---
Introduction
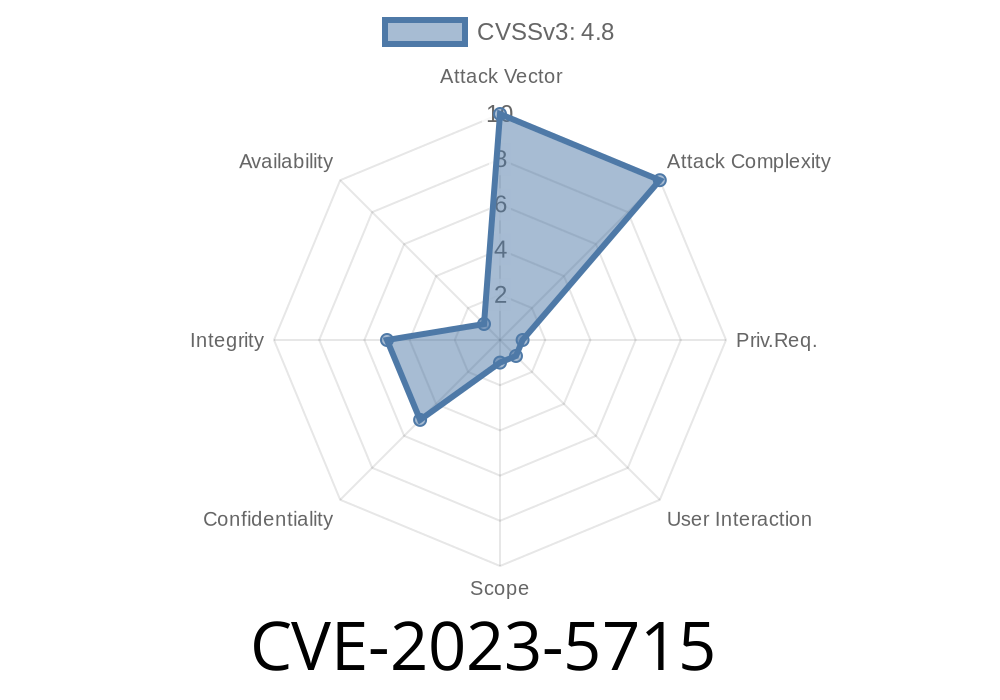
Security is crucial for WordPress websites, especially on multi-site setups where administrators have significant control. Recently, a vulnerability tracked as CVE-2023-5715 was found in the Plerdy Website Optimization plugin for WordPress, affecting versions up to and including 1.3.2. This bug enables authenticated attackers (those with admin access) to inject malicious JavaScript (“stored cross-site scripting” or stored XSS) into other users’ sessions. Let’s dig into what this means, how it happens, and how you can stay protected.
What’s The Problem?
The Plerdy plugin is used for website optimization—collecting clicks, popups, and analytics. However, its tracking code setting (an admin-configured field) isn’t properly sanitized. This means an attacker with admin-level rights could add JavaScript that will execute whenever anyone visits affected pages.
Below is a simple XSS payload that could be used
<script>alert('Your site is vulnerable to XSS!');</script>
An attacker could enter this into Plerdy > Settings > Tracking Code field.
Save changes.
Now, when any user visits the site, their browser runs this code. In the above example, it sends the user’s cookies to a remote server.
Reference Links
- NVD listing for CVE-2023-5715
- Wordfence Advisory
- Plerdy WordPress Plugin
- OWASP: Cross-Site Scripting (XSS)
Why Does “Admin Only” Matter?
You might be thinking: “If only admins can exploit this, what’s the risk?”
Role abuse: Malicious or compromised admin accounts can attack other users on the site.
- Unfiltered HTML disabled: Sometimes, WordPress hosts restrict the ability of admins to post HTML for security. This bug goes around those protection lines.
Update plugin: If you use Plerdy, update beyond version 1.3.2 as soon as a fix is available.
- Monitor user roles: Limit untrusted users from gaining admin or “site manager” rights, especially in multi-site setups.
- Sanitize inputs & outputs: Developers must use escaping functions like esc_html() or esc_js() in all settings fields.
Exclusive Tips
- Audit settings after updates: Sometimes, malicious code may remain after a vulnerable plugin is updated. Clean it out.
Disable plugin if not in use: Prefer native analytics when possible.
- Educate admins: Make sure all site managers understand the risks of custom scripts in tracking fields.
Conclusion
CVE-2023-5715 is a prime example of how even admin-only flaws matter—especially on platforms where not all admins are fully trusted. If you use Plerdy for WordPress, keep your plugin updated, review your user roles, and always be careful with settings that accept arbitrary code. XSS vulnerabilities don’t just threaten security—they can erode user trust in seconds.
Stay aware, stay updated, and help keep the WordPress ecosystem safe.
*This guide is based on analysis of public advisories and simplified for clarity. For more technical details, visit the official CVE entry.*
Timeline
Published on: 11/22/2023 16:15:14 UTC
Last modified on: 11/29/2023 19:50:49 UTC