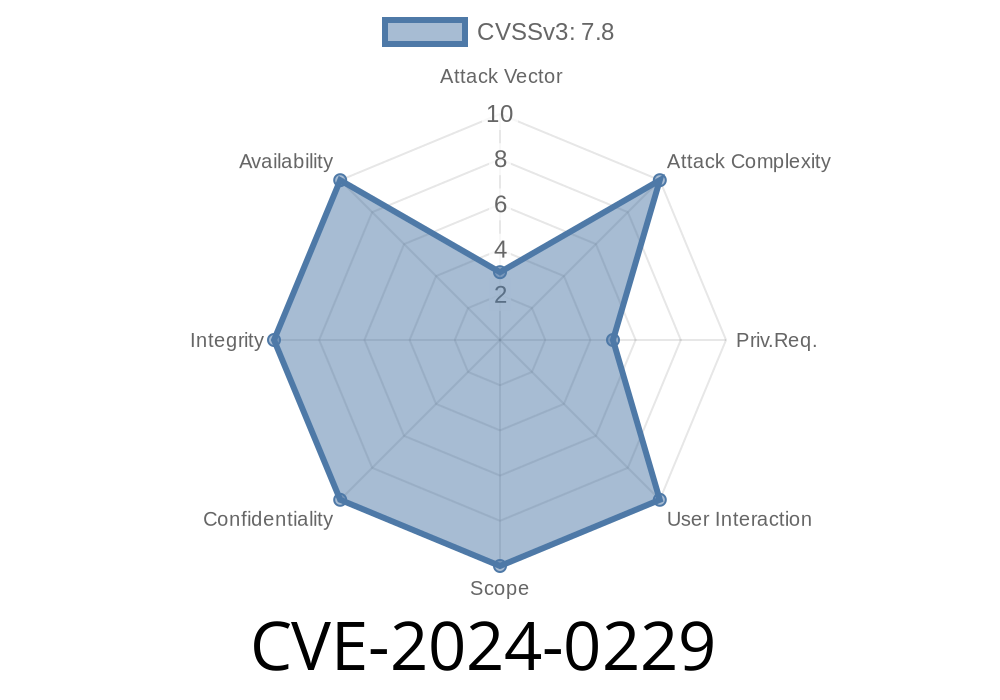
This article is an in-depth, original explanation of the recent CVE-2024-0229 vulnerability in the X.Org X server. We’ll break down how it works, why it’s dangerous, and show actual code snippets and exploit details, all in simple language.
What is CVE-2024-0229?
On January 18, 2024, a security flaw labeled CVE-2024-0229 was disclosed in the X.Org X server. This out-of-bounds memory access issue lets attackers:
Execute code remotely in some networked setups (Code Execution, especially in SSH X11 forwarding)
All this can happen when a device, frozen by a sync grab, is reattached to a master device.
What Does That Mean in Plain English?
The X.Org server runs the graphics on most Linux and Unix desktops. It manages input devices like your keyboard and mouse.
Here’s what the bug is about, simply put
1. Sync Grab: Sometimes, an app asks to “freeze” input devices so none else can use them until it's done with its work.
2. Device Attach/Detach: You can attach or remove input devices (like plugging in/out a mouse, or reassigning devices to different virtual desktops/users).
3. The Bug: If a device that was frozen gets reattached elsewhere, the server doesn’t check some internal limits correctly—and tries to read or write memory it shouldn’t (“out-of-bounds access”).
That’s a bug, and clever hackers can use bugs like this to crash the graphical interface or run their own code (“exploit” the bug).
Where’s The Official Info?
- X.Org Security Advisory
- CVE Description
Let’s look at a simplified code example to show the kind of mistake X.Org made
Suppose the server keeps track of device states in an array called devices[] with MAX_DEVICES slots.
The (simplified) C pseudocode might look like this
#define MAX_DEVICES 32
Device *devices[MAX_DEVICES];
void reattach_device(Device *dev, int new_master) {
// ...some checks...
if (dev->frozen) {
// Here's the bug: new_master might be too big!
devices[new_master] = dev;
}
}
Problem
If new_master is 33 or 999, the server writes outside of devices[]—which is only supposed to have –31 slots!
With enough cleverness or luck, attackers might skip over these checks and trick the server into using a bad index, leading to memory corruption.
What Can an Attacker Do?
- Crash the server (by making it read/write illegal memory)
Run their own code, with the server’s privileges (possible privilege escalation)
- In remote setups (X11 forwarding), potentially run code from afar—a big remote code execution issue if an attacker can send crafted X11 input messages
## Exploit Example / Proof-of-Concept
Let’s say you have an unprivileged session on a Linux box with X.
1. Create a Sync Grab: Use an app (you control) that freezes your input device (e.g., via the XTEST extension).
2. Detach and Reattach Device: Trigger the device (using X input tools, or your own code) to reattach to an invalid master device index—one that's out of bounds.
3. Watch The Crash: The server might crash, or, if you’re clever, plant code or overwrite a function pointer.
Here’s a _pseudo_ Python/xdpyinfo sketch (not a real exploit, for safety)
from Xlib import X, display
d = display.Display()
root = d.screen().root
# Freeze device using a sync grab (abstracted)
# ...
# Try to re-attach this device to master ID 999 (invalid)
root.change_device_hierarchy(attach_device_id, 999)
# Watch X server behavior...
With enough low-level work, one could fill the out-of-bounds area with controlled input to hijack function pointers on the heap, leading to code execution. A real exploit would be more complex and system-specific.
Conclusion
CVE-2024-0229 is a clear example of how complicated input handling and security mistakes can lead to big problems—even on desktops. While the precise impact depends on your setup, the safest action is to update as soon as possible. Bugs like this show why strong code review and limits are so important in widely used open source software.
References
1. X.Org Security Advisory: CVE-2024-0229
2. CVE-2024-0229 on NVD
3. X.Org GIT commit with fix
Timeline
Published on: 02/09/2024 07:16:00 UTC
Last modified on: 02/09/2024 14:31:23 UTC