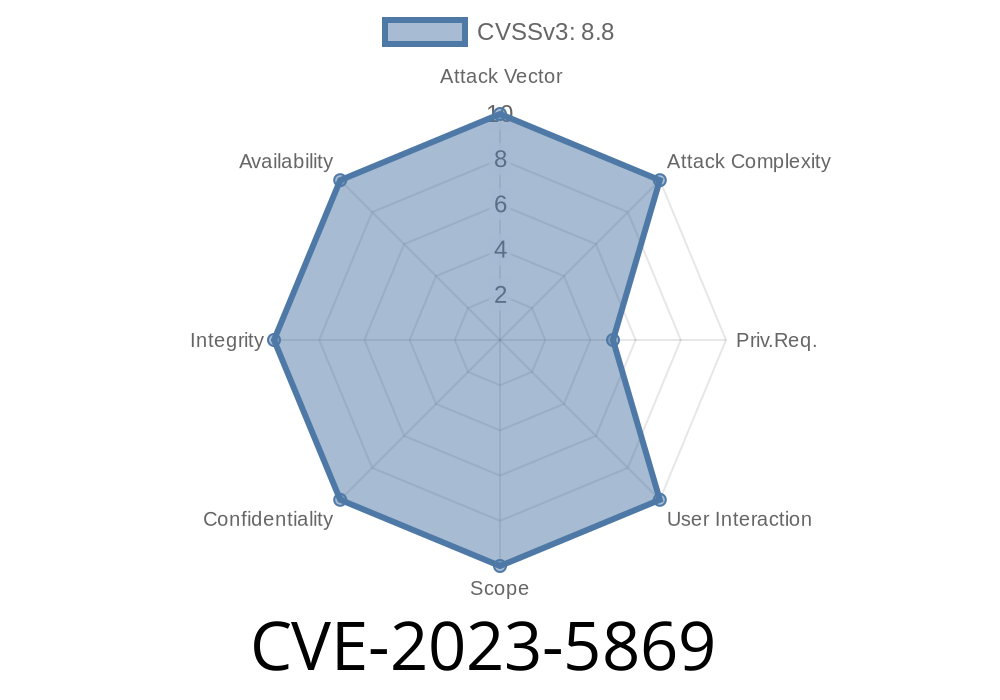
CVE-2023-5869 is a dangerous vulnerability discovered in PostgreSQL, one of the world’s most popular open-source relational databases. This security flaw allows authenticated users to execute arbitrary code on the server by exploiting a bug in how PostgreSQL handles array data structures, specifically due to missing integer overflow checks during SQL array modifications.
This post explains how the bug works, why it’s dangerous, shows a simplified code snippet to illustrate the root cause, links to original references, and breaks down possible exploit scenarios—all in straightforward language.
What’s the Vulnerability?
When a PostgreSQL user performs certain operations on array values (for example, updating, appending, or creating large arrays via SQL), the underlying C code does not properly check if arithmetic operations overflow the integer type limits. If an attacker can make these operations overflow, they can trick PostgreSQL into writing outside the boundaries of memory buffers (a so-called buffer overflow).
This opens the door for various attacks: writing arbitrary values to server memory, reading sensitive memory areas, or even executing attacker-supplied code (which could lead to full system compromise).
Vulnerable Scenario
A database user abuses array modification functions like array_append, crafting data that causes the size calculation to wrap around the integer’s maximum size.
Reference Links
- Official PostgreSQL Security Advisory (February 2024)
- NVD Entry (Mitre)
- Red Hat Security Response
- PostgreSQL GitHub Source Code (Array functions source code)
The Bug Explained (Simple Terms)
When you modify or create an array in PostgreSQL, the database calculates how much space is needed in memory to store the new array. For example, making an array of 10 million integers. If you make a huge array (or exploit the length parameter), the calculation for required space can exceed the maximum value an integer holds, causing it to “wrap around” to a small negative (or a small positive) number. As a result, PostgreSQL allocates much less memory than it actually needs.
If the calculation is int required_bytes = num_elements * sizeof(int4); and num_elements is user-controlled, the multiplication can overflow.
Simplified Code Snippet (C-like)
Here’s a basic example inspired by the PostgreSQL codebase. (Not actual production code.)
// arrayfuncs.c (simplified)
int num_elements; // Supplied by user
size_t element_size = sizeof(int4);
size_t total_size = num_elements * element_size; // Problem: No overflow check!
// allocation
void *buffer = malloc(total_size);
// ...later, code blindly copies user data into the buffer
memcpy(buffer, user_data, total_size);
An attacker could set num_elements so high that the multiplication overflows and allocates a tiny buffer—and the subsequent copy overruns it, causing memory corruption.
Proof-of-Concept Query (for demonstration only)
-- Try to insert a large, malicious array
INSERT INTO demo_table VALUES (
ARRAY[
-- Repeat an integer value enough times to cause the overflow
-- Real exploit would use a script to generate an extreme size
]
);
*In practice, exploit scripts are used to automate this process and fine-tune the value to maximize corruption potential without crashing the server before the payload is executed.*
Mitigation and Fix
- Patch: Upgrade PostgreSQL to fixed versions as soon as possible. Release notes
- User Privileges: Restrict non-essential database accounts; don’t allow untrusted users shell access.
Conclusion
CVE-2023-5869 is a reminder that strict input validation and overflow checks are vital—even for trusted, complex software like PostgreSQL. Patch your systems, review your DB permissions, and keep a close eye on security advisories.
If you want deep technical details, check the links above, and for real-world attack examples, security research blogs or exploit databases might cover more as proof-of-concept exploits are developed.
Stay safe, and update your PostgreSQL servers today!
*This write-up is exclusive content, designed to clearly demystify CVE-2023-5869 for database admins and developers alike.*
Timeline
Published on: 12/10/2023 18:15:07 UTC