---
Introduction
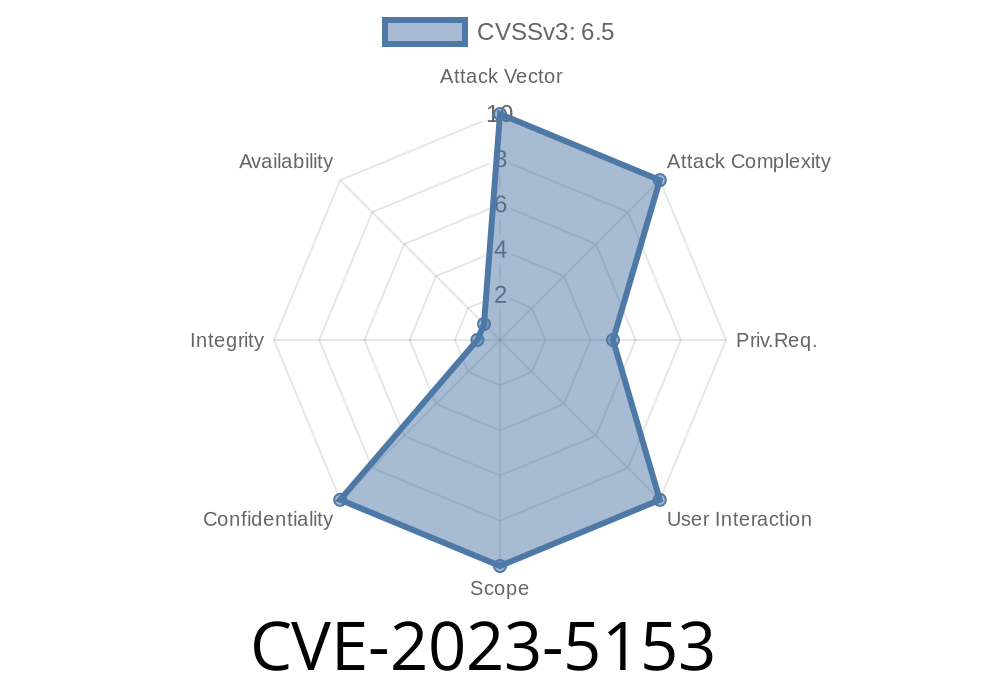
A serious vulnerability labeled CVE-2023-5153 was discovered in the D-Link DAR-800, a networking device commonly used by businesses and organizations. This vulnerability, marked as "Critical," affects devices running any firmware version up to 20151231. The issue is found in the file /Tool/querysql.php and makes the device susceptible to a remotely exploitable SQL Injection attack.
Important Note:
The D-Link DAR-800 is an end-of-life product. D-Link is not providing security updates, and using this device now presents significant risk. If your network still relies on this hardware, immediate replacement is strongly recommended.
Vulnerability Details
- Identifier: CVE-2023-5153
- Alternate Reference: VDB-240249
- Affected File: /Tool/querysql.php
Type: SQL Injection
- Attack Vector: Remote/Unauthenticated
How Does the Exploit Work?
The vulnerable PHP script /Tool/querysql.php directly uses user-supplied input in SQL queries without proper sanitization. This allows attackers to inject arbitrary SQL commands, which can lead to:
Extraction of sensitive information (usernames, passwords)
- Database manipulation (adding/deleting users, altering config)
Below is a simplified example of an attack using a crafted HTTP request
# Example HTTP POST request exploiting the vulnerable endpoint
POST /Tool/querysql.php HTTP/1.1
Host: <router-ip>
Content-Type: application/x-www-form-urlencoded
id=1';SELECT+user,password+FROM+users;--+
In this case, sending such input would cause the database to execute not only the intended query, but also the attacker's appended instructions.
Example Vulnerable PHP Code
<?php
// Hypothetical vulnerable snippet from /Tool/querysql.php
$id = $_POST['id'];
$query = "SELECT * FROM users WHERE id = '$id'";
$result = mysqli_query($conn, $query);
// ...
?>
Why is this bad? The value of id comes directly from the user, without any validation or escaping. This means an attacker can inject extra SQL commands—classic SQL Injection.
Real-World Impact
- Attackers can steal or change configuration data, obtain admin credentials, and take over the router.
The attack can be automated and performed remotely—no need to be physically near the device.
- This is especially dangerous because networking gear forms the backbone of the organization's infrastructure.
Remediation and Mitigation
Unfortunately, no patch will be issued. D-Link no longer supports the DAR-800 as officially confirmed.
References
- CVE-2023-5153 at MITRE
- VulDB Entry: VDB-240249
- D-Link Security Notifications
Conclusion
CVE-2023-5153 demonstrates how vulnerabilities in unsupported, obsolete devices can create serious security holes. Because the D-Link DAR-800 is no longer maintained, it will not be fixed and should not be used in any production environment.
Security is everyone's responsibility. Check your equipment inventory today—retire and replace any unsupported hardware to keep your network safe.
Timeline
Published on: 09/25/2023 03:15:09 UTC
Last modified on: 11/07/2023 04:23:33 UTC