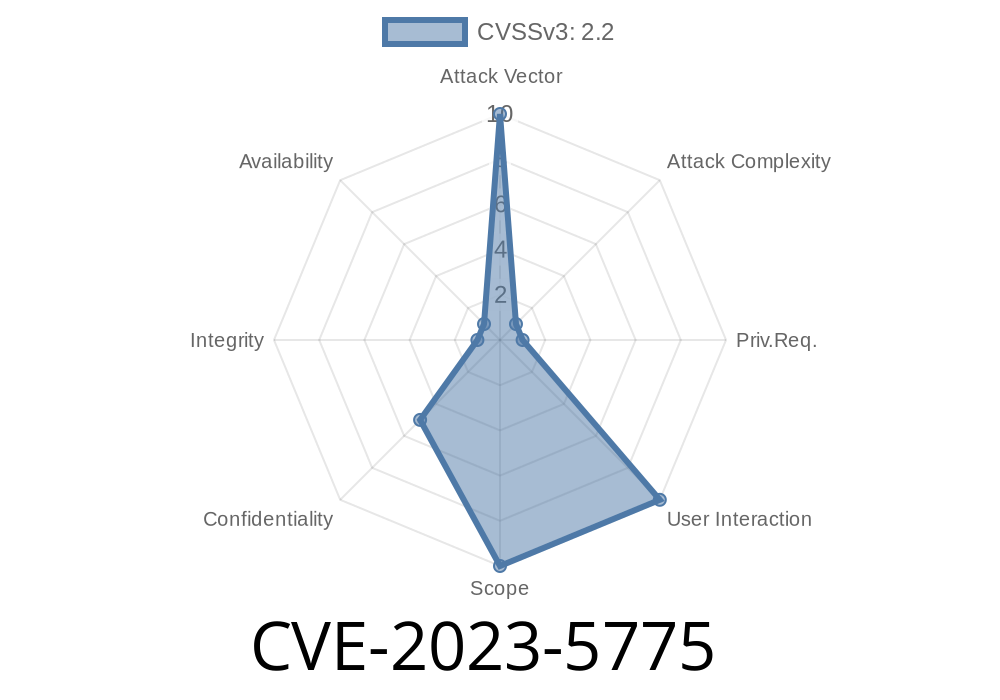
The BackWPup plugin is one of the most popular WordPress backup solutions, installed on hundreds of thousands of websites worldwide. But sometimes, popularity comes at a cost. In October 2023, security researchers disclosed a critical vulnerability tracked as CVE-2023-5775 that affects all BackWPup plugin versions up to and including 4..2. Let’s break down what happened, why it’s risky, and what you should do.
What is CVE-2023-5775?
CVE-2023-5775 refers to a security vulnerability in the BackWPup WordPress plugin. Essentially, the plugin stores backup destination passwords—think Amazon S3, FTP, Dropbox, and other remote backups—in plain text. This plaintext storage means any administrator can directly read or copy these passwords from the WordPress dashboard or, worse, from the database itself.
Why is this bad?
Storing sensitive information like passwords in an unencrypted, human-readable format exposes your website to a higher risk of exploitation, should an attacker gain administrative access.
Who Is Affected?
Any WordPress website running BackWPup versions 4..2 or lower is affected. Since this plugin is often used on busy or business-critical sites, thousands of sites could potentially be leaking sensitive credentials.
Attack Impact and Risk
> If a malicious administrator, plugin, or compromised account with admin rights accesses your site, they could retrieve these credentials—granting instant access to your backups, remote storage, and sensitive data.
The Storage Issue
When you connect BackWPup to remote destinations (like S3 or Dropbox), you must enter your credentials:
// Example of how BackWPup stores the credentials
update_option( 'backwpup_job_dest_s3', array(
'accesskey' => 'AKIAIOSFODNN7EXAMPLE',
'secretkey' => 'wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY'
));
These sensitive values are saved in plaintext in the WordPress database, specifically in the wp_options table. This allows anyone with admin-level access (even if only for a moment) to view, copy, or misuse these details.
Or, they could run a simple query in PHP or MySQL
// PHP code to fetch password from the database
$backwpup_opts = get_option('backwpup_job_dest_s3');
echo $backwpup_opts['secretkey'];
Or using SQL
SELECT option_value FROM wp_options WHERE option_name = 'backwpup_job_dest_s3';
Navigates to BackWPup job settings and copies remote storage credentials.
3. Uses credentials to download, modify, or delete site backups—or attack remote storage directly.
Responsible Disclosure and Fixes
The issue was reported via the WordPress plugin team and further tracked by the NIST National Vulnerability Database:
- CVE-2023-5775 on NVD
- WPScan Advisory
As of March 2024, the BackWPup team released an update (4..3+) resolving this vulnerability by properly masking and optionally encrypting stored credentials. Always check the official release notes for more details.
Change your backup destination passwords or keys after upgrading.
4. Consider running a security audit with a tool like WPScan or Wordfence.
Conclusion
CVE-2023-5775 is a strong reminder that even trusted plugins can introduce risk if sensitive information is not handled correctly. Plaintext storage of passwords is never OK. If you’re using BackWPup, upgrade now, rotate your backup credentials, and keep an eye on your security. Don’t let bad actors get their hands on your site data the easy way.
References
- NVD: CVE-2023-5775
- WPScan Advisory on BackWPup
- BackWPup Official Plugin Page
Timeline
Published on: 02/26/2024 16:27:49 UTC
Last modified on: 02/26/2024 16:32:25 UTC