In the evolving world of smart devices, the security of their inner workings becomes more crucial every day. One recent vulnerability that’s caught the attention of researchers is CVE-2023-52366. This flaw affects the smart activity recognition modules found in certain IoT and mobile devices, potentially causing the features to act unpredictably – or even crash.
This article breaks down CVE-2023-52366 using simple language, so anyone interested in cyber security, from students to professionals, can understand what’s at stake and how this vulnerability works.
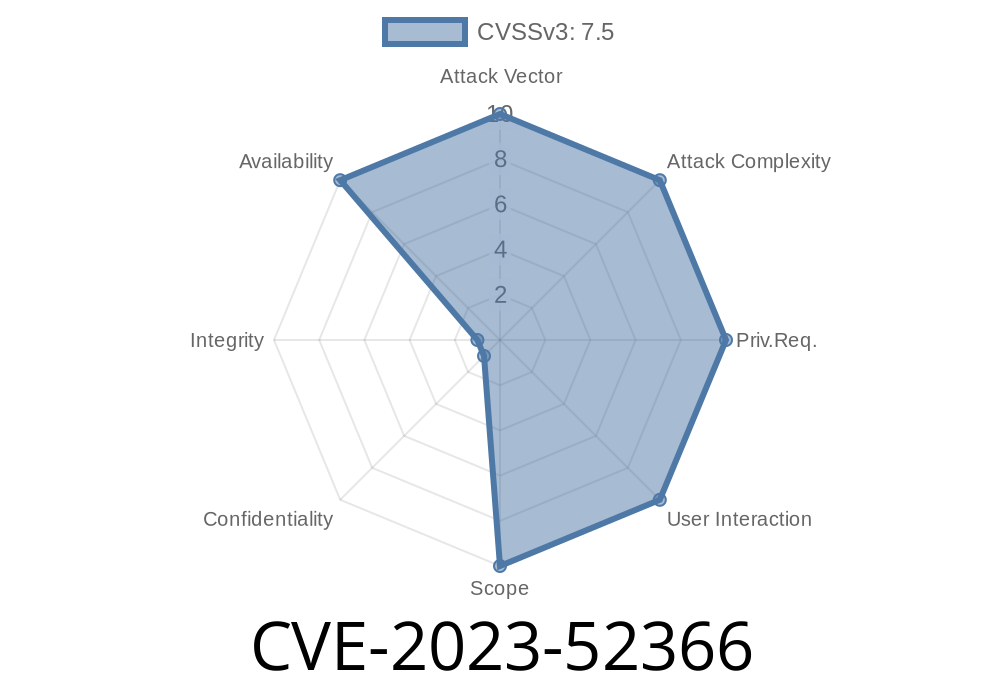
What is CVE-2023-52366?
CVE-2023-52366 is an out-of-bounds read vulnerability found in the smart activity recognition module of certain operating systems and devices. This means the affected code tries to read memory areas outside its assigned buffer. If an attacker crafts a specific input or exploits the system a certain way, the module could leak data, behave oddly, or, in rare cases, cause a device crash.
Why does this matter?
Smart activity modules are used in our phones, watches, and smart home devices to interpret human actions—like steps taken, cycling, or even gesture controls. If compromised, the device’s functionality may be disrupted, or in some cases, private data could be exposed.
Technical Explanation (In Plain English)
An out-of-bounds read typically happens because the software assumes the data it gets will always be the right size or format, but doesn’t properly check. If malicious or malformed data is fed into the module, the software may read memory it isn’t supposed to, sometimes leading to:
Here is a typical pattern of code with such a bug
void process_activities(int *activities, int count) {
int i;
for (i = ; i <= count; i++) { // Oops, should be i < count
printf("Activity ID: %d\n", activities[i]);
}
}
In this code, if count was 5, the loop would actually try to read activities[5], which is outside the valid array (arrays in C are -based). Reading outside these bounds can leak memory contents, cause odd behavior, or crash the program.
Identify the Input Path:
Most smart devices accept sensor data, which is processed by the activity recognition module. If the device lets apps or external sources supply raw activity data, this is a prime attack surface.
Craft a Malicious Input:
For our example, this could be a data packet with more—or specifically crafted—values than expected.
Trigger the Out-of-Bounds Read:
By sending an unexpected array size or malformed data, the attacker tricks the module into reading beyond the intended memory segment.
Suppose we can control values passed to the target function
# Simulated Python logic for demonstration
activities = [1, 2, 3] # expected input
count = 10 # purposely too large
for i in range(count): # will access activities[3] to activities[9] = OOB
print("Activity ID:", activities[i]) # may print garbage or crash
Real-World Risk
- End User: Features such as step counting, gesture controls, or health monitoring may not work right or can become completely unavailable.
- Data Security: Even though out-of-bounds *read* vulnerabilities are less severe than *write*, attackers could still leak sensitive information from memory, depending on what data is processed by the module.
Fixes and Recommendations
The ultimate solution is patching the module with proper input and boundary checks.
Simple Secure Code Example
void process_activities(int *activities, int count) {
int i;
for (i = ; i < count; i++) { // corrected boundary
printf("Activity ID: %d\n", activities[i]);
}
}
Vendors have started rolling out patches—make sure to update your device firmware or software as soon as possible.
References
- CVE-2023-52366 in NVD
- Huawei Security Advisory
- Simple explanation of out-of-bounds vulnerabilities
- How to avoid out-of-bounds in C
Conclusion
CVE-2023-52366 shows how even routine smart features can bring new risks if their code isn’t checked carefully. Developers must use safe programming practices, and users should keep their devices updated. While this particular issue may “only” cause odd device behavior, it’s a real reminder—every component in a smart device network needs to be secured.
Timeline
Published on: 02/18/2024 04:15:07 UTC
Last modified on: 08/22/2024 18:35:04 UTC