A serious vulnerability (CVE-2024-12362) was recently discovered in InvoicePlane, a popular open-source invoicing tool used by small businesses across the globe. If you use InvoicePlane up to version 1.6.1, your instance is likely affected. This issue relates to a path traversal flaw that allows remote attackers to download sensitive files from your server. In this post, we break down how the vulnerability works, show you what the exploit looks like, and explain how to fix the problem.
Understanding the Vulnerability
Vulnerability Type: Path Traversal
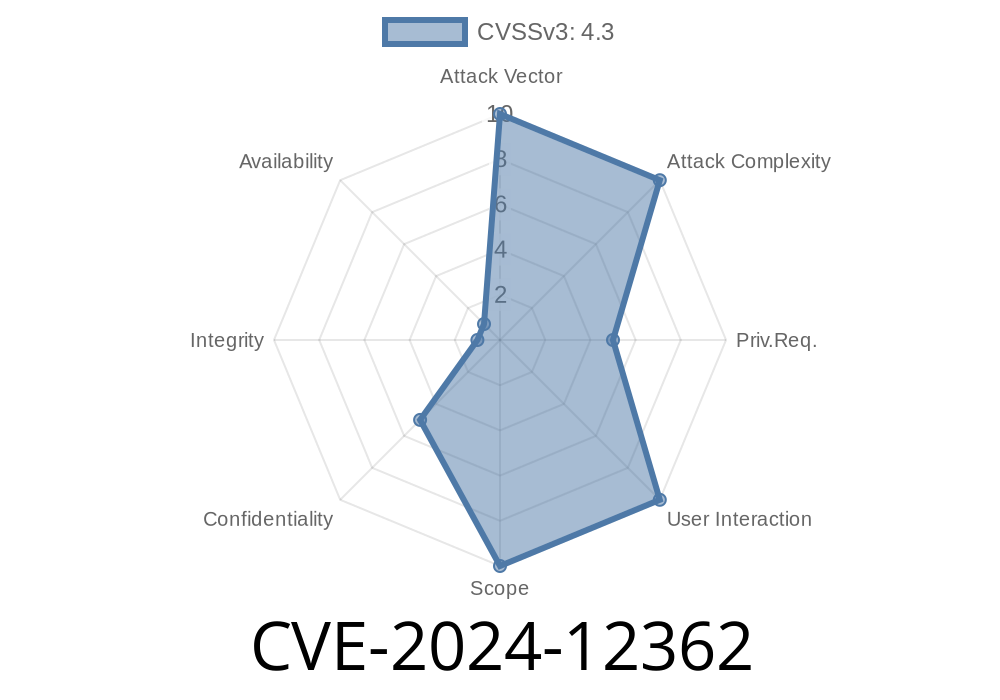
CVE ID: CVE-2024-12362
Affected Versions: InvoicePlane ≤ 1.6.1
Component: invoices.php
Function: download
Attack Vector: Remote, no authentication required
Fixed In: 1.6.2-beta-1
Severity: Problematic (can lead to sensitive data disclosure)
What is Path Traversal?
Path traversal is a security flaw where user input can manipulate file paths, allowing attackers to access files outside the intended directories. By tricking web apps to process special characters like ../, attackers can "climb" directories on the server—potentially accessing secrets such as configuration files, credentials, or other sensitive data.
Exploiting CVE-2024-12362
The vulnerable code allows user input from the invoice argument in a download function of invoices.php to be used *directly* in file paths, without proper sanitization.
Example Vulnerable Code Snippet
// File: application/modules/invoices/controllers/invoices.php
public function download($invoice = NULL)
{
$invoice_file = FCPATH . '/uploads/invoices/' . $invoice . '.pdf';
if (file_exists($invoice_file)) {
// Serve the file
readfile($invoice_file);
}
}
Notice how $invoice is used directly to construct a file path? This is the mistake: if $invoice contains ../../../etc/passwd, the code will try to serve /etc/passwd.pdf!
In the wild, an attacker could craft a URL like this
http://your-invoiceplane-site/index.php/invoices/download/../../../etc/passwd
This would make the application try to serve /etc/passwd.pdf from the server's filesystem—a classic *path traversal*.
Curl Example
curl "http://your-invoiceplane-site/index.php/invoices/download/../../../etc/passwd"
If successful, the attacker would see the contents of /etc/passwd.pdf (if it exists) or even other sensitive files depending on the file extension trick.
#### Detailed Exploit Disclosure
> Note: The success of the exploit can depend on server configuration and file presence.
How Did the Vendor Respond?
The InvoicePlane maintainers responded *impressively quickly* after being notified. A fix was released as version 1.6.2-beta-1 with improved file sanitization.
Upgrade InvoicePlane to at least 1.6.2-beta-1.
Download the official release from GitHub.
Safe Code Example
public function download($invoice = NULL)
{
// Allow only alphanumeric values
if (!preg_match('/^[a-zA-Z-9_-]+$/', $invoice)) {
show_error('Invalid filename.', 400);
return;
}
$invoice_file = FCPATH . '/uploads/invoices/' . $invoice . '.pdf';
if (file_exists($invoice_file)) {
readfile($invoice_file);
}
}
Resources & References
- Official CVE record: CVE-2024-12362
- InvoicePlane Release: 1.6.2-beta-1
- Path Traversal Background: OWASP Path Traversal Cheat Sheet
- InvoicePlane Security GitHub Issues
Conclusion
CVE-2024-12362 is a textbook case of how a little missing input validation can result in a big security hole. If you run InvoicePlane any version up to and including 1.6.1, you should patch to 1.6.2-beta-1 *right now* (or the latest available stable) to close this path traversal issue. Kudos to the InvoicePlane team for their fast response.
Stay safe. Patch often. And never trust user input!
*Found this useful? Share it with your IT friends and help keep the web safer!*
Timeline
Published on: 12/16/2024 10:15:05 UTC