBC_TUNABLES
The bug stems from the way the dynamic loader parses the GLIBC_TUNABLES environment variable. This variable lets users fine-tune various glibc behaviors by supplying settings in the form of key=value pairs, separated by colons, e.g.:
GLIBC_TUNABLES="glibc.malloc.check=1:glibc.rtld.verbose=1"
The loader code had an unsafe string copying process. When a carefully crafted, exceedingly long value is set for GLIBC_TUNABLES, the code can "overflow" a memory buffer, overwriting adjacent memory regions.
This classic programming mistake is especially dangerous if the program runs as root (with SUID), since a buffer overflow can lead to attacker-controlled code execution with root privileges.
Code Snippet Illustration
Below is a simplified (and illustrative!) example showing how a buffer overflow can happen. The vulnerable code (in glibc) was akin to:
// This is just illustrative — not the actual glibc code.
char buf[256];
strcpy(buf, getenv("GLIBC_TUNABLES")); // No length check!
If GLIBC_TUNABLES holds more than 256 characters, you'll end up writing past the end of buf, smashing the stack or other critical memory.
To actually exploit this on a real machine
1. Find a SUID Binary: A SUID (Set User ID) binary runs as root even when launched by a normal user. Classic examples are /usr/bin/su, /usr/bin/passwd, etc.
Set Malicious Env Variable:
- Set GLIBC_TUNABLES to a long, precisely crafted value that triggers the buffer overflow and injects shellcode.
3. Execute Binary: Run the SUID binary with this environment, causing the overflow in ld.so before the main program's code is even reached.
Proof-of-concept pseudocode for exploitation (do not use on systems you don't own!)
# On a vulnerable system, as a regular user:
export GLIBC_TUNABLES=$(python3 -c 'print("A" * 512 + YOUR_SHELLCODE)')
/usr/bin/su
# If vulnerable, the local user might get root shell access
Note: Modern distributions may have some exploit mitigations like ASLR, stack canaries, or environment sanitization in place. But clever attackers can sometimes bypass these, especially on older or custom setups.
Original References and More Details
- Red Hat Security Advisory
- Qualys Security Advisory (with technical exploit)
- Distrowatch summary
- Glibc source code / patch commit
For detailed exploit code and root cause analysis, the Qualys report is an excellent resource.
Linux desktops and servers running glibc version 2.34 (released August 2021) through 2.38.
- SUID binaries on the system — if present and not environment-sanitizing — are the attack target.
If you run a public-facing multi-user system, patch immediately. Cloud VMs and containers can be affected, depending on configuration.
sudo apt update && sudo apt upgrade
On Fedora/RHEL/CentOS:
sh
sudo yum update glibc
- Check for SUID binaries: Find SUID root binaries with:
sh
find / -type f -perm -04000 -user root 2>/dev/null
`
Remove or restrict SUID programs you don’t absolutely need.
- Limit untrusted users: This is a local-only exploit (attackers need an account), but if they can get access by other means, it's a big risk.
---
## Final Thoughts
Mismanaging environment variables in privileged processes is a common, dangerous pitfall. CVE-2023-4911 is a classic yet potent example: a single buffer overflow in a key system component can undo all your OS security in a blink. Keep your software up-to-date, restrict SUID binaries, and monitor your system’s security advisories.
If you’re a sysadmin or hobbyist, double-check your glibc version now — and patch if needed!
---
Links:
- Qualys Security Advisory
- NVD Entry for CVE-2023-4911
- Glibc Patch Commit
---
Stay safe and keep your systems updated!
Timeline
Published on: 10/03/2023 18:15:00 UTC
Last modified on: 10/06/2023 17:15:00 UTC