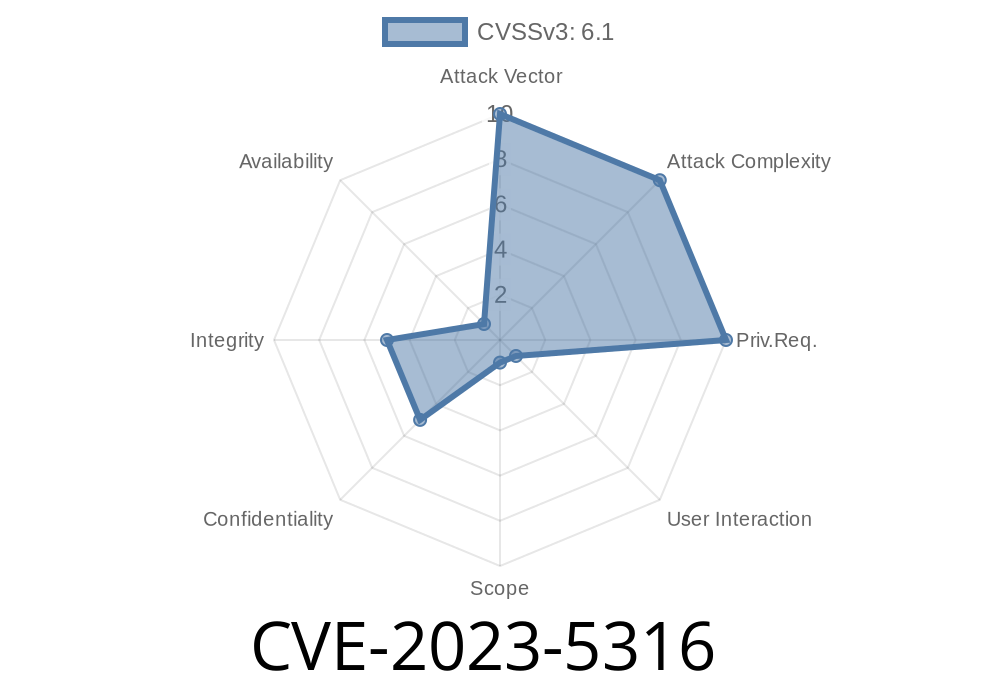
In November 2023, CVE-2023-5316 was disclosed as a DOM-based Cross-site Scripting (XSS) vulnerability in phpMyFAQ, a popular open-source FAQ system. The vulnerability is present in all versions of phpMyFAQ prior to 3.1.18, meaning that if you haven’t upgraded, your instance could be at high risk.
This post breaks down the vulnerability, shows you how it can be exploited, and guides you to secure your system. All information here is written in simple, accessible language.
2. What is DOM-based XSS?
Cross-site scripting (XSS) allows an attacker to inject malicious scripts into web pages viewed by others. DOM-based XSS occurs when the JavaScript code running in the browser processes data from user input (like a URL parameter) without safely handling it, leading to execution of the injected script.
3. About phpMyFAQ
phpMyFAQ is a leading, open-source FAQ system written in PHP. Used by companies and individuals for years, it’s trusted for its flexibility and features, including user management, category management, and more.
4. Vulnerability Details
CVE-2023-5316 affects phpMyFAQ versions before 3.1.18. The application did not properly sanitize user input in the browser’s Document Object Model (DOM), enabling attackers to inject and execute arbitrary JavaScript code.
This is a DOM-based XSS – the exploitation doesn’t depend on any backend logic or database storage. It happens entirely within the browser, making it both sneaky and dangerous.
Where’s the bug?
In affected versions, some components use JavaScript to read user-supplied values from the URL and inject them into the page, like this:
// src/js/frontend/somefile.js (example pattern)
const search = window.location.hash.substring(1);
document.getElementById('output').innerHTML = search;
If a user visits
http://example.com/#<img src=x onerror=alert(1)>
The DOM is updated with unescaped HTML, and JavaScript in that HTML is executed – in this case, alert(1) pops up.
5. Sample Exploit & Proof of Concept (PoC)
Let’s walk through building a simple proof-of-concept for CVE-2023-5316.
Step 1: Find the vulnerable page
Any page using unsanitized user data from the URL in innerHTML or similar methods is susceptible.
Suppose you discovered that the search bar input is read from the hash
http://yourserver/path/#<img src=x onerror=alert(document.cookie)>
When you access this link
http://yourserver/path/#<img src=x onerror=alert(document.cookie)>
If you’re running a vulnerable phpMyFAQ, you’ll see your browser’s alert dialog pop up displaying your document’s cookies.
Example code snippet from server
<!-- Vulnerable HTML template -->
<input type="text" id="searchBox">
<div id="output"></div>
<script>
var hash = window.location.hash.substring(1);
document.getElementById('output').innerHTML = hash; // Vulnerable
</script>
Why is this dangerous?
An attacker might send a crafted URL to an administrator. If the admin is logged in and visits the link, the attacker’s JavaScript can steal session cookies, escalate privileges, or hijack accounts.
6. Mitigation & Patching
The official fix is to upgrade to phpMyFAQ 3.1.18.
This version escapes user input correctly before updating the DOM.
Safe coding example
var hash = window.location.hash.substring(1);
// Safely set the text content without evaluating HTML/JS in user input
document.getElementById('output').textContent = hash;
Or use a sanitizing library such as DOMPurify
import DOMPurify from 'dompurify';
document.getElementById('output').innerHTML = DOMPurify.sanitize(hash);
7. References
- NVD Entry for CVE-2023-5316
- phpMyFAQ GitHub Security Advisory
- phpMyFAQ Release 3.1.18
- DOM-based XSS explained (OWASP)
Final Thoughts:
If you use phpMyFAQ, act fast. XSS vulnerabilities are a major threat and are easy for attackers to exploit. Always sanitize user input and keep third-party software updated, especially in public-facing systems.
Timeline
Published on: 09/30/2023 01:15:00 UTC
Last modified on: 10/02/2023 16:51:00 UTC