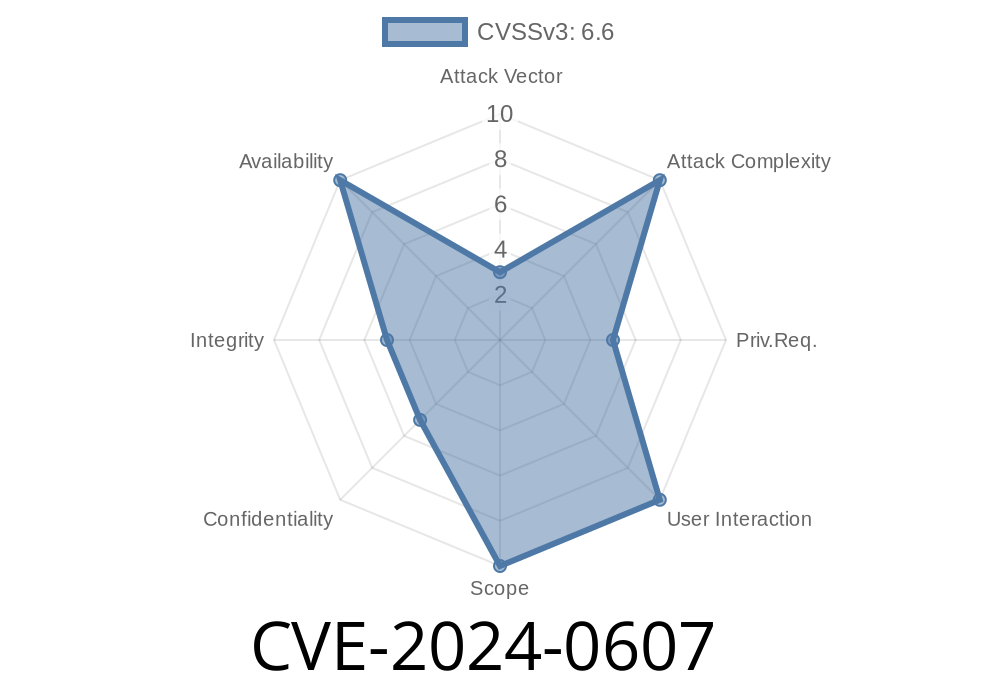
The open-source world trusts the Linux kernel for performance and security. However, CVE-2024-0607 shows how even the smallest coding mistake can cause big, system-wide problems. Netfilter, which powers the Linux firewall and network packet filtering, is affected by this bug. Let's break down what happened, see the problematic code, understand how it can be exploited, and how you can protect your systems.
What Is CVE-2024-0607?
Discovered in early 2024, CVE-2024-0607 affects the Netfilter subsystem in the Linux kernel—specifically the nft_byteorder_eval() function. The bug is caused by a mismatch in data types: it writes 8 bytes at a time to a destination array (dst) of u32, where each element is only 4 bytes. On every loop, the code overwrites and corrupts adjoining memory, which can lead to Denial of Service or break packet filtering.
The Problematic Code
Let's dig into the source. The bug was found in net/netfilter/nft_byteorder.c. Here is a simplified version to illustrate the problem:
// dst is declared as u32 array, so each element is 4 bytes
u32 dst[ARRAY_SIZE];
// src is the source buffer (could be u64 or data from user)
for (i = ; i < len; i += 8) {
// Bug: memcpy writes 8 bytes, but dst[i] only has 4 bytes
memcpy(&dst[i], &src[i], 8);
}
dst expects 4 bytes per element (u32), but memcpy writes 8 bytes at each loop.
- Each 8-byte write overlaps two u32 elements, so after every iteration, some part of dst is overwritten (memory corruption).
- This misalignment leads to memory corruption within the array, which can crash the kernel module or make Netfilter misbehave.
Exploitation: What Could Go Wrong?
An unprivileged local user could trigger this flaw through crafted nftables rules, designed to hit the vulnerable code path. By manipulating data to trigger the byte order conversion, an attacker can corrupt Netfilter's internal memory, potentially:
Proof of Concept (PoC) Example
Here’s a basic (non-destructive) Python-style pseudocode example of what exploitation might look like. (A full exploit would require deep kernel knowledge and actual kernel interface interactions!)
# For illustration only: Shows bug in a user-space simulation
import struct
dst = [] * 8 # Array of u32 (simulate with ints)
src = b'exploit!!' * 2 # 16 bytes of data
for i in range(, 16, 8):
# This should copy 2x u32 at a time,
# but will actually overflow our simulated dst list items
# This is just to illustrate overlapping writes
chunk = src[i:i+8]
dst[i // 4] = struct.unpack('<Q', chunk)[] # Overwrites 64 bits (2 elements)
Original References
- Red Hat Security Advisory
- NVD - National Vulnerability Database
- Linux Kernel Commit Discussion
Conclusion
CVE-2024-0607 in Netfilter reminds us that even “small” programming mismatches—like writing 8 bytes to a 4-byte slot—can have far-reaching, serious consequences. It’s a textbook example of why code reviews, type safety, and rapid patching matter.
Timeline
Published on: 01/18/2024 16:15:08 UTC
Last modified on: 01/26/2024 19:00:06 UTC