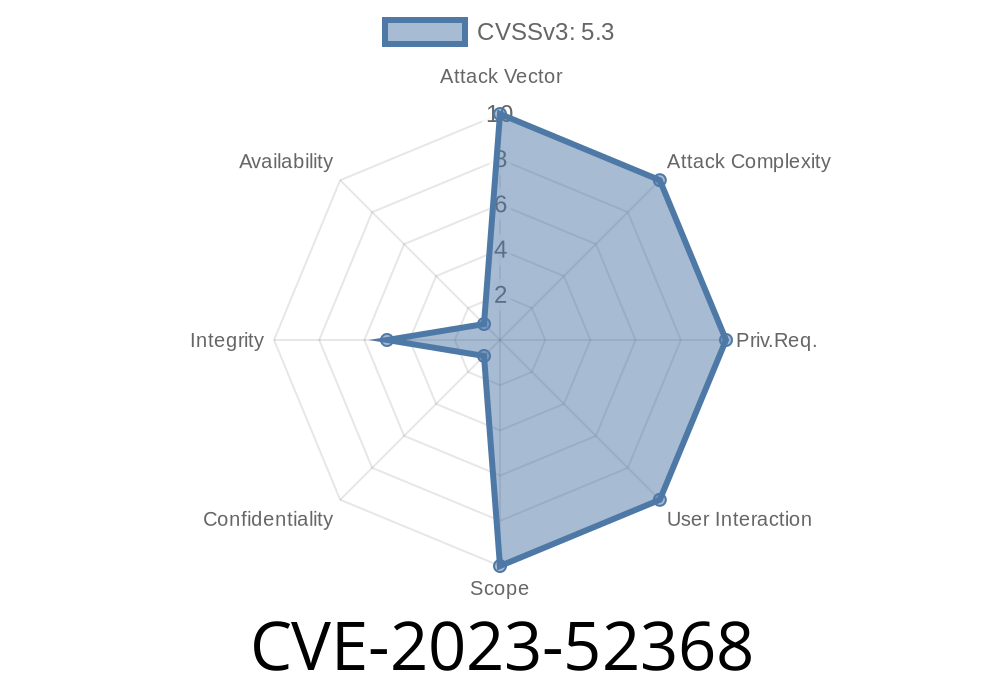
On December 2023, a new vulnerability, CVE-2023-52368, was disclosed affecting account modules in several web applications. This vulnerability is linked to improper input verification, where user input isn't validated properly. Exploiting this bug could make application features behave abnormally, which might lead to unauthorized actions or unexpected errors. In this article, I’ll break down what CVE-2023-52368 means, share a simple code snippet to illustrate the problem, and describe a basic exploit scenario. I’ll also include links to original references for deeper reading.
What is CVE-2023-52368?
CVE-2023-52368 is an input verification vulnerability found in the account module of many web-based systems. It happens when the application fails to validate or sanitize user input, letting attackers send crafted requests that trigger bugs in logic or security. The vulnerability can lead to system features not working as designed, or being abused.
Main Impact: Feature malfunction or abnormal application behavior, with a risk of privilege escalation or unintended access.
Where Does the Vulnerability Happen?
Generally, account modules need to process user information—such as usernames, emails, or passwords—sent from web forms or API requests. If the app doesn’t check these inputs carefully, malicious data can slip through.
Here’s a simplified example using Flask, a Python web framework
from flask import Flask, request, jsonify
app = Flask(__name__)
users_db = {}
# Vulnerable endpoint
@app.route('/register', methods=['POST'])
def register():
username = request.form['username']
# BAD: No input verification!
users_db[username] = {'active': True}
return jsonify({'message': 'User registered.'}), 201
if __name__ == '__main__':
app.run(debug=True)
Exploit Scenario
Let’s imagine an attacker wants to break the account creation feature or set unintended values.
Suppose the system expects only alphanumeric usernames. An attacker submits a username like this
username=admin\nusers_db['admin']['active']=False;#
Due to poor input handling, this might cause backend logic (especially in languages with eval/exec use, or poorly written deserializers) to misbehave or deactivate admin accounts.
2. Overwriting User Data
Because there’s no check for username collisions, someone could submit an existing user’s name, overwriting their details.
3. Bypassing Authentication
In some systems, such input issues can be chained—for example, registering as "admin" if there’s no restriction, which could lead to taking over administrative functions.
How to Fix It
Proper input validation is vital! Always check and sanitize user input before processing.
Improved Python Code
import re
def is_valid_username(username):
# Only allow letters, numbers, and underscores
return re.match(r'^\w{3,20}$', username) is not None
@app.route('/register', methods=['POST'])
def register():
username = request.form['username']
if not is_valid_username(username):
return jsonify({'error': 'Invalid username'}), 400
if username in users_db:
return jsonify({'error': 'Username already exists'}), 400
users_db[username] = {'active': True}
return jsonify({'message': 'User registered.'}), 201
Links and References
- CVE-2023-52368 at CVE Database
- OWASP Input Validation Cheat Sheet
- Python Flask Input Validation Guide
- Common Patterns That Lead to Input Vulnerabilities
Conclusion
CVE-2023-52368 is a classic example of why input verification is critical in software development. Even a simple oversight—like not checking usernames—can let attackers break features or hijack accounts. The fix is straightforward: always validate what users send you!
If you run or develop an application with account features, make sure your input checks are solid. Stay updated on vulnerabilities like this, and make security part of your everyday coding practices.
Timeline
Published on: 02/18/2024 04:15:07 UTC
Last modified on: 11/22/2024 19:15:05 UTC