---
1. Introduction
Passwords, credit card numbers, secret project notes: you expect all of that to stay locked down in Private Browsing windows and tabs. On Android, many depend on Firefox or Thunderbird to keep that sensitive data under wraps. But if you used private tabs and copied any information to the clipboard, it might have accidentally ended up in your device’s *cloud clipboard history*.
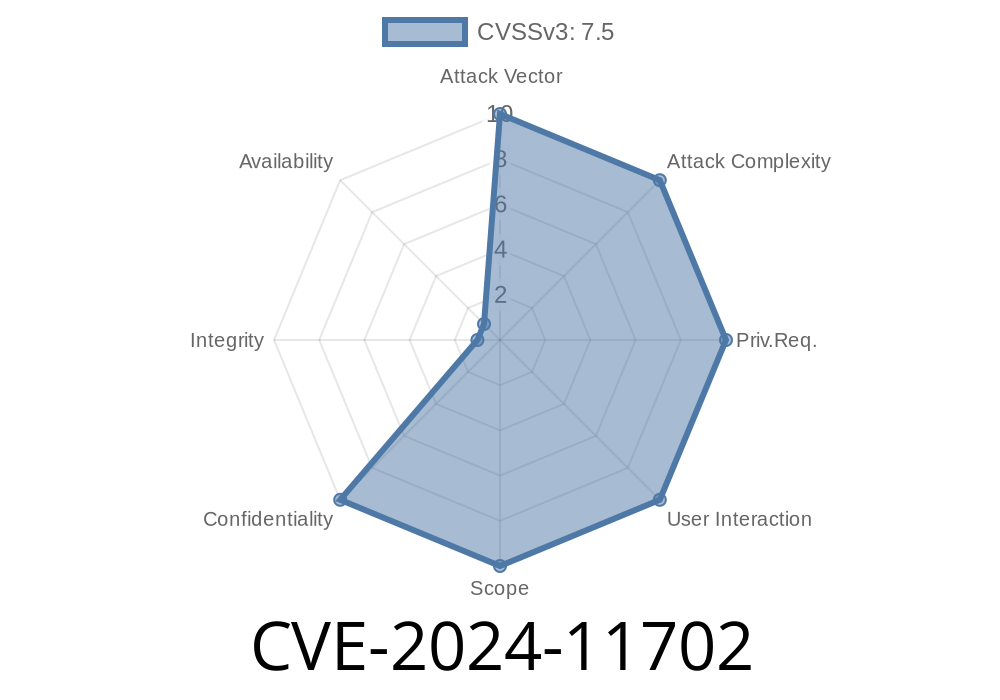
This long-read digs into CVE-2024-11702, a newly disclosed vulnerability that affects Firefox and Thunderbird for Android (before version 133). We'll break down exactly how this privacy fail happened, show how it could be exploited, and tell you what you can do.
2. What is CVE-2024-11702?
CVE-2024-11702 is a security vulnerability that allowed sensitive data copied from Private Browsing windows in Firefox and Thunderbird on Android to be stored outside of your device—without your knowledge. If you used a manufacturer’s “cloud clipboard” feature (such as Samsung, Huawei, or Xiaomi), your passwords copied from a private tab could have been uploaded, synced, and retrievable later.
This bug was fixed in Firefox 133 and Thunderbird 133. If you’re using an older version, your information is at risk.
3. How Did the Vulnerability Work?
Normally, sensitive data copied to your clipboard (using ‘Copy’ in a private tab) should stay as private as possible. But on some Android phones, there’s a built-in *clipboard history* feature that can sync clipboard contents to the cloud, making the last several copied items available across your devices.
The Problem
Private Browsing in Firefox and Thunderbird did not prevent clipboard cloud sync. This means that, for example, if you copied a password from a private tab, it could end up in the synced clipboard history, easily accessible later—even after you closed the tab!
*Why is this bad?*
If someone gains access to your phone or the synced account, they could see sensitive info even after the private tab is closed—breaking the promise of Private Browsing.
4. Exploit Details & Example
Scenario: You’re logging into your bank in a Firefox Private Tab on Android. You copy your password from a password manager, or perhaps from the login page itself, intending to paste into another field.
`javascript
// Example: Copy password in private tab
var pass = "SuperSecretP@sswrd!";
navigator.clipboard.writeText(pass); // This will save the password to clipboard
Your phone’s clipboard service detects the copy event.
3. If cloud clipboard history is enabled (see Samsung, Xiaomi, Huawei docs), the copied password is uploaded to the cloud clipboard storage.
4. Later, on this device or another synced device, *anyone* (with access to your cloud clipboard) could see the copied password, even after the private tab was closed!
Why This Is a Vulnerability
Apps, especially in Private Mode, should explicitly *prevent* clipboard sync or clear the clipboard upon exit. Failing to do so exposes sensitive info not just to users—but to attackers or anyone with device (or cloud) access.
Thunderbird for Android (before v133)
- Devices with cloud clipboard sync/history enabled (Samsung, Xiaomi, Huawei, etc.)
Firefox or Thunderbird on desktop systems
- Users who disabled cloud clipboard/history on their Android devices
Update Immediately:
- Get Firefox for Android
- Get Thunderbird for Android
Review Your Clipboard History:
- Open your clipboard manager/history on your device. Clear any sensitive content.
Turn Off Cloud Clipboard (optional):
- In your device settings, search for “Clipboard” or “Cloud Clipboard” and turn it off. (Samsung guide)
Mozilla Security Advisory (MFSA 2024-19):
https://www.mozilla.org/en-US/security/advisories/mfsa2024-19/
Bugzilla Report:
https://bugzilla.mozilla.org/show_bug.cgi?id=1877352
Official CVE Info:
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-11702
How to Use Clipboard History on Android:
https://www.howtogeek.com/708934/how-to-use-the-clipboard-on-android/
Cloud Clipboard settings (Samsung):
https://doc.samsungmobile.com/SM-G970F/BTU/doc.html
Final Thoughts
Privacy in Private Browsing should be absolute. CVE-2024-11702 is a strong reminder that software, hardware, and cloud integrations can have unexpected consequences. If you’re using Firefox or Thunderbird on Android—update as soon as you can and review your clipboard practices.
Timeline
Published on: 11/26/2024 14:15:19 UTC
Last modified on: 11/27/2024 16:15:13 UTC