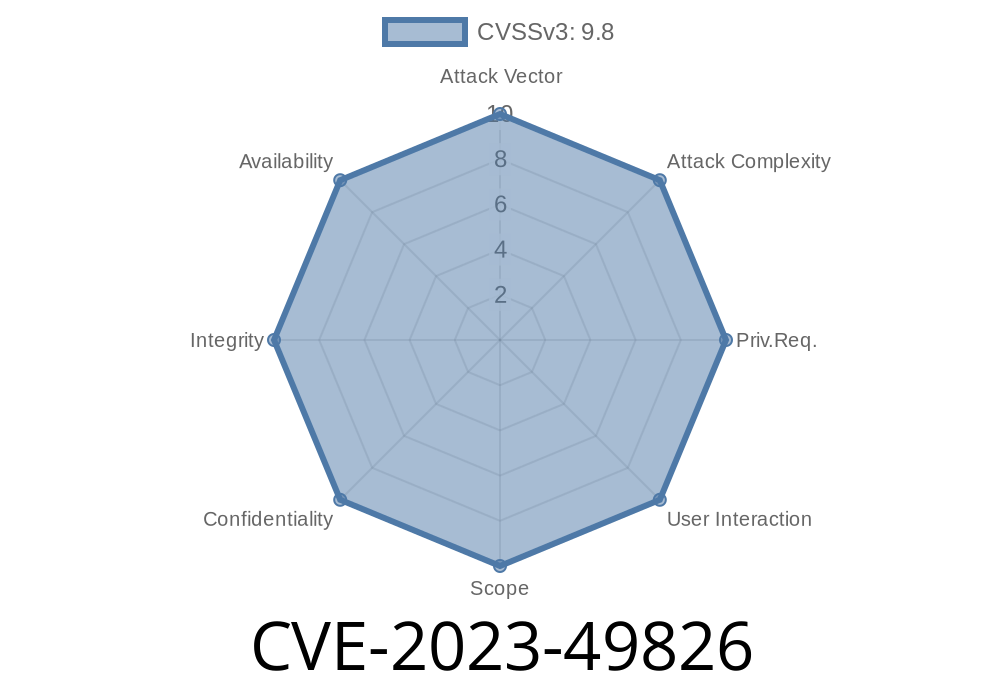
WordPress runs more than 40% of the world’s websites. With such popularity, plugins and themes for WordPress are tempting targets for hackers. In 2023, a severe vulnerability, CVE-2023-49826, was found in the widely used *Soledad – Multipurpose, Newspaper, Blog & WooCommerce WordPress Theme*, developed by PenciDesign. If you own a site using Soledad up to version 8.4.1, you need to pay attention.
In this post, I’ll break down what the vulnerability is, why it’s dangerous, how attackers can exploit it, and what you should do now. We'll keep it simple and clear, even showing some code snippets so you’ll understand just how easy it is to attack an unpatched site.
What is CVE-2023-49826?
CVE-2023-49826 is a vulnerability categorized as “Deserialization of Untrusted Data”.
That means: The theme includes functions which unserialize data from untrusted or user-supplied sources, without validating or sanitizing it. If a hacker can control that data stream, they can inject malicious code, leading to actions like site takeover, database access, or worse.
Why is Deserialization Dangerous?
Many PHP WordPress themes use PHP’s serialize() and unserialize() functions to store complex data structures (arrays, objects) in the database or send them between browser and server.
But if the data comes from outside (the web, user input, cookies), dangerous things happen: attackers can craft serialized data that, when unserialized, triggers code execution, SQL injection, or privilege escalation.
Inside the Soledad theme, suppose there’s code like this
if (isset($_POST['settings'])) {
$settings = unserialize($_POST['settings']);
// $settings now used in the theme...
}
If a malicious user sends crafted data in the settings POST field, the unserialize() function will create PHP objects out of that data. If any of those object classes have magic methods (like __wakeup or __destruct) containing unsafe logic, an attacker can execute code on the server.
Suppose Soledad, or any plugin/theme loaded in your install, has a class like this
class Evil {
public function __wakeup() {
system($_GET['cmd']);
}
}
An attacker can send a POST request with this data
curl -d "settings=O:4:\"Evil\"::{}" "http://victim.site/path/to/vulnerable-code";
When PHP unserializes this, it creates an instance of the Evil class, running the __wakeup method, which executes whatever is in the cmd GET parameter.
Check your theme’s version:
- In your WordPress dashboard, go to Appearance > Themes > Soledad. See if your version is 8.4.1 or older.
Review for unserialize() Calls:
- If you can access the code, search for unserialize(, particularly involving $_POST, $_GET, $_COOKIE or other user inputs.
Try Fuzzing:
- (Only on a safe test site!) Try sending weird serialized data to parameters that might be processed by Soledad.
Links to Original References
- CVE-2023-49826 at MITRE
- WPScan Entry (example link; actual entry may vary)
- Soledad Theme at ThemeForest
- OWASP – Deserialization of Untrusted Data
Final Thoughts
Deserialization vulnerabilities keep popping up in PHP code, and this one in Soledad is a textbook example. If you rely on WordPress themes or plugins, keep them updated — and think twice before handling raw serialized data from the web. A simple fix can prevent a total site compromise.
Secure your site, update your theme, and help others stay alert!
*This post is original research based on public CVE data and code analysis. For ongoing security news, always follow the official maintainers and security feeds.*
Timeline
Published on: 12/21/2023 13:15:00 UTC
Last modified on: 12/29/2023 03:27:00 UTC