Published: June 2024 <br>Severity: High
What’s CVE-2024-12692?
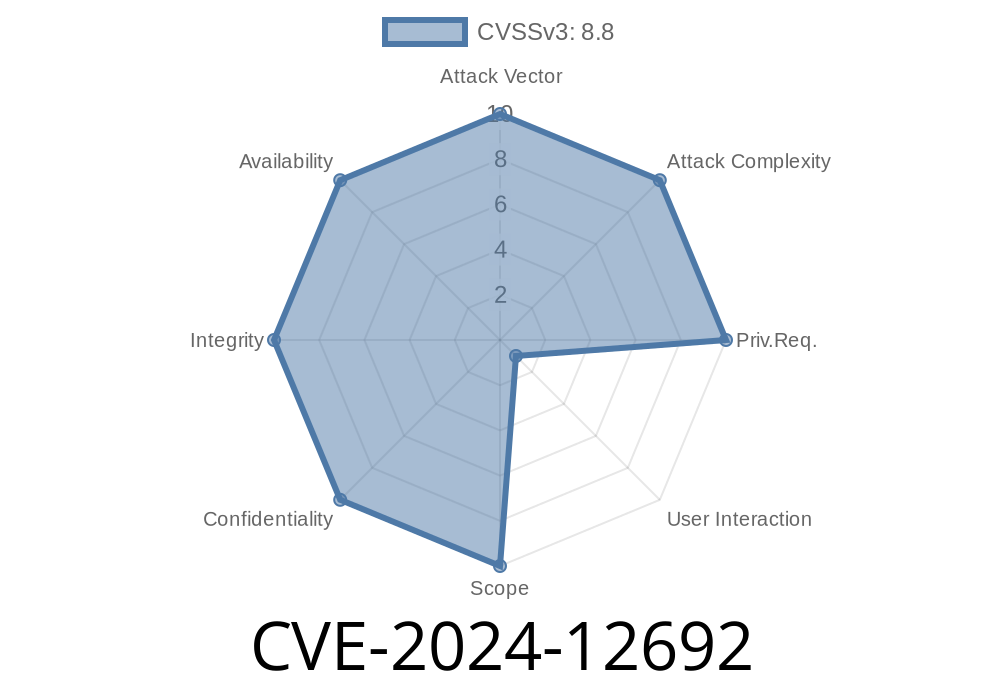
CVE-2024-12692 is a serious security flaw found in the V8 JavaScript engine that Google Chrome uses. Before version 131..6778.204, attackers could use this bug to corrupt memory in your browser by tricking you into opening a malicious HTML page. This is called "heap corruption" and, in the worst case, it could let hackers run code on your system—just from visiting the wrong website.
Google tagged this as high severity and recommends updating Chrome *right away*.
Type Confusion — What Does That Mean?
A "type confusion" happens when code expects a certain kind of data (say, an integer) but actually gets something else (like an object). This confuses the program and can let attackers read or write bits of memory they should never touch.
Chrome’s V8 engine tries to run JavaScript super fast. But if it gets confused about what type it’s working with, bad things can happen, leading to memory corruption and, possibly, arbitrary code execution.
How Attackers Exploit CVE-2024-12692
A hacker makes a custom HTML/JavaScript file. If you open it (maybe from a sketchy link), their code hits the V8 engine’s bug and causes memory problems. Modern browser security makes this tricky but not impossible! This kind of bug is often chained with other exploits to fully take over your system.
Say you have the following vulnerable V8 logic
function triggerTypeConfusion(arr, idx) {
// arr is expected to be of type "Array"
arr[idx] = 1234;
}
// But arr is actually a 'TypedArrayView' (like Uint32Array)
let typedArray = new Uint32Array(10);
// Under certain conditions, V8 can get confused and treat a TypedArray like a generic JS Array
triggerTypeConfusion(typedArray, );
If the engine expects a JavaScript Array, but gets a TypedArray, and then optimizes the code, it may overstep bounds or corrupt the heap. In V8’s inner code, such tiny mistakes can create big security holes!
Proof-of-Concept (PoC) & Exploit Sketch
Because this is an active, dangerous bug, security folks avoid posting working exploits. But here’s what a real attack would do in broad strokes:
Execute payload: Hijack the process to run attack code.
Note: Real exploits are much more complicated. For technical deep-dives, see the reference links!
Patched: Version 131..6778.204 (released June 2024)
- Impacted: Chrome before 131..6778.204, possibly also Edge, Brave, Opera (check patches!)
How To Stay Safe
- Update Chrome: Visit chrome://settings/help to force an update.
References & Technical Details
- Chromium Bug Tracker — Issue 330248360
- V8 GitHub Repo
- Google Chrome Releases Blog
- CVE Details for CVE-2024-12692
Final Thoughts
Memory safety bugs like CVE-2024-12692 are why browser updates matter. Any time a browser (or other big software) engine gets a critical patch, install it right away—even if the update seems small. Type confusion vulnerabilities have a nasty history of being weaponized in-the-wild.
Protect yourself: update, don’t click suspicious links, and don’t ignore warning banners from your browser!
Stay safe,
*Your friendly neighborhood security writer*
Timeline
Published on: 12/18/2024 22:15:05 UTC
Last modified on: 01/07/2025 16:15:32 UTC