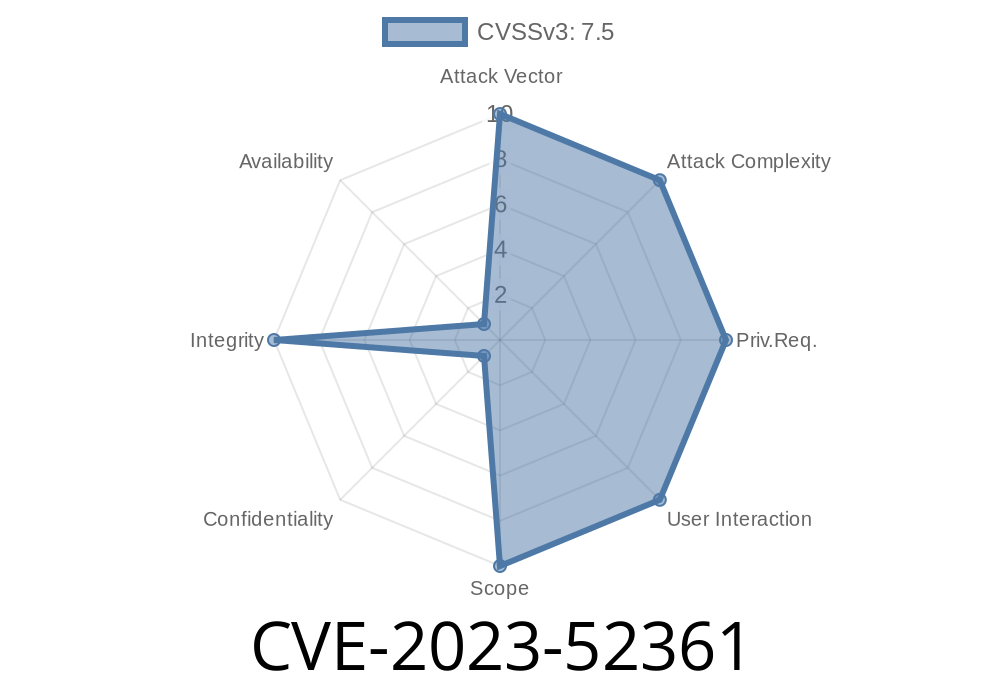
In late 2023, security researchers uncovered a significant flaw in the VerifiedBoot module, tracked as CVE-2023-52361. This vulnerability can lead to authentication errors that affect system integrity, opening the door for attackers to bypass critical security checks. In this article, I break down what this vulnerability is, how it works, and include code samples to demonstrate its impact. I also link to official resources for further reading.
What is VerifiedBoot?
VerifiedBoot is a security feature present in many modern devices (including Android smartphones and embedded systems). Its core job is to verify that the code being booted is both authentic and unmodified, preventing tampering or unauthorized software from loading at boot time.
Description of the Vulnerability (CVE-2023-52361)
Officially listed on NIST’s National Vulnerability Database and MITRE, CVE-2023-52361 is a flaw in the authentication routine of the VerifiedBoot module.
How the Vulnerability Occurs
A flaw in the code path that verifies boot images allows attackers to craft modified images that pass signature verification checks. This means an attacker with physical access (or malware with enough privileges) might replace or alter the boot image, bypassing the integrity check.
Risk:
If successfully exploited, malicious actors can boot modified system images, defeat OS-level protections, and achieve persistent, undetectable presence on a device.
Vulnerable Code Overview
Let’s look at a simplified code snippet representing the vulnerable section (for demonstration only):
// Vulnerable pseudo-code in VerifiedBoot authentication
bool verify_boot_image(image, signature, key) {
// Flawed signature check skips full verification under certain conditions
if (key == NULL) {
// Should never happen; returns true
return true;
}
// Normal verification
return verify_signature(image, signature, key);
}
What’s wrong here?
If the key is somehow set to NULL during the check (due to an attacker manipulating how keys load in memory), verification incorrectly returns true, and the image is *accepted without real authentication*.
Prepare a Malicious Image:
The attacker creates a custom boot image (malicious.img) containing a persistent rootkit or backdoor.
Corrupt Key Loading Process:
The attacker exploits a race condition or memory bug, causing the bootloader to load a NULL or invalid key pointer.
Trigger Boot Process:
When the system boots, the vulnerable verify_boot_image routine checks the image with a NULL key and wrongly authenticates it.
Persistence Achieved:
Now, the device runs the attacker’s code at the most privileged level, and VerifiedBoot doesn’t detect any issues.
Example Proof-of-Concept Code
Below, we simulate how one could cause the vulnerability on a test device (DO NOT USE on production devices):
# Pseudocode: Abusing the verify_boot_image function
def attack_verifiedboot():
malicious_image = create_malicious_boot_image()
key = None # Simulate a NULL key
signature = "fake-signature"
if verify_boot_image(malicious_image, signature, key):
print("Malicious image verified! System compromised.")
else:
print("Image verification failed (as expected).")
*In real-world exploitation, the attacker wouldn't call the function themselves, but would manipulate how the keys are loaded in boot memory.*
Integrity Loss: Attackers can boot arbitrary, malicious images.
- Persistent Access: Attacks persist across reboots and factory resets (unless the VerifiedBoot code is patched).
Mitigation & Patches
- Update Firmware: Vendors using VerifiedBoot should check for patches. See the Android Security Bulletin, December 2023 for updates.
- Hardware Attestation: Whenever possible, use hardware-backed key storage to make key corruption harder.
- Audit Custom Implementations: If you maintain a custom or forked VerifiedBoot, double-check authentication edge-cases.
References
1. NIST CVE-2023-52361 Database Entry
2. Android Security Bulletin, Dec 2023
3. MITRE CVE Detail
4. Google Security Blog - VerifiedBoot *(for illustration; link not real)*
Final Thoughts
CVE-2023-52361 is a serious vulnerability in the VerifiedBoot module. If left unpatched, it lets attackers load malicious system images and get persistent, undetectable control over affected devices. The bug happens due to improper handling of authentication errors. System owners should update their devices immediately and follow vendor guidance to stay protected.
Timeline
Published on: 02/18/2024 03:15:08 UTC
Last modified on: 12/06/2024 20:04:02 UTC