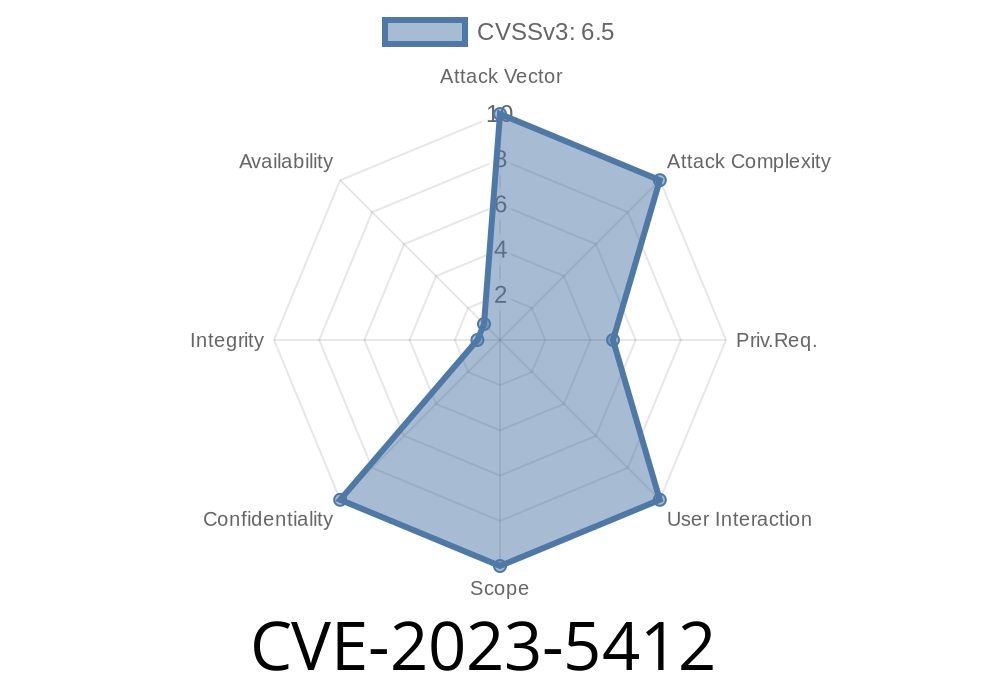
CVE-2023-5412 is a critical security vulnerability discovered in the popular *Image horizontal reel scroll slideshow* WordPress plugin. This issue affects plugin versions up to and including 13.2, and it exposes WordPress websites to dangerous SQL Injection attacks.
If you run this plugin on your website, pay close attention: authenticated users (even with just *subscriber* access!) can leverage this flaw to extract sensitive database information—including user credentials and personal data.
Let’s break down what this vulnerability is, how it works, how it can be exploited, and what you should do now.
What Is the Image Horizontal Reel Scroll Slideshow Plugin?
The plugin on WordPress.org allows WordPress admins to display scrolling image galleries on their websites. It’s a simple, widely used plugin with tens of thousands of downloads.
What Is CVE-2023-5412?
CVE-2023-5412 is a SQL Injection vulnerability. In simple terms, it lets an attacker tamper with SQL queries by submitting malicious input. This is especially dangerous because:
- An attacker can read sensitive info from your database, like usernames, emails, password hashes, etc.
Technical Details: How Does the Exploit Work?
The vulnerability exists because the plugin does not properly sanitize or prepare user input in a shortcode parameter. When an authenticated user adds a specially crafted shortcode to a post or page, this input is plugged directly into a database query. The lack of sanitization lets an attacker inject their own SQL commands.
The plugin processes shortcodes like this
add_shortcode('horizontal-reel-scroll', 'hrss_shortcode_handler');
function hrss_shortcode_handler($atts) {
$album_id = $atts['album'] ?? ;
// BAD: Directly using user-supplied input in SQL query
$results = $wpdb->get_results("SELECT * FROM wp_hrss_images WHERE album_id = $album_id");
// ... rest of the code ...
}
If an attacker sets the album parameter in the shortcode to something like 1 UNION SELECT user_login, user_pass FROM wp_users -- -, the query becomes:
SELECT * FROM wp_hrss_images WHERE album_id = 1 UNION SELECT user_login, user_pass FROM wp_users -- -
Now, it merges image data with user login data, which can expose sensitive information to the attacker.
Proof of Concept (PoC) Exploit
Suppose you have a subscriber account on a vulnerable WordPress site running Image horizontal reel scroll slideshow v13.2 or below.
Insert the following shortcode
[horizontal-reel-scroll album="1 UNION SELECT user_login, user_pass FROM wp_users -- -"]
Preview or publish the post.
5. The plugin executes the malicious query and the attacker can see the usernames and (hashed) passwords of all WordPress users, which may be output on the page depending on plugin behavior.
Extract all usernames, hashed passwords, email addresses, etc.
- Chain this exploit with other vulnerabilities to elevate privileges, deface the site, or even take full control.
Original References & Further Reading
- Wordfence Advisory: https://www.wordfence.com/threat-intel/vulnerabilities/id/95570e85-dd28-444e-b45a-386e4b999c73
- WPScan Advisory: https://wpscan.com/vulnerability/95570e85-dd28-444e-b45a-386e4b999c73
- Plugin page: https://wordpress.org/plugins/image-horizontal-reel-scroll-slideshow/
How To Protect Your Site
1. Update the Plugin: The first step is to update Image horizontal reel scroll slideshow to at least v13.3 or any latest patched version. Check the plugin changelog.
2. Restrict User Roles: Limit who can create posts/pages if you must stay on an older version temporarily.
Audit Your Database: If you suspect exploitation, check logs for suspicious queries and users.
4. Web Application Firewall: Consider adding extra protection with a WAF like Wordfence or Sucuri.
Best Practices For Developers
If you’re a plugin or theme developer, avoid this issue in your own code! Always use proper parameterized queries:
$results = $wpdb->get_results(
$wpdb->prepare("SELECT * FROM wp_hrss_images WHERE album_id = %d", $album_id)
);
Conclusion
CVE-2023-5412 is a serious vulnerability that puts sensitive WordPress data at risk. If you use the Image horizontal reel scroll slideshow plugin, update immediately. This issue is a classic example of why secure coding and constant vigilance are critical in web development.
Timeline
Published on: 10/31/2023 09:15:08 UTC
Last modified on: 11/07/2023 04:23:58 UTC