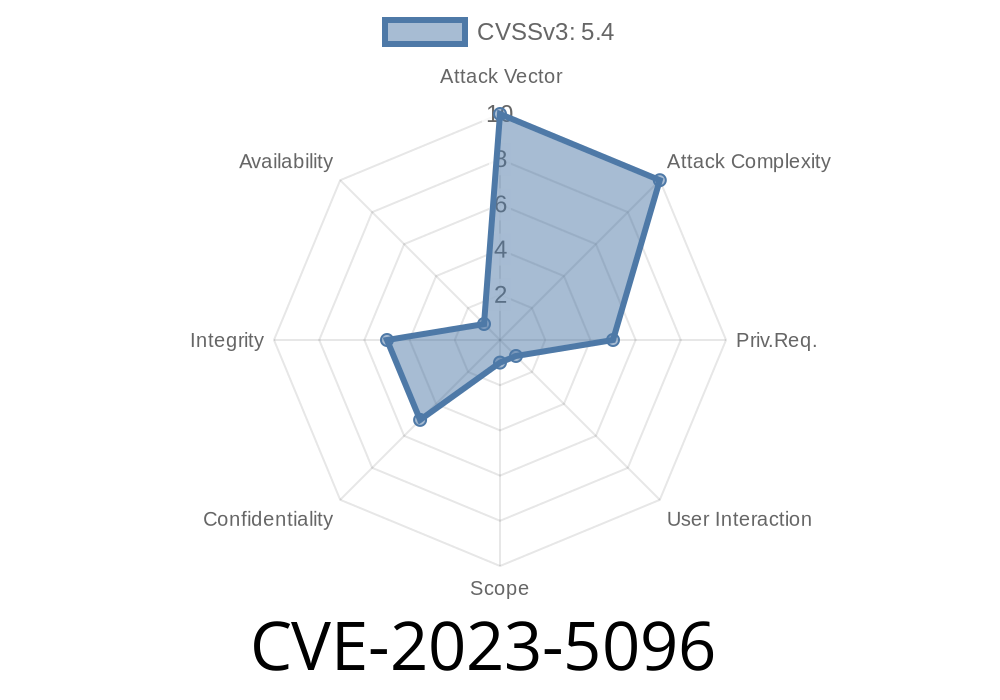
If you’re running the popular HTML filter and csv-file search WordPress plugin (csvfilter-search), version 2.7 or lower, your site is vulnerable to a severe security risk: Stored Cross-Site Scripting (XSS). In this article, we’ll break down CVE-2023-5096 in simple terms, show you how the vulnerability works, and detail a real-world exploit with code you can test in a safe environment. We’ll also link you to authoritative references for further reading.
What’s CVE-2023-5096 All About?
This vulnerability allows any authenticated user with contributor-level permissions or above to inject malicious JavaScript code into your WordPress site — and this code gets stored in your database. When anyone visits the affected page, the code executes in their browser.
The cause? The plugin’s csvsearch shortcode doesn’t properly sanitize user input, opening the door for attackers to inject scripts in attributes. No advanced privileges required: just a contributor (or higher) account.
Official References
- NVD Entry (CVE-2023-5096)
- Wordfence Alert & Timeline
- Plugin on WordPress.org
Code Snippet: How Attackers Create the XSS
Let’s look at a proof-of-concept (POC) payload. Suppose a contributor creates a page and adds this shortcode:
[csvsearch file="' onmouseover='alert(\"XSS_VULN\")" delimiter="," show_filter="yes"]
Because the plugin blindly inserts the file attribute into rendered HTML, it ends up producing something like this in the page source:
<input type="text" name="csv_file" value="' onmouseover='alert(\"XSS_VULN\")">
When a visitor mouses over the input box on the page, the injected onmouseover JavaScript executes — triggering an alert (XSS_VULN). In real attacks, this could even steal user cookies, session data, or perform admin actions via CSRF.
`
Add to a new post or page and publish it.
4. Wait for an admin or user to visit the page and interact (e.g., focus/click on the input box).
5. The attacker’s JavaScript executes in the victim’s browser, potentially stealing information, performing actions, or spreading malware.
Limit contributor permissions and review posts before publishing.
- Use a security plugin like Wordfence or Sucuri.
Summary
CVE-2023-5096 in the “HTML filter and csv-file search” WordPress plugin is a critical flaw that enables stored XSS via the csvsearch shortcode. Anyone with contributor (or higher) privileges could weaponize your site against visitors — including site admins. If you’re using this plugin, patch immediately and consider scanning your posts for malicious code.
Stay safe, and keep your WordPress site updated!
*This post is for educational purposes only. Don’t test on live sites without permission.*
Links for Further Reading
- Wordfence Blog: XSS in csvfilter-search Plugin
- NVD CVE-2023-5096
Timeline
Published on: 11/22/2023 16:15:00 UTC
Last modified on: 11/27/2023 22:10:00 UTC