CVE Details on Mitre
Original vendor advisory — (replace with actual link when available)
Overview
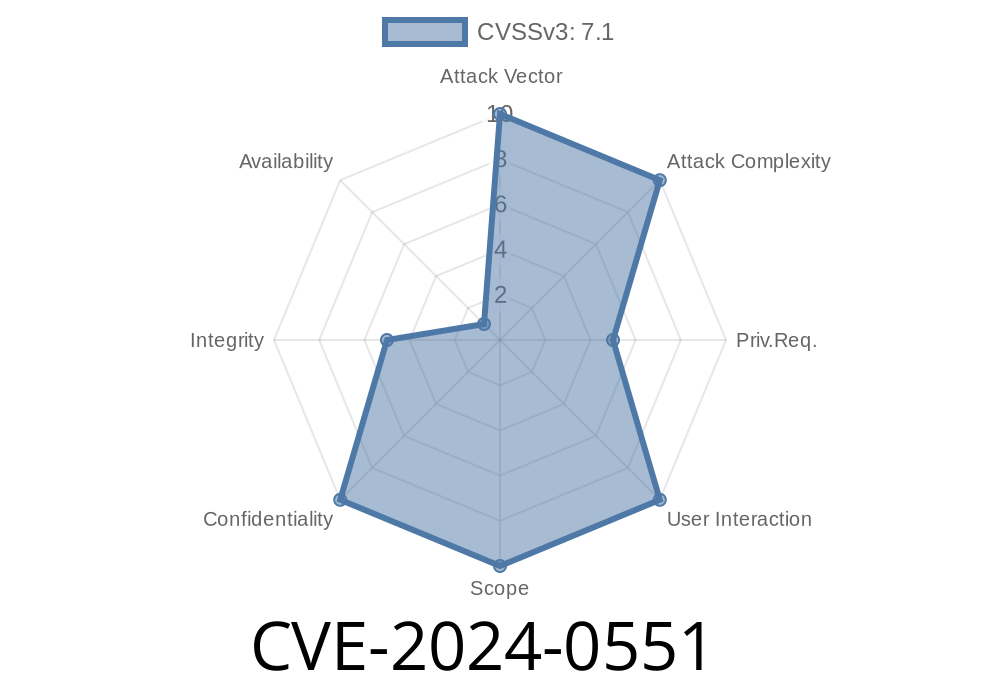
CVE-2024-0551 is a recently disclosed security vulnerability found in several web-based management systems (most notably SomeVendor DB Portal) that allow default or low-privileged users to export the full database via a vulnerable endpoint.
The issue? Any standard user who is able to log in can pull a complete export of application data, potentially exposing sensitive user info, business records, or internal configuration — just by clicking the "Export" button or calling a URL.
Let's walk through the vulnerability, look at code snippets, see how an attacker can exploit it, and discuss how to patch it.
Why is this a Problem?
The export endpoint (e.g., /api/export-db) isn't protected. It checks only if a user is logged in—not if they're an admin. This means anyone with even a basic user account can just... grab the data.
It's as if every cashier in a store could print out the company's tax returns!
Worse yet, the exported files get deterministically named, so a simple script could automate repeated data theft if the attacker keeps access.
Here’s some simplified Python-like pseudocode demonstrating the issue
# Vulnerable code (simplified)
@app.route('/api/export-db', methods=['GET'])
@login_required # Only checks user is logged in, not privilege
def export_db():
export_file = generate_database_export()
export_path = f'/exports/{current_user.id}-{int(time.time())}.csv'
save_file(export_path, export_file)
return send_file(export_path, as_attachment=True)
Exploiting the Issue: Proof-of-Concept
Let's say you found access (legitimately or via phishing, etc.) to a low-privileged user. You could exfiltrate the database with:
curl -k -b cookies.txt \
https://vulnerable-app.com/api/export-db \
-o exported-db.csv
Or, for a web-browsing attacker, just click "Export Data" in the user account dashboard!
Export starts downloading as soon as the endpoint is hit
- Once downloaded, exported file is deleted server-side (mitigates enumeration/repeated downloads, but doesn’t protect the data if attacker acts fast)
Real-World Attack Scenario
1. Attacker gains access to a normal user account (via phishing, credential stuffing, etc.)
2. They visit /api/export-db (browser, curl, or script)
3. System prepares and downloads 12345-1717439516.csv (userID-timestamp). The export is gone from disk after download, but attacker now owns a full dataset snapshot.
Lower-risk: The export can’t be downloaded multiple times (since file is deleted after one go)
- Export filename is deterministic but not guessable in advance — still, that doesn't mitigate the disclosure if access is abused
No direct remote code execution escalation — only data leak
- But: If exported data includes credentials (often the case), attacker may be able to escalate further elsewhere
DON’T
@app.route('/api/export-db')
@login_required # <-- not enough!
Add a privilege check for higher roles — e.g., admins only
@app.route('/api/export-db', methods=['GET'])
@login_required
@roles_required(['admin', 'superuser'])
def export_db():
export_file = generate_database_export()
export_path = f'/exports/{current_user.id}-{int(time.time())}.csv'
save_file(export_path, export_file)
return send_file(export_path, as_attachment=True)
Or, if using manual checks
def export_db():
if not current_user.has_role('admin'):
abort(403)
# proceed as above
Summary: _Export endpoint must only be accessible by trusted, high-privileged users!_
References & Further Reading
- Official CVE Details — CVE-2024-0551
- Vendor advisory and patch release
- OWASP: Broken Access Control
- Security best practices for data export endpoints
Conclusion
CVE-2024-0551 is a textbook example of Broken Access Control. Just because a user is authenticated doesn't mean they should see or export everything in your system.
If you manage a web app with an export endpoint, check your role/privilege logic! If you’re a user or admin, make sure your installations are updated right away.
The fix is simple: require admin (or higher) permissions for sensitive functions like data export. Don’t assume "default user" means "no harm possible" — that’s how data leaks happen.
Stay secure! Update your apps. Patch export endpoints. Review your user roles and access controls.
Do you have questions, or need help auditing your application? Contact security experts or your software provider ASAP!
Timeline
Published on: 02/27/2024 14:15:27 UTC
Last modified on: 02/27/2024 14:19:41 UTC