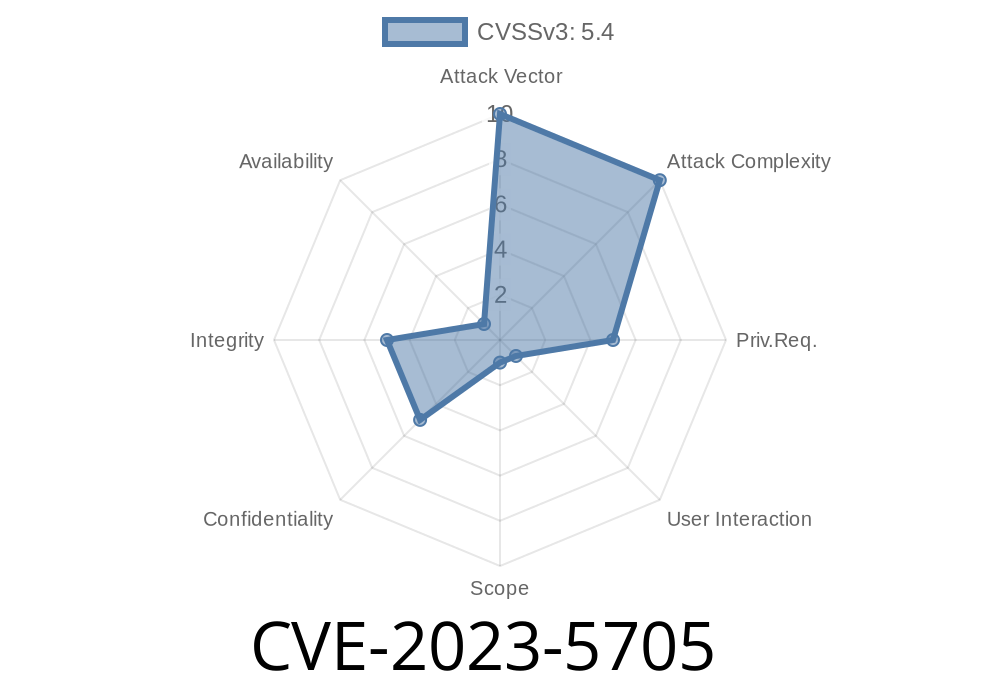
In the ever-growing list of WordPress plugin vulnerabilities, CVE-2023-5705 stands out. This security issue impacts the popular VK Filter Search plugin, used by thousands to add filter functionality to their WordPress sites. The vulnerability allows authenticated users with at least contributor rights to execute Stored Cross-Site Scripting (XSS) attacks—an all-too-common exploit that can lead to session hijacking, phishing scams, defacement, and more.
What Is CVE-2023-5705?
CVE-2023-5705 is classified as a Stored XSS vulnerability in the VK Filter Search WordPress plugin, affecting all versions up to (and including) 2.3.1. The bug comes from the way the plugin's [vk_filter_search] shortcode processes user-supplied attributes. It doesn't properly sanitize or escape inputs, opening the door to malicious code injection.
Attack Surface:
Any site running the vulnerable VK Filter Search plugin, version 2.3.1 or earlier.
Prerequisites:
The attacker must have a WordPress account with at least contributor permissions. By default, contributors can write posts but normally cannot use JavaScript in content. This flaw overrides that control.
Where's the Problem?
The culprit is the plugin's shortcode processing. WordPress lets plugins create shortcodes, which users can add to posts and pages. The VK Filter Search plugin has a [vk_filter_search] shortcode that accepts various attributes.
Here’s a simple sketch of the logic
add_shortcode('vk_filter_search', 'vk_filter_search_shortcode');
function vk_filter_search_shortcode($atts) {
// The plugin does little or no sanitization here!
$label = $atts['label']; // Directly taken from user input
return "<div class='filter-label'>{$label}</div>";
}
If a user sets the label attribute to arbitrary HTML or JavaScript, it will be rendered as-is on the page.
`
[vk_filter_search label=""]
Publish the post
Result:
Every time ANYONE visits this post, the browser executes the JavaScript. Attackers can replace alert() with malicious payloads to steal cookies, deface pages, or inject phishing forms.
On the page HTML, it looks like
<div class='filter-label'>
<script>alert('XSS by CVE-2023-5705');</script>
</div>
Session hijacking: Steal admins' cookies and take control of their accounts
- Malware injection: Insert links/scripts to distribute malware
SEO spam: Fill injected pages with spam links
Critical point:
Attackers only need low-level user access (contributor) to infect the whole front-end.
Immediate Steps
- Upgrade: Update VK Filter Search to the latest version from WordPress.org
- Review: Check your site for unexpected posts/pages or user accounts
Sanitize: For admins, audit all current content for suspicious scripts or shortcodes
Technical Fix:
Plugin developers should sanitize and escape all user input with WordPress functions like esc_html or esc_attr before display:
function vk_filter_search_shortcode($atts) {
$label = isset($atts['label']) ? esc_html($atts['label']) : '';
return "<div class='filter-label'>{$label}</div>";
}
References
- Original Wordfence Advisory
- NVD Entry for CVE-2023-5705
- VK Filter Search at WordPress.org
- OWASP XSS Guide
Conclusion
Even trusted WordPress plugins can introduce serious risks like CVE-2023-5705. A small oversight in sanitizing shortcode attributes led to a vulnerability that makes it trivial for insiders to run malicious scripts. Always keep plugins updated and never trust user input—sanitize and escape!
Protect your site, stay updated, and keep an eye out for these simple, yet powerful vulnerabilities.
Stay secure, <br>YourSite Security Team
Timeline
Published on: 10/27/2023 12:15:08 UTC
Last modified on: 11/07/2023 04:24:18 UTC